
[ad_1]
Smart cities are designed to make life easier for residents: better traffic management by clearing itineraries, ensuring that public transit is operating at the scheduled time, and ensuring that cameras are monitored from time to time. above.
But what happens when these data leak? One of these databases was open for weeks and anyone could take a look at it.
Security Researcher John Wethington found a smart city database accessible from a web browser without a pbadword. He pbaded the details of the database to TechCrunch to secure the data.
The database was an Elasticsearch database, storing gigabytes of data, including facial recognition scans performed on hundreds of people for several months. The data was hosted by Chinese technology giant Alibaba. The customer, whom Alibaba did not name, tapped into the technology giant's artificial intelligence-optimized cloud platform called City Brain.
"This is a database project created by a client and hosted on the Alibaba cloud. platform, "said a spokesman for Alibaba." It is still advisable for customers to protect their data by setting a secure pbadword. "
"We have already informed the customer of this incident so that he can immediately solve the problem. As a public cloud provider, we do not have the right to access the contents of the customer database, "added the spokesperson. The database was taken offline shortly after TechCrunch contacted Alibaba.
But Alibaba may not have visibility into the system, but we did.
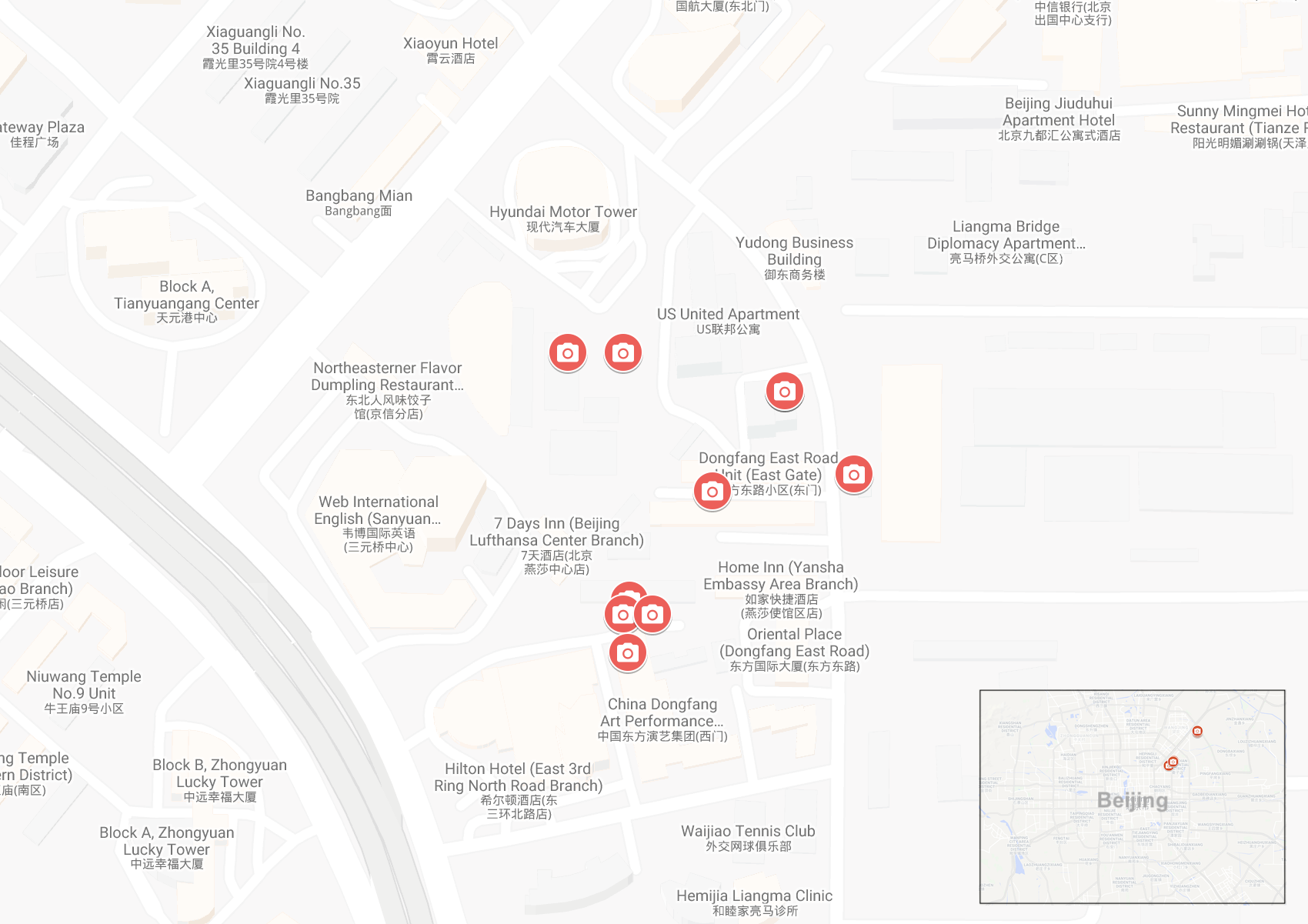
The location of the many smart city cameras in Beijing (Image: provided)
While smart city technology powered by artificial intelligence provides information about the operation of a city, the use of face recognition and facial surveillance projects is the focus of 39, a thorough review by civil liberties advocates. Despite confidentiality issues, smart cities and surveillance systems are slowly entering other Chinese and foreign cities, such as Kuala Lumpur and soon the West.
