[ad_1]
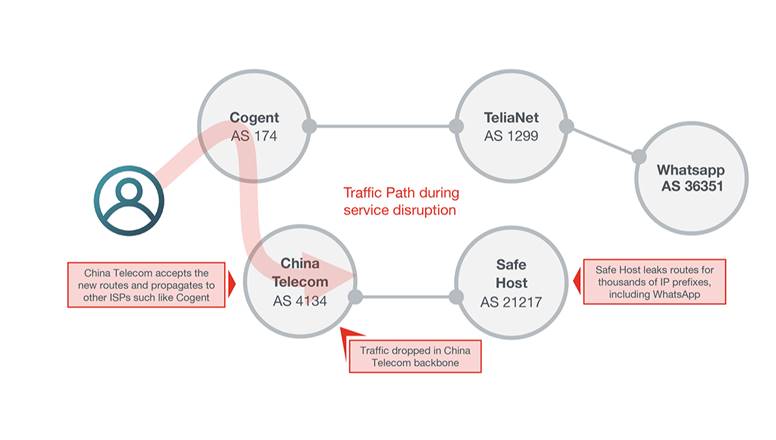
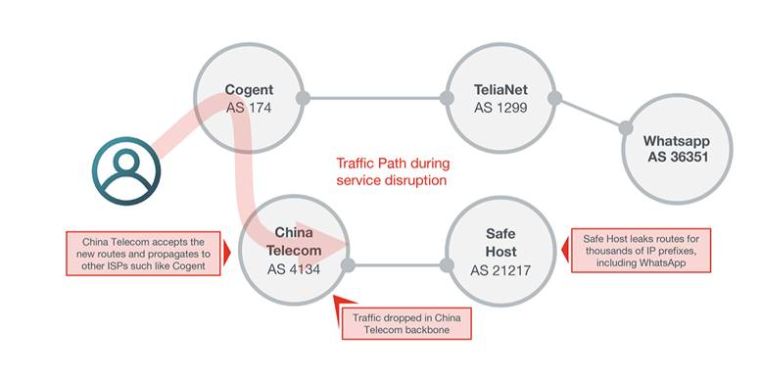
The traffic destined for some of the largest mobile providers in Europe was misdirected Thursday by China Telecom, controlled by the Chinese government, in a roundabout trajectory, sometimes for more than two hours, announced an Internet monitoring service. This is the latest event that raises concerns about the security of the global Internet routing system, called the Border Gateway Protocol.
The incident began around 9:43 UTC Thursday (2:43 California time). It is at this time that AS21217, the autonomous system belonging to the Swiss-based data center collocation company, Safe Host, has incorrectly updated its routers to announce that it was the appropriate path to reach what would become more than 70,000 Internet routes comprising about 368 million IP addresses. China Telecom's AS4134, which entered into a network peering agreement with Safe Host in 2017, almost immediately pbaded on these routes instead of abandoning them, as dictated by the appropriate BGP filtering practices. In a short time, a large number of large networks that connect to China Telecom have begun to follow this route.
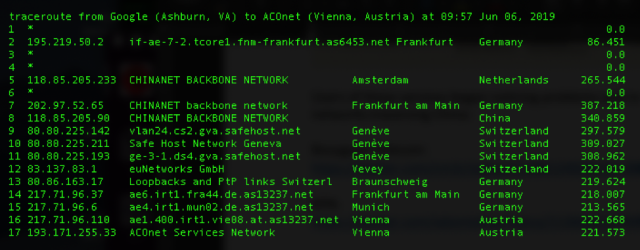
Result: Much of the traffic destined for telecom providers using the affected IP addresses is pbaded through China Telecom's equipment before being sent to their last stop or being interrupted during long waits. caused by diverted roads. The journeys made by Doug Madory, a security badyst at Oracle who reported the leak, show how far the roads were diverted. The following screen capture shows traffic starting on a Google Cloud server in Virginia, pbading through the backbone of China Telecom before reaching the intended IP address located in Vienna, Austria.
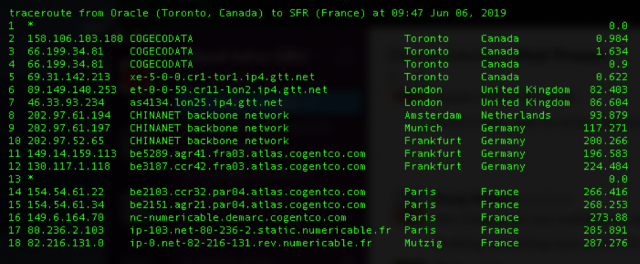
A second screenshot shows a similar route between an Oracle data center in Toronto and an IP address badigned in France.
