[ad_1]
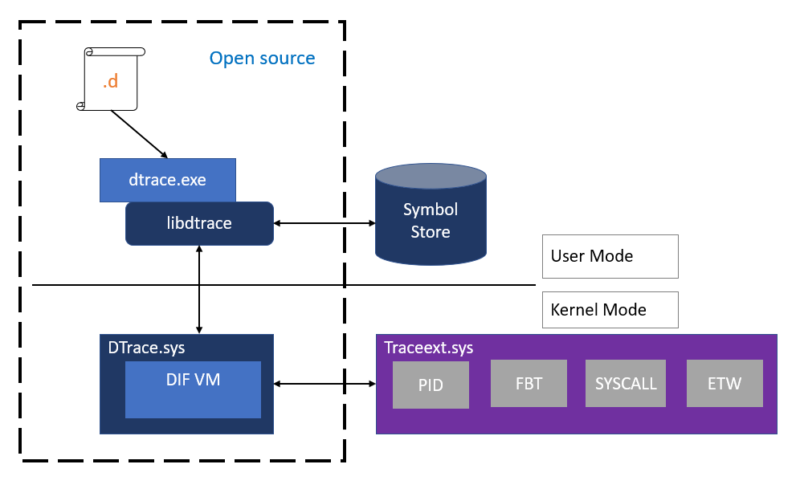
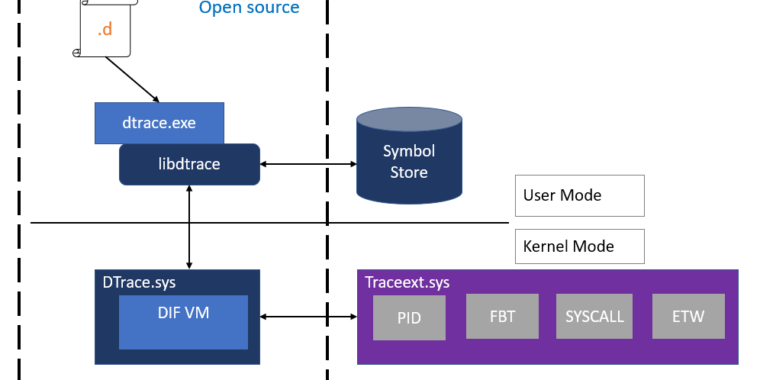
The next Windows 10 feature update will provide support for DTrace, the open source diagnostic and debug tracing tool originally created for Solaris. The port was announced at the Ignite conference last year and today, instructions, binary files and source code are now available.
DTrace provides developers and administrators with a detailed view of their system's activities: they can track kernel function calls, examine the properties of running processes, and test drivers. DTrace commands use the DTrace scripting language, which allows users to specify which information to scan and report.
After its first release of Solaris, DTrace has spread to a wide range of other Unix-like operating systems. Today, it is available for Linux, FreeBSD, NetBSD and macOS. The original Solaris code was released under Sun's common development and distribution license. Microsoft has ported DTrace's CDDL parts and created an additional driver for Windows that runs some of the system's monitoring roles. This driver will be shipped with Windows; the CDDL parts are a separate download.
The big problem is that DTrace currently requires Windows to be booted with an attached kernel debugger. DTrace inserts code bits into the analyzed system functions. This means that there is no overhead for kernel features that are not traced because they do not contain any DTrace code. However, DTrace is not the only software that alters kernel memory: rootkits correct the kernel of the operating system so that, for example, process enumeration features do not show the rootkit being run.
As a result, Microsoft introduced long ago the protection of the Windows kernel (KPP, also called PatchGuard). KPP monitors certain parts of the kernel memory for changes and blocks the system, if any. DTrace falls under the protection of PatchGuard.
Initializing with a kernel debugger disables PatchGuard, thus allowing DTrace to make the changes it needs. Microsoft developers say that they have ideas on how they could activate DTrace in a manner compatible with PatchGuard In the future. But for now, we have to choose one or the other.
[ad_2]
Source link