
[ad_1]

Apache Software Foundation released HTTP Web Server 2.4.51 after researchers discovered that a previous security update failed to properly correct an actively exploited vulnerability.
Apache HTTP Server is an open source, cross-platform web server that powers approximately 25% of the world’s websites.
On Tuesday, Apache released Apache HTTP 2.4.50 to fix an actively exploited path traversal vulnerability in version 2.4.49 (tracked as CVE-2021-41773). This flaw allows malicious actors to view the content of files stored on a vulnerable server.
“A flaw was found in a change to the normalization of paths in Apache HTTP Server 2.4.49. An attacker could use a path traversal attack to map URLs to files outside of the expected document root, ”Apache revealed in a security advisory.
“If files outside of the document root are not protected with ‘require all denied’, these requests may be successful. Additionally, this flaw could disclose the source of files interpreted as CGI scripts.”
A Shodan search revealed more than 112,000 vulnerable Apache HTTP servers exposed to the Internet, offering attackers a wide selection of potential targets.
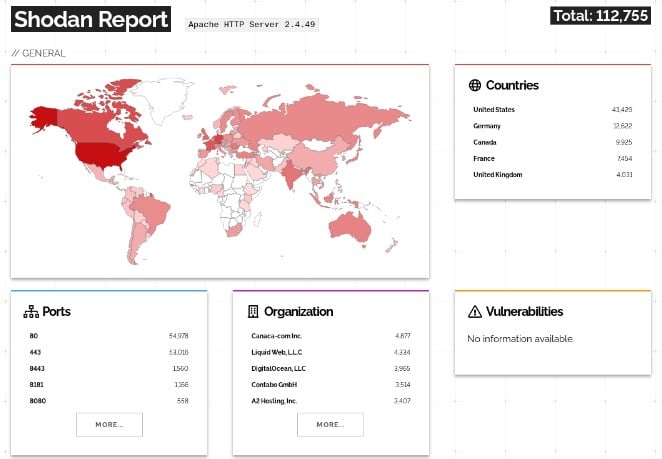
Shortly after the update was released, security researchers analyzed and disclosed the functional exploits of the vulnerability. To make matters worse, researchers also found that the vulnerability could be used for remote code execution if the mod_cgi module was loaded and the default “Require all denied” option was missing.
With so many servers potentially vulnerable to remote code execution, it has become even more critical for administrators to update their Apache HTTP servers.
Emergency update fixes incomplete patch
Today, Apache released version 2.4.51 after discovering that its previous patch for the actively exploited vulnerability CVE-2021-41773 was incomplete.
“The fix for CVE-2021-41773 in Apache HTTP Server 2.4.50 was found to be insufficient. An attacker could use a path traversal attack to map URLs to files outside of directories configured by directives from type Alias, ”Apache announced in an updated advisory.
“If files outside of these directories are not protected by the usual default ‘required all denied’ configuration, these requests may be successful.” If CGI scripts are also enabled for these alias paths, it could allow remote code execution. “
This new path crossing vector is tracked as CVE-2021-42013, and it was disclosed by Juan Escobar of Dreamlab Technologies, Fernando Muñoz of NULL Life CTF Team, and Shungo Kumasaka.
The United States Computer Emergency Preparedness Team (US-CERT) says this new vulnerability is also being exploited in ongoing attacks.
The active scan of the Apache HTTP server CVE-2021-41773 and CVE-2021-42013 is in progress and is expected to accelerate, possibly leading to exploitation. Please correct immediately if you haven’t done so already — it can’t wait until after the weekend. Read more: https://t.co/4Ljk730wz4 pic.twitter.com/TYPiXhOluf
– US-CERT (@USCERT_gov) October 7, 2021
Now that it’s been officially disclosed, it won’t be long before other threat actors create their own working exploit.
For this reason, administrators are strongly recommended to immediately upgrade their servers to Apache HTTP 2.4.51 to remove any attack vectors left after the previous patch.
[ad_2]
Source link