[ad_1]
Communication giant T Mobile said today that it is investigating the extent of a breach that hackers say exposed sensitive personal data on 100 million T-Mobile USA customers, in many cases including name, social security number, address, date of birth, phone number, security PINs and details that uniquely identify each customer’s mobile device.
On Sunday, Vice.com announced that someone was selling data on 100 million people and that the data came from T-Mobile. In a statement posted to its website today, the company confirmed it had suffered an intrusion involving “certain data from T-Mobile,” but said it was too early in its investigation to know what was stolen and how many customers could be affected.
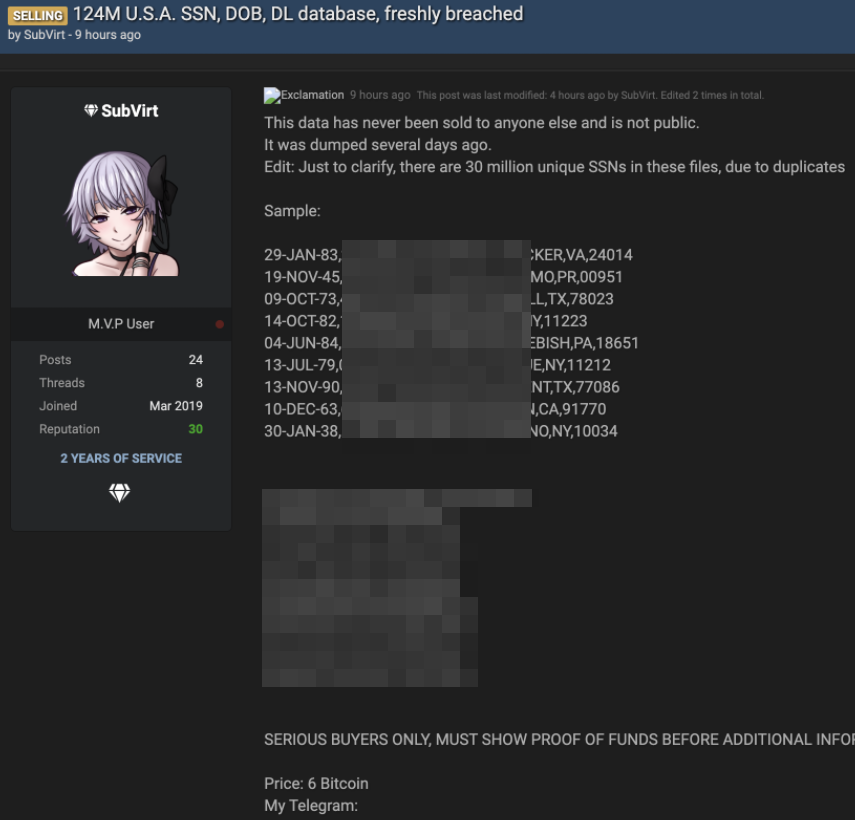
A sales thread related to allegedly stolen T-Mobile customer data.
“We have determined that unauthorized access to certain T-Mobile data has occurred, but we have not yet determined that there was any personal customer data involved,” T-Mobile wrote.
“We are satisfied that the entry point used to access has been closed, and we are continuing our in-depth technical review of the situation in our systems to identify the nature of any data that has been illegally accessed,” the statement continued. “This investigation will take some time, but we are working with the highest degree of urgency. Until we complete this assessment, we cannot confirm the reported number of affected records or the validity of statements made by others.
The intrusion came to light on Twitter when the account @ und0xxed started tweeting the details. Reached by direct message, Und0xxed said he was not involved in the database theft, but rather was in charge of finding buyers for the stolen T-Mobile customer data.
Und0xxed said the hackers found an opening in T-Mobile’s wireless data network that allowed access to two of T-Mobile’s customer data centers. From there, the intruders were able to dump a number of customer databases totaling over 100 gigabytes.
They claim that one of these databases contains 36 million T-Mobile customers in the United States, all dating back to the mid-1990s.
The hacker (s) claim that the stolen data also includes the IMSI and IMEI data of 36 million customers. These are unique numbers built into customers’ mobile devices that identify the device and SIM card that connects that customer’s device to a phone number.
“If you want to verify that I have access to the data / the data is real, just give me a T-Mobile number and I will do a search for you and return the IMEI and IMSI of the phone currently attached to the number and any other details, “@ und0xxed said.” All prepaid and postpaid T-Mobile USA customers are affected; Sprint and other telecommunications owned by T-Mobile are not affected.
Other databases allegedly accessed by the intruders included one for prepaid accounts, which contained much less customer details.
“Prepaid customers are usually just phone numbers and IMEI and IMSI,” Und0xxed said. “In addition, the database collection includes historical entries, and there are many phone numbers associated with 10 or 20 IMEIs over the years, and service dates are provided. There is also a database that includes credit card numbers with six digit obfuscated cards.
T-Mobile declined to comment beyond what the company said in its blog post today.
In 2015, a computer breach in the three major credit bureaus Experiential exposed social security numbers and other data on 15 million people who applied for funding from T-Mobile.
Like other mobile service providers, T-Mobile is engaged in a constant battle with crooks who target its own employees in SIM swap attacks and other techniques to wrest control of employee accounts who may provide backdoor access to customer data. In at least one instance, retail store employees were complicit in the account takeovers.
WHO HACKED T-MOBILE?
The Twitter profile of the @ Und0xxed account includes a cry to @IntelSecrets, the Twitter account of a rather elusive hacker who also went through the handles IRDev and V0rtex. When asked if @IntelSecrets was involved in the T-Mobile intrusion, @ und0xxed confirmed it was.
The IntelSecrets nicknames correspond to an individual who claimed to modify the source code of the Mirai “Internet of Things” botnet to create a variant known as “Satori”, And providing it to others who have used it for criminal purposes and who have subsequently been arrested and prosecuted. Like Kenny “NexusZeta” Schuchmann, who pleaded guilty in 2019 to exploiting the Satori botnet. Two other young men have been charged in connection with Satori – but not IntelSecrets.
How do we know all this about IntelSecrets / IRDev / V0rtex? This identity recognized him in a series of bizarre lawsuits filed by someone who claims his real name is John Erin Binns. Same Identity Binns operates the website secret secrets[.]his.
On this site, Binns claims that he fled to Germany and Turkey to escape prosecution in the Satori case, before being kidnapped in Turkey and subjected to various forms of psychological and physical torture. According to Binns, the US Central Intelligence Agency (CIA) falsely declared to his counterparts in Turkey that he was a supporter or member of the Islamic State (IS), a claim which he said led to his alleged capture and torture by the Turks.
Since then, Binns has filed a flood of lawsuits against various federal agencies, including the FBI, CIA and the United States Special Operations Command (PDF), demanding that the government turn over the information gathered about him and seeking redress for his alleged kidnapping at the hands of the CIA.
Talk to the researcher Alon gal (@underthebreach), the hackers responsible for the T-Mobile intrusion said they did so to “retaliate against the United States for the kidnapping and torture of John Erin Binns in Germany by the CIA and agents of Turkish intelligence in 2019. We did it to harm US infrastructure. “
[ad_2]
Source link