
[ad_1]

This malware attack uses your emotions, including fear, to trick you into installing malware on your phone
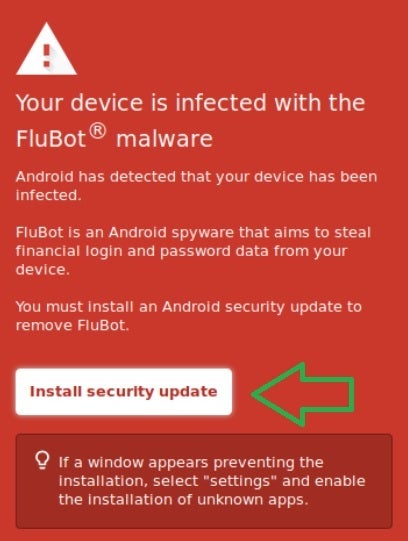
This fake text message tries to scare you into installing malware on your Android phone
And just below that copy, written to scare off Android users, is a link that says “Install security update.” The text even asks Android users to remove some protections they might have had against installing malicious apps. At the bottom of the message it is noted: “If a window appears preventing installation, select ‘Settings’ and enable installation of unknown applications.”
If you click on the link but do not install the app, your phone will not be infected. Nonetheless, Cert NZ suggests that if you click on the link, you should change all of your passwords and contact your bank for security. If you click on the link and install the app, you need to wipe your phone by performing a factory reset. You should also change all of your passwords and call your bank.
FluBot has successfully tricked Android users into giving it permissions while it is running in the background, creating all kinds of havoc for device owners. FluBot has been spotted in Spain, Germany, Poland, Hungary, UK and Switzerland as well as Australia and Japan. It can steal banking and payment information by placing overlays on legitimate banking, payment, and cryptocurrency apps.
Another trick is trying to get you to install a parcel tracker on your handset
The key to this particular scam is making you so nervous about FluBot that you are looking for anything you can use to block it. So the scam text saves your life in the form of a bogus software update designed to attack your phone with the virus you think you’re protecting it from.
Another trick used is to get excited about a fake package that’s supposed to come your way. This message also tells you how to disable the block against installing unknown applications. Again, the bad actors play with your emotions because they know that most people like to receive unexpected packages.
The way to prevent your Android phone from getting infected is to use common sense. Don’t quickly tap on a link and if something doesn’t seem kosher about a text you receive, delete it immediately. And even if you don’t live in an area where FluBot has been seen, at least not yet, you should still be aware of this scam.
[ad_2]
Source link