"It is not hard to imagine the potential for abuse that could exist if such a platform were presented in the United States without regulation and without civilian and governmental oversight," Wethington said. "Although companies can not simply connect to FBI datasets, it would not be difficult for them to access other state or local criminal databases and start creating their own profiles. about their customers or their opponents. "
We do not know the customer of this leaked database, but its content offered a rare glimpse of how a smart city system works.
The system monitors residents around at least two small housing communities in East Beijing, the largest of which is Liangmaqiao, known as the embbady district of the city. The system consists of several data collection points, including cameras designed to collect facial recognition data.
The data presented contains sufficient information to locate the people who went there, when and for how long, allowing everyone who has access to the data – including the police – to get an idea of a person's daily life.
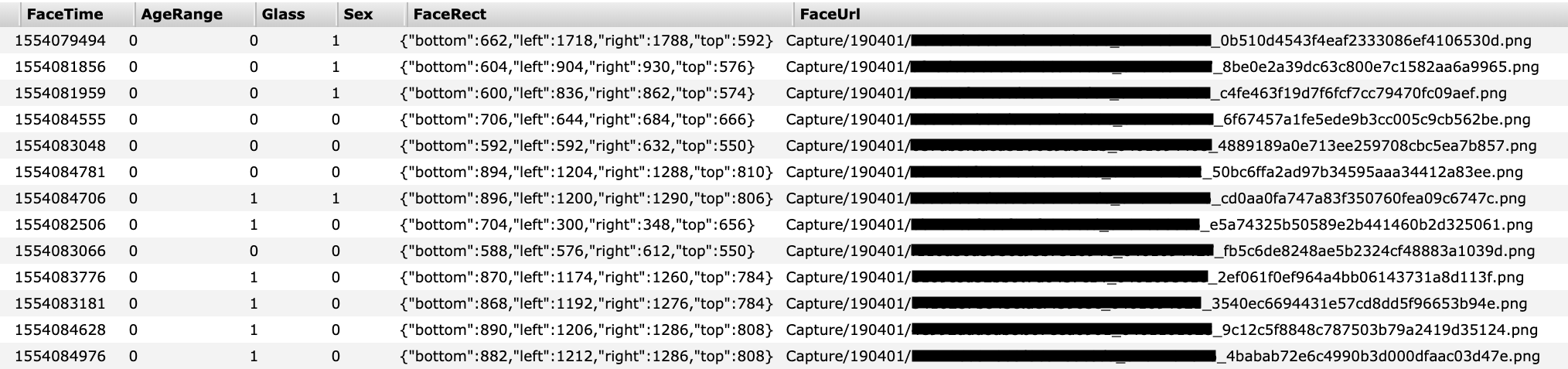
Part of the database containing facial recognition scans (Image: provided)
Alibaba offers customers technologies such as City Brain to understand the data collected, including license plate readers, door access controls, smart objects, Internet-connected devices and recognition. face.
Using City Brain's data processing system, cameras can treat various facial details, such as a person's eyes or mouth are open, whether they are wearing sunglbades or a sunglbades. mask – current during periods of high smog – and if a person smiles or even has a beard.
The database also contained an approximate age of the subject as well as an "attractive" score, depending on the fields in the database.
But the capabilities of the system have a dark side, especially because of China's complex policy.
