
[ad_1]

Attackers target users of GitHub, GitLab and Bitbucket, erasing code and validations from multiple repositories based on reports, leaving only a ransom note and many questions.
Deprecated targets use multiple Git repository management platforms, the only other link between the reports, apart from Git, being that the victims were using the free Git SourceTree cross-platform client. [1, 2, 3, 4].
Although BleepingComputer could not get in touch with Atlassian, the company behind SourceTree, a user would have received a statement from the company that:
"In the last few hours we have detected and blocked an attempt – from a suspicious IP address – to log in with your Atlassian account.We believe that someone has used a list of stolen login information to third-party services to try to access multiple accounts. "
After having infiltrated the depot of the victims and erased all the history of the commit, the attackers will leave only one commit, named "WARNING", containing a single file containing the following contents (the note of the ransom):
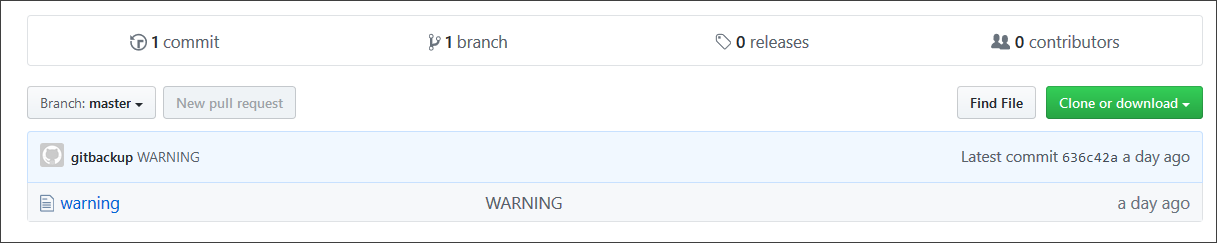
This "warning" of the ransom asked the victims to send 0.1 BTC, which equates to about 568 dollars, in order to recover their data.
To recover your lost code and avoid any leaks: send us 0.1 Bitcoin (BTC) to our Bitcoin address 1ES14c7qLb5CYhLMUekctxLgc1FV2Ti9DA and contact us by email at [email protected] with your Git ID and proof of payment. If you do not know if we have your data, contact us and we will send you a proof. Your code is downloaded and saved on our servers. If we do not receive your payment within the next 10 days, we will return your code or otherwise use it.
On the BitcoinAbuse platform, the Bitcoin address used by the attackers already contains 27 reports, the first being filed on May 2nd.
However, when searching on GitHub, we found 392 impacted repositories, of which all validations and codes were cleared with the help of the account & gitbackup & # 39; gitbackup & # 39; who joined the platform seven years ago, January 25, 2012.
Despite this, none of the victims paid the ransom demanded by the hackers, knowing that the Bitcoin address had received only 0.00052525 BTC May 3 via a single transaction, which equates to about 2.99 USD .
For the moment, there is no detail on how the attackers could access the accounts of their victims, but, as one StackExchange user said, even if he had the 2FA feature, he did not never received an SMS telling him that he had managed to connect. . "
A report says that GitHub suspends accounts and investigates after the attacks have been detected: "GitHub suspended my account last night while they were investigating.I hope to hear them today. 39 may have been lucky. "
In addition, although GitHub, GitLab, and Bitbucket have not yet released a statement about the current attack, users have tried to find a solution to the problem, with an ongoing discussion available HERE and a possible fix in this StackExchange exchange. to post.
BleepingComputer solicited comments from GitHub and GitLab, but had no news at that time.
[ad_2]
Source link