
[ad_1]

Criminals in 2017 managed to get an advanced backdoor preinstalled on Android devices before leaving manufacturers' factories, Google researchers said Thursday.
Triada appeared for the first time in 2016 in articles published by Kaspersky here and here. The first of them said that the malware was "one of the most advanced mobile trojans" ever met by security company analysts. Once installed, the primary purpose of Triada was to install applications that could be used to send spam and display advertisements. He used an impressive set of tools, including rooting exploits bypassing Android's built-in security protections and ways to modify the almighty Zygote process of the Android operating system. This meant that the malware could directly affect each installed application. Triada is also connected to no less than 17 command and control servers.
In July 2017, the security company Dr. Web announced that its researchers had discovered that Triada was integrated into the firmware of several Android devices, including the Leagoo M5 Plus, Leagoo M8, Nomu S10 and Nomu S20. Attackers used the backdoor to download and install clandestine modules. Because the backdoor is built into one of the operating system libraries and located in the system section, it could not be removed using standard methods, the report says.
On Thursday, Google confirmed Mr. Web's report, although he did not name the manufacturers. Thursday's report also indicated that the supply chain attack was triggered by one or more partners that the manufacturers used to prepare the final firmware image used in the affected devices. Lukasz Siewierski, a member of Google's Google Security and Privacy team, wrote:
Triada infects the camera system images by a third party during the production process. Sometimes OEMs want to include features that are not part of the Android Open Source project, such as unlocking the face. The OEM can partner with a third party to develop the desired feature and send the entire system image to that vendor for development.
Based on the analysis, we believe that a vendor using the names Yehuo or Blazefire has infected the system image returned with Triada.
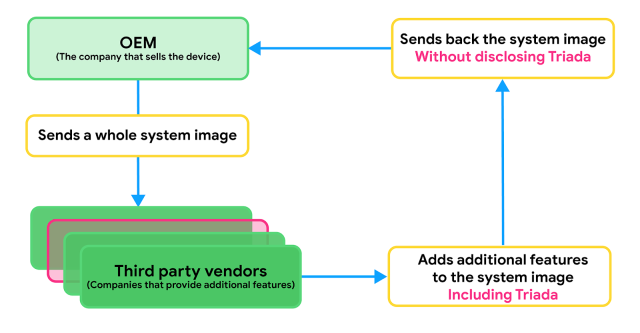
Thursday's post also developed the previous analysis of the features that made Triada so sophisticated. On the one hand, he used XOR coding and ZIP files to encrypt communications. And for another, he injected code into the system UI application that allowed the display of ads. The backdoor also injected code allowing it to use the Google Play app to download and install applications chosen by the attackers.
"The applications have been downloaded from the C & C server and the communication with C & C has been encrypted using the same custom encryption routine using dual XOR and zip," wrote Siewierski. "The downloaded and installed apps used the unpopular app package names available on Google Play, and they had no link to Google Play apps, except for the same package name."
Mike Cramp, senior security researcher at mobile security provider Zimperium, confirmed the assessments that Triada's capabilities had been advanced.
"At first glance, Triada seems to be a relatively advanced malicious program, including control and management features and, in the beginning, shell-running features," writes Cramp in an email. "We see a lot of adware, but Triada is different in that it uses C & C and other techniques that we would usually see more in malware. Yes, all of this is used to run ads But it's more sophisticated than most advertising campaigns – it's almost a "steroid adware". "
Siewierski said Triada's developers resorted to the supply chain attack after Google implemented measures to push back the backdoor. One was the mitigation measures that were preventing its rooting mechanisms from working. Another step was to improve Google Play Protect, which allowed the company to remotely disinfect compromised phones.
The Triada version preinstalled at one point in 2017 did not contain the rooting features. The new version has been "discreetly included in the system image as a third-party code for additional features requested by OEMs". Since then, Google has been working with manufacturers to ensure the removal of the malicious application of the firmware image.
Not the first time
Last year, Google set up a program requiring manufacturers to submit new or updated version images to a suite of version tests.
"One of these security tests analyzes preinstalled PHAs [potentially harmful applications] included in the image system ", wrote Google officials in their report on the Android Security & Privacy 2018:" If we identify a PHA in the build, we work with the OEM partner to fix it and delete it before it is possible. be offered to users. "
Nevertheless, Thursday's report acknowledges that while Google is strengthening security in one area, attackers will certainly adapt by exploiting new weaknesses.
"The Triada case is a good example of how Android malware writers become more skilled," wrote Siewierski. "This case also shows that it is harder to infect Android devices, especially if the malicious program's author needs elevation of privilege."
[ad_2]
Source link