[ad_1]
The cloud hosting provider iNSYNQ said it was trying to recover from a ransomware attack that had shut down its network and left customers unable to access their accounting data in the last three days. Unfortunately for iNSYNQ, the company seems to be turning a deaf ear to the increasingly anxious cries of its users who want more information about the incident.
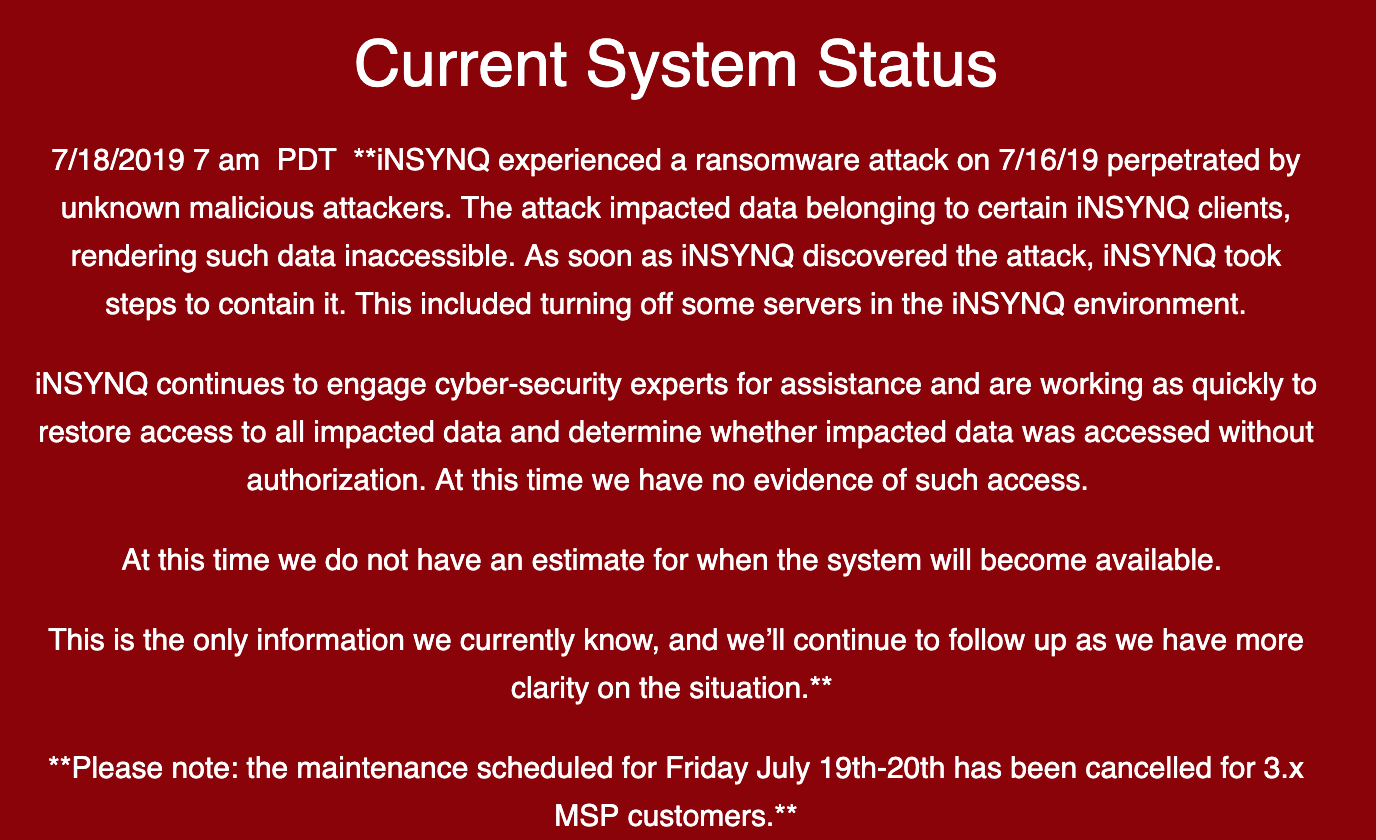
A message from iNSYNQ to customers.
INSYNQ based on Gig Harbor, Wash., Is specialized in providing QuickBooks software and accounting services. In a statement posted on his status page, iNSYNQ said it was the victim of a ransomware attack on July 16 and disconnected its network to try to contain the spread of the malware.
"The attack has affected data belonging to some iNSYNQ customers, making this data inaccessible," the company said. "As soon as iNSYNQ discovered the attack, he took steps to contain it. This included disabling some servers in the iNSYNQ environment. "
iNSYNQ stated that it used external cybersecurity badistance to determine whether client data had been accessed without authorization, but that, until now, no estimate of when these files could be re-profiled available for customers.
In the meantime, iNSYNQ's clients – including many accountants who manage financial data for a number of their own clients – have used Twitter to express their frustration at the lack of updates since this initial message to users .
