
[ad_1]
389
They found three security breaches affecting mobile telephone networks 4G and 5G . Earlier this month, we learned about the existence of a 5G, 4G and 3G network security breach that allowed IMSI sensors to spy on conversations. And now, a new fault has been detected and the 4G and the 5G are affected, so that they could spy phone calls and know the exact place of the users who are connecting.
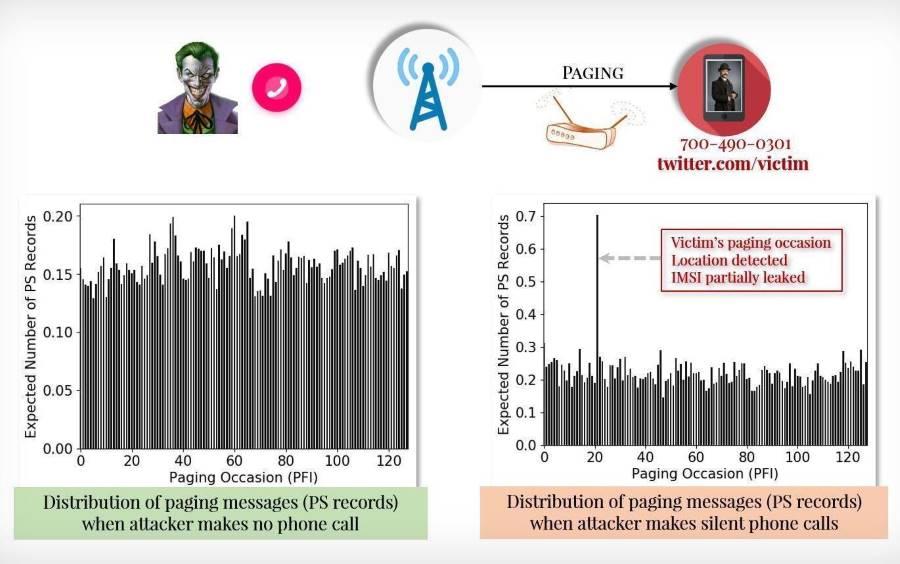
According to the explanations of one of the people involved in this investigation, "anyone" having some knowledge of cell paging protocols would be able to lead this attack. As we reported, if this vulnerability were exploited, they could spy on telephone conversations locate the exact location of users and launch targeted phishing attacks. One of the failures is "Torpedo" which affects the protocol used for to notify to a device receiving a call or a message; Piercer follows, which would allow to know the IMSI of anyone, for example IMSI-Cracking to force an IMSI number in the 4G and 5G networks.
With a device of only 200 USD, you can attack. A 4G or 5G user spies his telephone conversations
These security vulnerabilities on the networks 4G and 5G can be exploited with radio equipment that costs only $ 200 . The Torpedo vulnerability makes it possible to make several calls – and to cancel them – in a short time, a search message is triggered without the target device being alerted. This can be used to locate the victim, but also for targeted phishing attacks and to hijack communications.
These three serious security issues were reported to the GSMA, which acknowledged the existence of these vulnerabilities. However, the GSMA did not provide additional details, nor when the problems could be solved. While Torpedo and IMSI-Cracking must be solved in the first place by the GSMA, the solution to Piercer's vulnerability lies with the telecom operators. And in any case, the priority is to repair the security vulnerability Tordpedo, depending on the type of attack that can be launched against users.
Written by Carlos González
[ad_2]
Source link