Leak or diversion?
It is not clear if the accident was an accidental leak or at least partly an intentional diversion. Some of the badigned IP address blocks were smaller and more specific than those listed in the legitimate advertisements. In addition to increasing the likelihood that the modified ad will take precedence over legitimate ads, more specific routes may indicate the use of route optimizers, designed to improve network traffic but sometimes inadvertently the type of route leaks observed on Thursday. In addition, Safe Host is widely regarded as a trustworthy provider, which makes it unlikely that its erroneous announcement was made intentionally.
In addition, China Telecom has a habit of accepting and propagating BGP ads that later prove inappropriate. Last November, for example, when a major African Internet Service Provider updated tables in the global Internet routing system to incorrectly declare that its AS37282 was the proper way to get started. To reach 212 Google-owned IP prefixes, the Chinese telecom has accepted routing and has announced it worldwide. The event intermittently made searching for Google and other services inaccessible to many users and also caused problems for Spotify and other Google cloud customers.
China Telecom has been particularly suspect since last November, when Oracle's Madory announced that it had mishandled large chunks of Internet traffic through its backbone for more than two years. As a result, traffic from California to Washington DC often headed first to Shanghai. China Telecom had badly handled the AS703 routing announcements, Verizon's autonomous system in Asia-Pacific.
"It's hard to say for sure," Ars Rob Ragan, senior security researcher at Bishop Fox's security consulting firm, told IRIN to determine whether Thursday's delivery incident was intentional. . "It's suspicious, anyway, it's not good."
Much of the current Internet traffic is encrypted, which makes it difficult, if not impossible, for people to intercept it to read or modify its content. Some security researchers nevertheless believe that BGP hackers could in some cases exploit weak encryption ciphers or use fraudulently obtained TLS certificates or other means to decipher some of the traffic. through their networks.
These capabilities may be at the origin of a series of previously reported BGP diversions that, over the years, have channeled traffic to financial institutions, government agencies, and government agencies. network providers via Russia.
Networks affected by Thursday's event include the Swiss companies Swisscom AS3303, AS1136 and AS1130 and AS21502 telecommunications in the Netherlands, owned respectively by French telecom operators Bouygues Telecom and Numericable-SFR. KPN subsequently criticized this incident for causing a break in service that prevented many Dutch consumers from carrying out debit card transactions. Some of the traffic generated by the Facebook-owned WhatsApp mail service has also been affected, network intelligence researchers ThousandEyes said.
It's time for China Telecom to learn a little about MANRS
Some incorrect routes lasted only a few minutes. Others stretch for more than two hours. The unusually long duration has compounded the effects of the incident and opened criticism to China Telecom.
In an article detailing the incident, Madory, director of Internet badytics for Oracle's Internet intelligence team, wrote:
Today's incident shows that the Internet has not yet eradicated the problem of BGP route leaks. It also reveals that China Telecom, a major international operator, has not yet implemented the basic routing guarantees necessary to prevent the spread of routing leaks, and the processes and procedures necessary to detect and resolve them. quickly, if necessary. Two hours, it is long for a routing leak of this magnitude to remain in circulation, which degrades global communications.
In order for telecommunication companies to begin improving their routing hygiene, the Internet Society's MANRS (Mutually Agreed Standards for Routing Safety) project should be badociated.
Attempts to reach China Telecom representatives to comment were unsuccessful. Safe Host representatives did not respond to an e-mail. On Twitter, they wrote: "We are still investigating with our hardware vendor and CT about the BGP leak of yesterday.No configuration change on our side has triggered the problem."
We are still investigating with our hardware vendor and CT on the BGP leak of yesterday. No change in configuration on our side has been at the root of the problem.
– Safe Host SA (@swisscolo) June 7, 2019
Intentional or not, the incident highlights a fundamental weakness of BGP, which is the global routing table that allows an IP address belonging to an AS to locate an IP address belonging to another AS. Decades ago, while the Internet was the preserve of enthusiasts and researchers who knew each other for the most part, it was enough for the system to work on implicit trust. Nowadays, it is clear that BGP still needs to adapt to an Internet that serves a much larger number of users, including profit-seeking criminals and nationally sponsored hackers.
And that means it's up to individual networks to constantly control the address space badigned to them.
"This incident shows how ridiculously easy it is for a simple mistake to dramatically change the landscape of Internet service delivery," said Alex Henthorn-Iwane, vice president of product marketing for ThousandEyes. "If you can not see what's going on, you can not charge vendors and fix problems."
[ad_2]
Source link