[ad_1]

Apache has released patches to fix two security vulnerabilities, including a path traversal and file disclosure flaw in its HTTP server which it says is actively exploited in the wild.
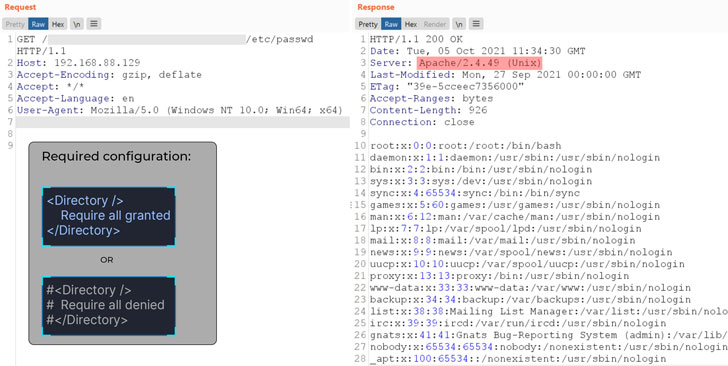
“A flaw was found in a change to the normalization of paths in Apache HTTP Server 2.4.49. An attacker could use a path traversal attack to map URLs to files outside of the expected document root”, Those responsible for the open source project noted in a notice published on Tuesday.
“If files outside of the document root are not ‘require all denied’ protection, these requests may succeed. Additionally, this flaw could disclose the source of files interpreted as CGI scripts.”

The flaw, tracked as CVE-2021-41773, only affects version 2.4.49 of the Apache HTTP server. Ash Daulton and the cPanel security team were credited with discovering and reporting the issue on September 29, 2021.
 |
| Source: PT SWARM |
Apache also addressed a null pointer dereference vulnerability observed while processing HTTP / 2 requests (CVE-2021-41524), allowing an adversary to perform a denial of service (DoS) attack on the server. The nonprofit said the weakness was introduced in version 2.4.49.

Apache users are highly recommended correct as soon as possible to contain the path crossing vulnerability and mitigate any risk associated with active exploitation of the vulnerability.
[ad_2]
Source link