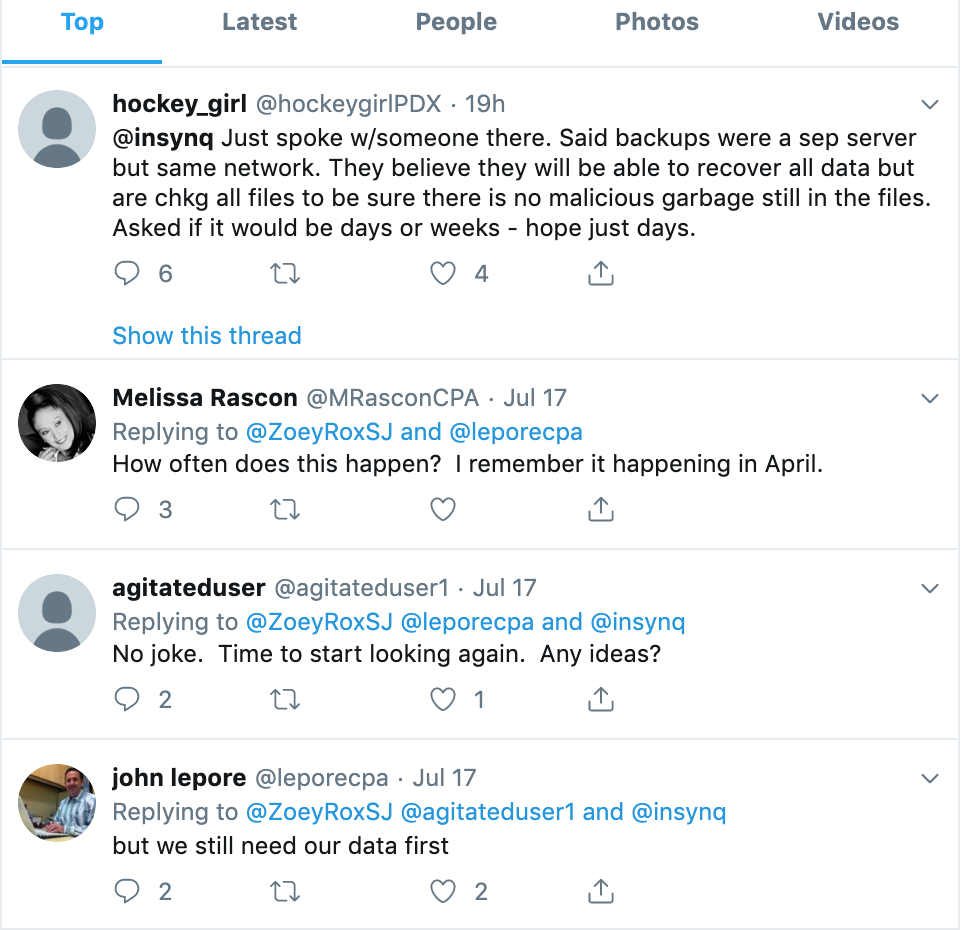
In response, the company appears to have simply deleted or disabled its Twitter account (a cached copy of June 2019 is available). right here). Several customers denouncing the crash on Twitter have also accused the company of not posting negative comments about the incident on its Facebook page.
Some of these customers also stated that iNSYNQ had initially attributed the outage to an alleged problem with Comcast, the US cable television giant nationwide. At the same time, competing cloud hosting providers have increased reactions to the iNSYNQ outage by marketing their own services, claiming that they would never subject customers to a three-day outage.
iNSYNQ has not yet responded to requests for comment.
Update, 4:35 pm ET: I just heard the CEO of iNSYNQ Elliot Luchansky, who shared the following text:
Although we have continually updated our website and are sending emails to our customers once or twice a day during this malware attack, I acknowledge that we had to minimize the details.
Unfortunately, and as you well know, the lack of detailed information we shared was deliberate and aimed at protecting our customers and their data. We are in trench warfare behind the scenes and we are doing everything. we can eventually secure and restore our system and client data and backups. I understand why our customers are frustrated and we want above all to share all the information we have.
Our customers and their businesses are our number one priority right now. Our team is working tirelessly to secure and restore access to all impacted data, and we expect to see an end in sight in the near future.
You know as well as we do that no one is 100% safe from this situation – big and small businesses, governments and individuals are vulnerable. iNSYNQ and our customers were victims of a malicious software attack, a totally new variant that had not yet been detected, confirmed by the experienced and competent cybersecurity team we employ.
Original story: There is no doubt that a ransomware infestation in any business – not to mention a data provider in the cloud – can quickly turn into an all-in-one emergency on the bridge that diverts the attention of all to solve the problem as quickly as possible. .
But this is not an excuse to leave customers in the dark and not to provide frequent and transparent updates on what the victim organization is doing to remedy the situation. In particular, when the cloud provider in question posts on his blog consistently about how companies can minimize the risks of such incidents by trusting them for their data.
Among the victims of ransomware, perhaps we can mention cloud data hosting providers and software offerings as services, because these companies are totally unable to serve their customers when a ransomware infestation is activated.
The FBI and several security companies have advised the victims not to pay ransom, as this would only encourage the attackers and, in any case, would not recover the access to the encrypted files.
However, in practice, many cybersecurity consulting firms quietly insist that paying is the fastest way to return to the status quo. It's not difficult to understand why: stealing or stealing customer data can drive many customers to find new suppliers. As a result, the temptation to simply pay can become stronger each pbading day.
That's exactly what happened in February, when the cloud payroll data provider Apex Human Capital Management was shut down for three days as a result of a ransomware infestation.
Christmas Eve 2018, cloud hosting provider Dataresolution.net has put its systems offline in response to an outbreak of ransomware on its internal networks. The company was adamant that it would not pay the ransom demand, but it took several weeks before customers regained access to their data.
KrebsOnSecurity will strive to update this story as more and more details become available. Any iNSYNQ affected by the failure is welcome to contact this author via Twitter (my direct messages are open to everyone) or krebsonsecurity @ gmail.com.
Tags: iNSYNQ ransomware attack
This entry was posted on Friday, July 19th, 2019 at 12:40 pm and is filed under Data breaches.
You can follow the comments of this entry via the RSS 2.0 feed.
You can go to the end and leave a comment. Ping is currently not allowed.
[ad_2]
Source link