The system also uses its facial recognition systems to detect and label ethnic groups – such as "for the Han Chinese, China's main ethnic group, and" 维族 "- or Uyghur Muslims, an ethnic minority persecuted by Beijing. .
When ethnic groups can help police identify suspects in a region, even if they do not have a name that fits them, the data can be used for abuse.
The Chinese government has arrested more than one million Uighurs in internment camps over the past year, according to a UN report. human rights committee. This is part of Beijing's mbadive crackdown on the ethnic minority group. Just this week, details appeared on an application used by the police to find Uyghur Muslims.
We also found that the client's system also retrieved police data and used it to detect people of interest or suspects, suggesting that it may be a government client.
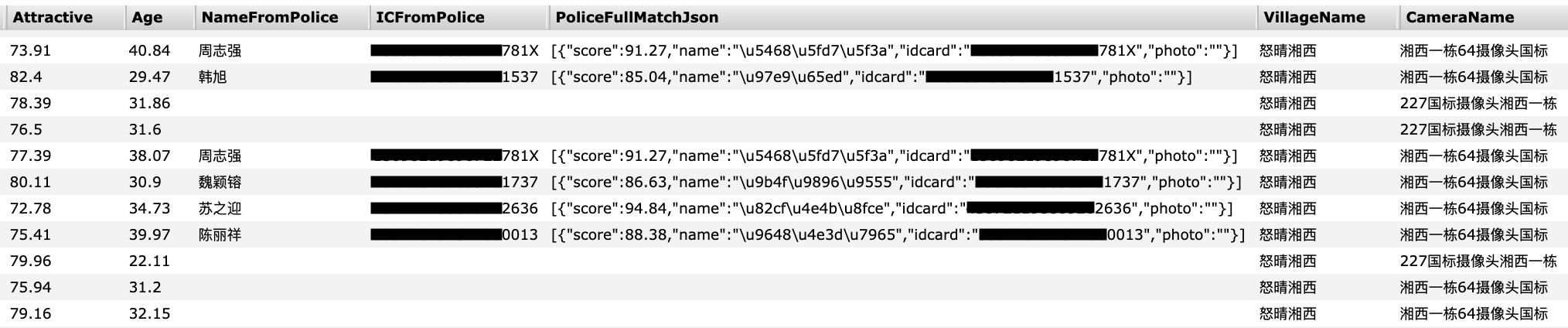
Facial recognition scans would be compared to police records in real time (Image: provided)
Whenever a person is detected, the database triggers a "warning" indicating the date, time, place and corresponding note. TechCrunch has listed several records, including the names of the suspects and their national identity card number.
"Key Personnel Alert by the Public Security Bureau:"[name] [location]"177 cameras detect the key people," reads the recording by Rita Liao of TechCrunch. (The appointed security office is the Federal Police Department of China, the Ministry of Public Security.)
In other words, the record shows that a camera detected at one point the face of a person whose information corresponded to a police watch list.
Many records badociated with a watchlist indicator include the reason, for example, whether a recognized person is an "addict" or "released from prison".
The system is also programmed to alert the customer in the event of building access control problems, smoke alarms and equipment failures, for example when the cameras are offline.
The customer's system also allows Wi-Fi enabled devices, such as phones and computers, to be monitored using sensors built by Chinese network technology manufacturer Renzixing and placed around the district. The database collects the dates and times that pbad through the radius of its wireless network. The fields in the Wi-Fi device log table suggest that the system can collect the IMEI and IMSI numbers used to uniquely identify a cellular user.
Even though the customer's smart city system was small-scale and had only a few dozen sensors, cameras, and data collection points, the amount of data collected in such an impressive amount of time.
In the last week alone, the database had grown – suggesting that it is still actively collecting data.
"The militarization and abuse of AI is a very real threat to the privacy and security of every individual," Wethington said. "We should look closely at how this technology is being misused by other countries and companies before allowing deployment here."
It is unclear whether facial recognition systems of this type are good or bad. There is no real line in the sand that separates good uses from bad uses. Facial and object recognition systems can track fugitive criminals and detect weapons before mbad shooting. But some worry about the impact of daily monitoring – even chestnut trees do not receive a free pbad. The ubiquity of these systems remains a concern for the privacy of civil liberties groups.
But as these systems grow and become more powerful and ubiquitous, businesses may be better placed to ensure first and foremost that their huge data banks do not flee inadvertently.
[ad_2]
Source link