
[ad_1]
Electronic Arts Fixed a vulnerability in its Origin online gaming platform after security researchers discovered that they could make an unsuspecting player remotely execute malicious code on his computer.
The bug affected Windows users with the installed Origin application. Tens of millions of players use the Origin app to buy, access and download games. To facilitate access to the store an individual game from the Web, the customer has its own URL system that allows players to open the application and load a game from a webpage by clicking on a link with origin:// in the address.
But two security researchers, Bee daley and Dominik Penner of Underdog Security, discovered that the application could be brought to run any application on the computer of the victim.
"An attacker could have done anything he wanted," Bee told TechCrunch.
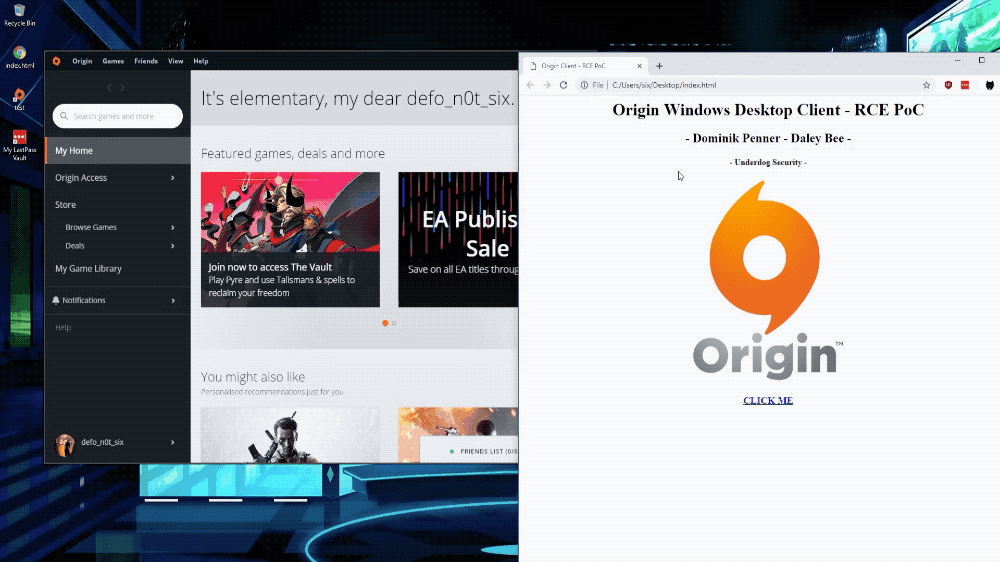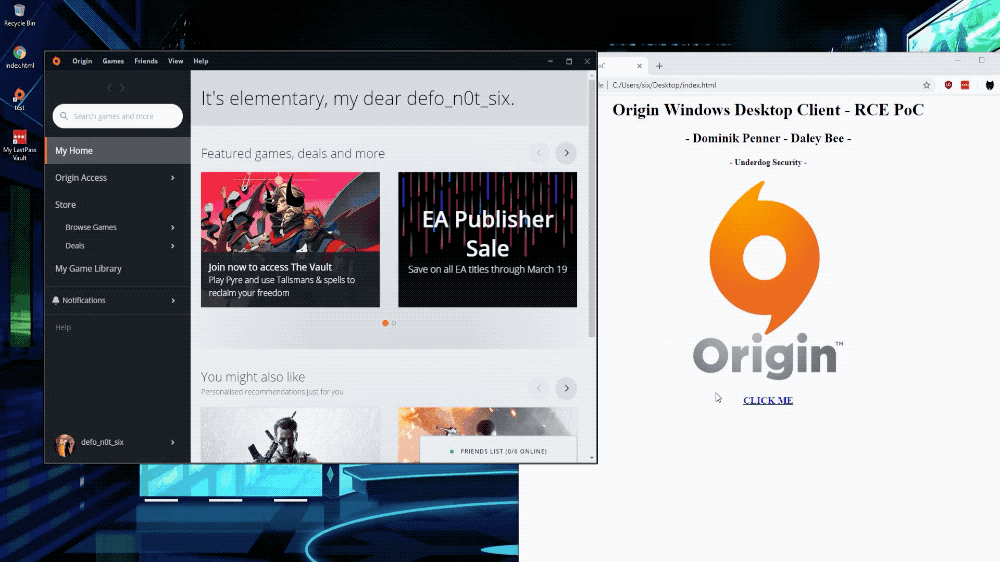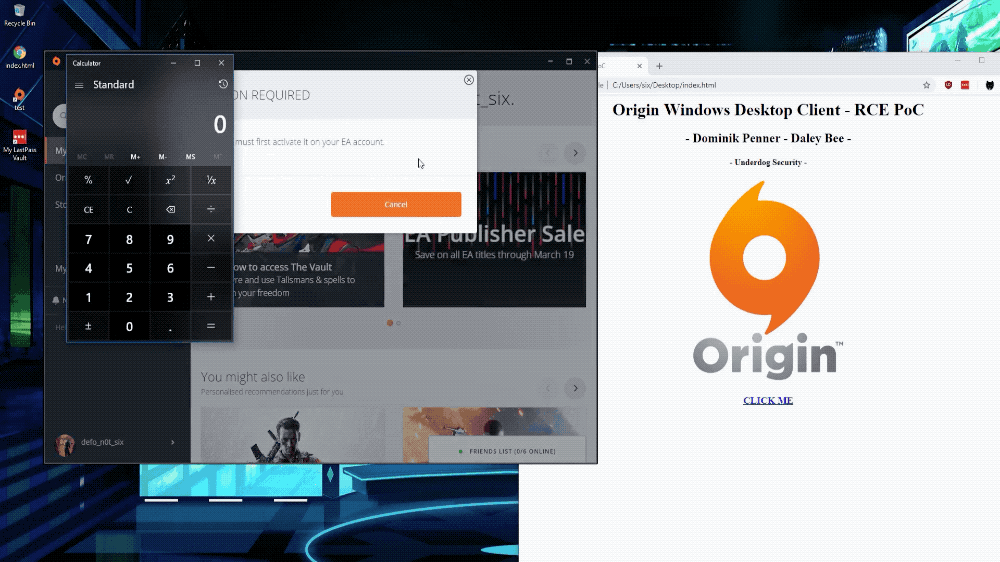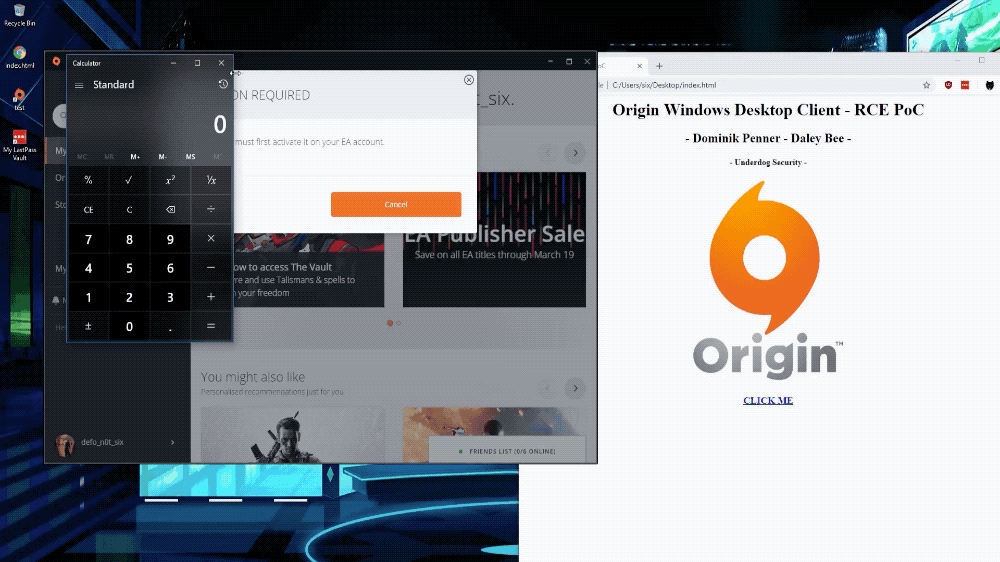
'Popping calc' to illustrate a remote code execution bug in Origin. (Image: provided)
The researchers provided TechCrunch with a proof of concept code to test the bug. The code allowed any application to run with the same level of privileges as the logged-on user. In this case, the researchers opened the Windows Calculator, the must-have application that allows hackers to show they can execute code remotely on an affected computer.
Even worse, a hacker could send malicious PowerShell commands, an embedded application often used by attackers to download additional malicious components and install ransomware.
According to Bee, a malicious link could be sent as an email or listed on a web page, but could also be triggered if the malicious code was combined with an intersite scripting exploit automatically executed in the browser.
It was also possible to steal the access token from a user's account using a single line of code, thus allowing a hacker to access a user's account without the need of his password.
The original macOS client was not affected by the bug.
EA spokesman John Reseburg confirmed that a fix had been put in place on Monday. TechCrunch confirmed that the code was no longer working after the update.
[ad_2]
Source link