[ad_1]
Homeland Security warned of a set of critical vulnerabilities in Medtronic defibrillators that expose devices to a risk of manipulation.
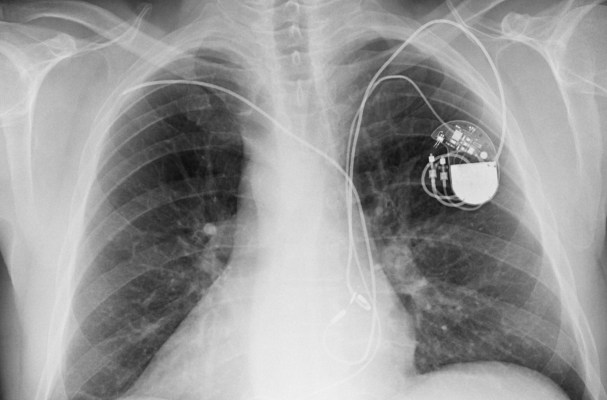
These small implantable cardio defibrillators are implanted into a patient's chest to emit small electrical shocks to prevent irregular or extremely fast heartbeat, which can be fatal. Most modern devices are equipped with wireless technology or radio to allow patients to monitor their condition and their doctor to adjust settings without having to perform invasive surgery.
The government's warning warned, however, that Medtronic's proprietary radio communication protocol, called Conexus, was not encrypted and did not require authentication, allowing a nearby attacker with equipment intercepting the radio. modify the data of an badigned defibrillator.
Homeland Security gave the alert a rating of 9.3 out of 10, describing it as requiring a "low level of skill" to operate.
This does not mean that anyone with an badigned defibrillator suddenly becomes a target for hackers. These devices do not always broadcast radio frequency, because it would require too much battery. Medtronic said patients would be most at risk when their patients have their implants checked while at their doctor's office. At any other time, the defibrillator will wake up from time to time and look for a nearby surveillance device if it is within range, reducing the scope of an attack.
More than 20 models of Medtronic defibrillators and models are involved, the alert said, including the CareLink programmer used in doctors' offices and the MyCareLink monitor used in patients.
Peter Morgan, founder and director of Clever Security, discovered and reported the virus to Medtronic privately. In an email, Morgan told TechCrunch that the bugs were not easy to detect, but were warned of a potential risk to patients.
"It is possible with this attack to damage a patient, either by erasing the firmware that gives the necessary treatment to the patient's heart, or by directly invoking shock commands on the defibrillator," he said. "Since this protocol is not authenticated, the DAI can not know if the communications it receives come from a trusted Medtronic device or an attacker."
A successful attacker could delete or reprogram the defibrillator firmware and execute any device command.
Medtronic said in his own opinion that he did not know any patient whose devices had been attacked, but that the company was "developing updates" to address vulnerabilities, but did not specify when patches would be applied.
The Food and Drug Administration (FDA), which regulates medical devices, has provided a list of affected devices.
This is the latest example of smart medical devices at worst, even as healthcare spending on cybersecurity is expected to become a $ 65 billion industry by 2021.
The FDA made non-binding recommendations in 2016 to advise medical device manufacturers to improve cybersecurity to prevent this type of problem from occurring by advising companies to "provide cybersecurity controls when designing and develop the devices performance device against cyber threats. "
Yet this latest government alert marks the second time in two years that Medtronic has been forced to respond to security vulnerabilities in its medical devices. In October, the company finally closed an internet-based software update system that was jeopardizing its pacemaker monitoring devices.
Source link