[ad_1]
June 7, 2019 –
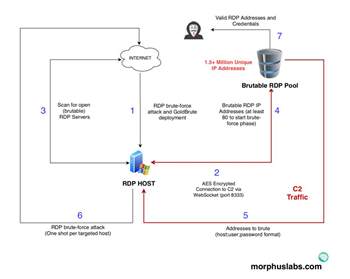
A new botnet named Goldbrute targets Windows servers with the Remote Desktop Protocol enabled. Currently, more than 1.5 million servers must be attacked.
According to a report from "Zdnet.com", security researchers learned that a new network of zombies was attacking millions of Windows servers with Remote Desktop Protocol (RDP) enabled. The botnet, called Goldbrute, was discovered by security expert Renato Marinho, of Morphus Labs. It is currently performing brute force attacks on approximately 1.5 million RDP servers.
According to Marinho, the botnet works as follows: A botnet computer accesses a Windows computer through an RDP connection via a brute force attack. In a next step, a malware zip file is loaded and the attacked server searches the Internet for new RDP endpoints. As soon as 80 new RDP connections are found, the IP addresses are sent to the own command and control server. The infected server then receives a set of IP addresses for new brute force attacks, providing each address only with a user / pbadword combination with which the bot computer attempts to connect. Each bot thus obtains different identification information, which is used to carry out brute force attacks.
The bot network is difficult to detect by security mechanisms because each bot computer only attempts once to connect to the targeted system.
(Rd)
[ad_2]
Source link