
[ad_1]

Researchers recently discovered a well-funded mobile phone monitoring operation that was able to surreptitiously stealing a variety of data from both iOS and Android operating systems. Researchers believe the malware is so-called "lawful intercept" software sold to law-enforcement and governments.
Exodus, as the malware for Android phones has been dubbed, was under development for at least five years. It was spread in apps disguised as service applications from Italian mobile operators. Exodus was hidden inside apps and 25 apps available in Google Play. In a report published two weeks ago, Researchers at Security without Borders said Exodus infected phones estimated to be in the "several hundreds if not a thousand or more."
Exodus consisted of three distinct stages. The first was a small dropper, which was identified by the IMEI and phone number, and sent to a command-and-control server. A second stage was installed almost immediately after the researchers' test was infected with the first stage and reported to a control server. That led researchers to believe that they are infected with later stages.
Stage two consisted of multiple binary packages that implemented the bulk of the advanced surveillance capabilities. Some of the variants encrypted communications with self-signed certificates were pinned to the apps. The binaries could also take advantage of capabilities available on specific devices. For instance, a feature in the use of "protectedapps," a feature in Huawei phones, to keep Exodus running even when the screen went dark, rather than being suspended to reduce battery consumption.
Exodus gains root control over an infected phone, typically though the use of a DirtyCOW dubbed exploit. Once fully installed, Exodus was able to carry out an extensive amount of monitoring, including:
- Retrieve a list of installed applications
- Record environments using the built-in microphone in 3gp format
- Retrieve the browsing history and bookmarks from Chrome and SBrowser (the browser shipped with Samsung phones)
- Extract events from the Calendar app
- Record phone calls audio in 3gp format
- Take pictures with the embedded camera
- Collecting information on surrounding cellular towers (BTS)
- Extract the contacts list from the Facebook app
- Extract logs from Facebook Messenger conversations
- Take a screenshot of any app in foreground
- Extract information on pictures from the Gallery
- Extract information from the Gmail app
- Dump data from the IMO messenger app
- Extract call logs, contacts and messages from the Skype app
- Retrieve all SMS messages
- Extract messages and the encryption key from the Telegram app
- Dump data from the Viber messenger app
- Extract logs from WhatsApp
- Retrieve media exchanged through WhatsApp
- Extract the Wi-Fi network's password
- Extract data from WeChat app
- Extract current GPS coordinates of the phone
The missing iOS link discovered
Monday, December 1, 2011 – Exodus said, "Exodus, Exodus, Exodus, Exodus." The iphone surveillance malware was distributed on phishing sites that masqueraded as Italian and Turkmenistani mobile carriers. Screenshots of the two sites are below:
Lookout
Lookout
The iOS version was installed using the Apple Developer Enterprise program, which allows organizations to distribute in-house apps to employees or members using the iOS App Store. The apps masqueraded as mobile carrier support apps that instruct users to "keep the app installed on your device and stay under the cloud."
The Apple-issued digital certificate used to distribute the iOS apps was associated with an Italian-based company called Connexxa S.R.L. Infected iPhones also connected to domains and IP addresses to Connexxa. Connexxa is the same Italian company whose domains were used by Exodus. A Connexxa engineer who appears to own the company also digitally signed some versions of Exodus.
Lookout
Connexxa's appearance in the Apple-issued digital certificate, its role in the server infrastructure used by both Exodus and the iOS apps, and servers that hosted both Exodus and the iOS apps give researchers a high degree of confidence the same developers. Researchers said that a company called eSurv S.R.L. was also involved. eSurv was once a business unit of Connexxa and was released to eSurv S.R.L. in 2014. In 2016, the eSurv software and brand was sold from Connexxa to eSurv S.R.L.
It's not clear how many iPhones have been infected by the iOS apps. The iOS variant is not as sophisticated as Exodus was. Unlike Exodus, the iOS version was not observed to use exploits. Instead, it relied on document programming interfaces. It was not possible to exfiltrate a variety of sensitive data including:
- contacts
- Audio recordings
- pics
- videos
- GPS rental
- Device information
Tell-tale signs
Because the iOS variant relied on Apple-provided APIs, the malware provided alerted users with certain tell-tale signs that would have alerted users that their data was being tracked. For instance, the first time the victim has been attempted, the request for permission:
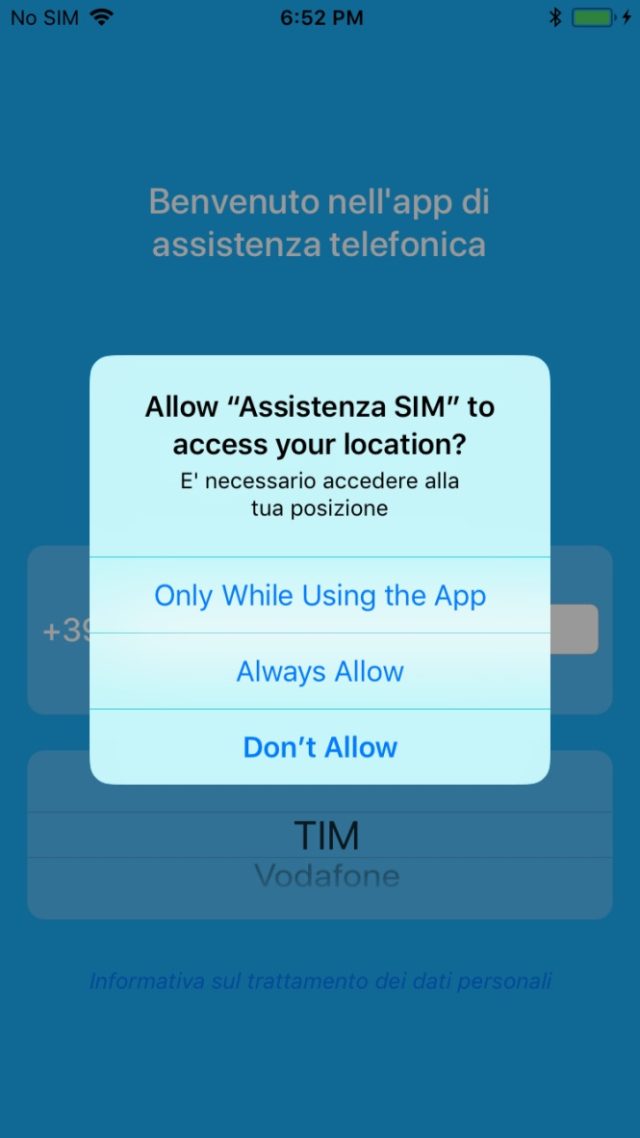
Lookout
Lookout researchers reported their findings to Apple, and the company revoked the enterprise certificate. The revocation has the effect of preventing it from being installed on new iPhones and stopping them from running on infected devices. Researchers who discovered Exodus reported their findings to Google, and the company removed the nearly 25 apps from Google Play.
[ad_2]
Source link