
[ad_1]

The surge in cryptocurrency valuations has broken record after record in recent years, turning people with once modest holdings into millionaires overnight. A determined circle of criminals have attempted to join the party using a large-scale operation that for the past 12 months has used a full-fledged marketing campaign to push custom malware written from scratch for devices. Windows, macOS and Linux.
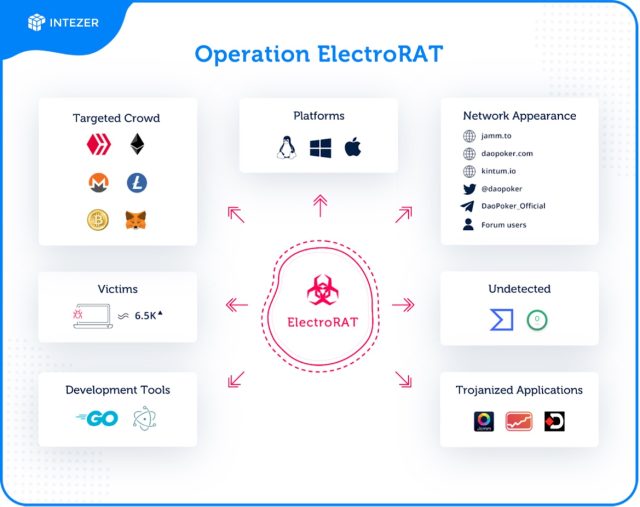
The operation, which has been active since at least January 2020, has spared no effort to steal the wallet addresses of unwitting cryptocurrency holders, according to a report released by security firm Intezer. The diagram includes three separate Trojan horse applications, each running on Windows, macOS, and Linux. It also relies on a network of bogus businesses, websites and social media profiles to gain the trust of potential victims.
Rarely stealthy
The applications present themselves as benign software useful to cryptocurrency holders. Hidden inside is a Remote Access Trojan that was written from scratch. Once the app is installed, ElectroRAT – as Intezer has dubbed it the backdoor – allows the crooks behind the operation to record keystrokes, take screenshots, upload, download and upload. install files and run commands on infected machines. As a testament to their stealth, bogus cryptocurrency apps have not been detected by all major antivirus products.
“It’s very rare to see a RAT written from scratch and used to steal personal information from cryptocurrency users,” the researchers wrote in the Intezer report. “It’s even rarer to see such a large and targeted campaign that includes various components such as bogus apps and websites, and marketing / promotion efforts through relevant forums and social media.”
The three applications used to infect targets were called “Jamm”, “eTrade” and “DaoPoker”. The first two apps claimed to be a cryptocurrency trading platform. The third was a poker app that allowed betting with cryptocurrency.
The crooks used fake promotional campaigns on cryptocurrency-related forums such as bitcointalk and SteemCoinPan. The promotions, which were posted by fake social media users, led to one of three websites, one for each of the trojanized apps available. ElectroRAT is written in the Go programming language.
The image below summarizes the operation and the different elements it used to target cryptocurrency users:
Intezer
Execmac Tracking
ElectroRAT uses Pastebin pages posted by a user named “Execmac” to locate its command and control server. The user’s profile page shows that since January 2020, pages have received over 6,700 pageviews. Intezer estimates that the number of visits roughly matches the number of people infected.
The security company said that Execmac has in the past had ties to the Amadey and KPOT Windows Trojans, which are available for purchase in underground forums.
“A reason behind it [change] could be targeting multiple operating systems, ”the Intezer post speculated. “Another motivating factor is that this is unknown Golang malware, which kept the campaign under the radar for a year bypassing all virus detections.”
The best way to find out if you have been infected is to search for the installation of one of the three applications mentioned earlier. The Intezer post also provides links that Windows and Linux users can use to detect ElectroRAT running in memory. Infected people must sanitize their systems, change all passwords, and transfer funds to a new wallet.
[ad_2]
Source link