[ad_1]

A new "zero day" vulnerability has been revealed. It could allow attackers to hijack existing remote desktop services sessions in order to access a computer.
The flaw can be exploited to bypass the lock screen of a Windows machine, even though two-factor authentication mechanisms (2FAs) such as Duo Security MFA are used. Other login banners that an organization can configure are also ignored.
It should not happen that way
The problem is now tracked as CVE-2019-9510 and is described as an authentication bypass using an alternative path or channel.
Today, an opinion from the CERT Coordination Center of Carnegie Mellon University's Institute of Software Engineering (SEI) warns that session locking may behave unexpectedly on the latest Windows systems where desktop sessions to distance use NLA.
Even if a user specifically locks a Windows computer during an RDP session, if the session is temporarily disconnected, automatic reconnection restores the session to an unlocked state, "regardless of how the remote system was left." This applies to Windows 10 from version 1803 and server 2019 or later.
Will Dormann, a vulnerability analyst at CERT / CC, describes the following attack scenario:
1. The user connects to the remote system Windows 10 1803 or Server 2019 or later using RDP.
2. The user locks the remote desktop session.
3. The user leaves the physical neighborhood of the system used as the RDP client
An attacker could then break the RDP client's network connection, which will cause it to automatically reconnect and bypass the Windows screen lock. This could then allow a local attacker to access the unlocked computer at the end of the Remote Desktop session.
By interrupting the network connectivity of a system, an attacker with access to a system that is used as a Windows RDP client can access a connected remote system regardless of whether the remote system is locked.
Dormann explained to BleepingComputer that "it's not really likely to be exploited in the wild, but it's definitely an unexpected behavior."
CVE-2019-9510 was discovered by Joe Tammariello of the SEI of Carnegie Mellon University. He received a severity score of 4.6 out of 10.
Microsoft was notified of the problem on April 19 and responded by saying that "the behavior does not meet the Microsoft Security Servicing criteria for Windows". Below the complete statement:
After studying this scenario, we determined that this issue does not meet the criteria for Microsoft Security Service for Windows. What you are observing is Windows Server 2019 complying with Network Level Authentication (NLA). Network-level authentication requires users created to allow the connection to continue during the first phase of the connection. These same credits are used to connect the user to a session (or reconnect). As long as it is connected, the client caches the credentials used for connection and reuses them when it needs to reconnect automatically (in order to bypass the NLA).
The attenuation of BlueKeep is always good
When details about BlueKeep (CVE-2019-0708) were released, Microsoft said that activating the NLA would act as a mitigating factor against "deworming" malware that could exploit this vulnerability.
The temporary solution is based on the fact that the NLA requires authentication before triggering the vulnerability. Therefore, the attacker would need valid identification information to access the vulnerable system.
Even though CVE-2019-9510 changes the behavior of the NLA, this effect is not visible on the systems impacted by BlueKeep (Windows 7 and Server 2008). NLA remains a reliable security element. This vulnerability is anomalous and administrators should be aware of this result on newer versions of Windows.
BlueKeep is a serious vulnerability that could lead to remote code execution on the Windows operating system. This affects remote desktop services and makes it attractive for deploying malware that can be de-wormed.
Security researchers have developed a conceptual validation code. Cyber criminals should not be far behind, there are about a million vulnerable systems at BlueKeep, and Web search for them continues to intensify.
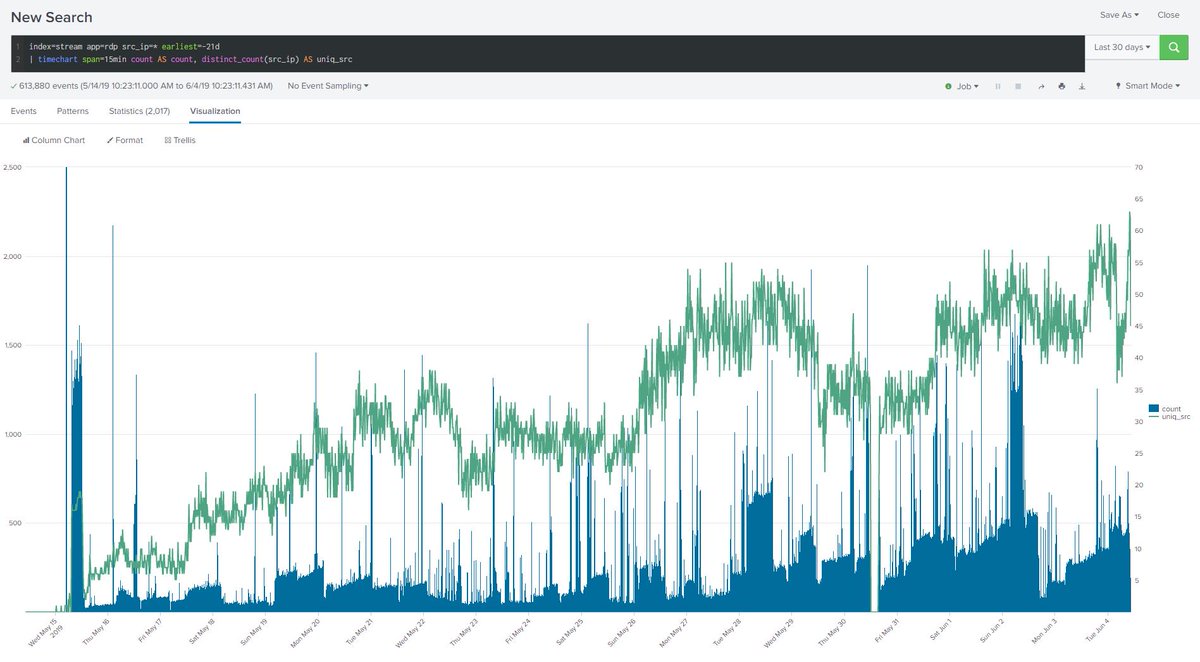
Statistics collected from a RDP jar of honey controlled by a security researcher Daniel Gallagher show an upward trend in analyzes of computers vulnerable to BlueKeep.
[ad_2]
Source link