
[ad_1]
What is a networked DMZ?
In computer networks, a DMZ, or demilitarized zone, is a physical or logical subnet that separates a local area network (LAN) from other untrusted networks, typically the public Internet. DMZs are also called perimeter networks or shielded subnets.
Any service provided to users on the public Internet must be placed in the DMZ network. The servers, resources and external services are usually located there. Some of the more common services include the web, email, domain name system, file transfer protocol, and proxy servers.
The servers and resources of the DMZ are accessible from the Internet, but the rest of the internal local network remains inaccessible. This approach provides an additional layer of security to the local network as it restricts an attacker’s ability to directly access internal servers and data from the Internet.
Hackers and cybercriminals can reach systems running services on DMZ servers. These servers must be hardened to withstand constant attacks. The term DMZ originates from the geographic buffer zone established between North Korea and South Korea at the end of the Korean War.
Why are DMZs important?
DMZs provide a level of network segmentation that helps protect internal corporate networks. These subnets restrict remote access to internal servers and resources, making it difficult for attackers to access the internal network. This strategy is useful both for individual use and for large organizations.
Businesses place applications and servers exposed to the Internet in a DMZ, separating them from the internal network. The DMZ isolates these resources so that, if compromised, the attack is unlikely to cause exposure, damage, or loss.
How does a DMZ work?
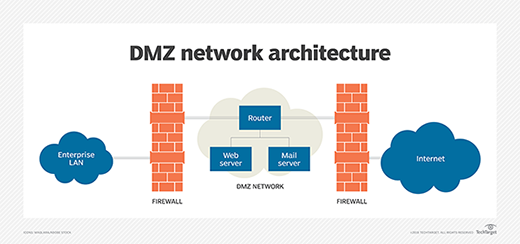
DMZs function as a buffer zone between the public Internet and the private network. The DMZ subnet is deployed between two firewalls. All incoming network packets are then filtered using a firewall or other security device before arriving at the servers hosted in the DMZ.
If better prepared malicious actors pass through the first firewall, then they must gain unauthorized access to DMZ services before they can cause damage. These systems are likely to be hardened against such attacks.
Finally, assuming threat actors with sufficient resources take control of a system hosted in the DMZ, they still need to break through the internal firewall before they can reach sensitive corporate resources. Determined attackers can penetrate even the most secure DMZ architecture. However, an attacked DMZ will set off alarms, giving security professionals enough warning to prevent a complete breach of their organization.
What are the advantages of using a DMZ?
The main advantage of a DMZ is that it gives users of the public Internet access to certain secure services, while maintaining a buffer between these users and the private internal network. This pad has several safety benefits, including the following:
- Access control. A DMZ network provides access control to services outside of an organization’s network perimeters that are accessed from the Internet. It simultaneously introduces a level of network segmentation that increases the number of obstacles a user must bypass before accessing an organization’s private network. In some cases, a DMZ includes a proxy server, which centralizes the flow of internal Internet traffic – usually that of employees – and simplifies the recording and monitoring of that traffic.
- Network recognition prevention. A DMZ also prevents an attacker from delineating potential targets within the network. Even if a system within the DMZ is compromised, the internal firewall still protects the private network, separating it from the DMZ. This configuration makes external active recognition more difficult. Although the DMZ’s servers are publicly exposed, they are backed by another layer of protection. The public face of the DMZ prevents attackers from seeing the contents of the internal private network. If the attackers manage to compromise the servers in the DMZ, they are still isolated from the private network by the internal barrier of the DMZ.
- Internet Protocol (IP) spoofing protection. In some cases, attackers attempt to bypass access control restrictions by spoofing an authorized IP address to impersonate another device on the network. A DMZ can block potential IP spoofers, while another service on the network verifies the legitimacy of the IP address by testing whether it is reachable.
What are the DMZs for
DMZ networks have been an important part of corporate network security for almost as long as firewalls have been in use. They are deployed for similar reasons: to protect sensitive organizational systems and resources. DMZ networks are often used for:
- isolate and separate potential target systems from internal networks;
- reduce and control access to these systems by external users; and
- host company resources to make some of them available to authorized external users.
More recently, companies have chosen to use virtual machines or containers to isolate parts of the network or specific applications from the rest of the corporate environment. Cloud technologies have largely removed the need for many organizations to have internal web servers. Many external infrastructures that were once located in the company’s DMZ have migrated to the cloud, such as software as a service applications.
Architecture and design of DMZ networks
There are different ways of designing a network with a DMZ. The two basic methods are to use one or two firewalls, although most modern DMZs are designed with two firewalls. This approach can be extended to create more complex architectures.
A single firewall with at least three network interfaces can be used to create a network architecture containing a DMZ. The external network is formed by connecting the public Internet – through an Internet service provider connection – to the firewall on the first network interface. The internal network is formed from the second network interface and the DMZ network itself is connected to the third network interface.
Different sets of firewall rules to monitor traffic between Internet and DMZ, LAN and DMZ, and LAN and Internet tightly control which ports and types of traffic are allowed into the DMZ from the Internet, limit the connectivity to specific hosts in the internal network and prevent unsolicited connections to either the Internet or the internal local network from the DMZ.
The most secure approach to creating a DMZ network is a dual firewall configuration, in which two firewalls are deployed with the DMZ network positioned between them. The first firewall – also called the perimeter firewall – is configured to only allow external traffic destined for the DMZ. The second, or internal, firewall only allows traffic from the DMZ to the internal network.
The dual firewall approach is considered more secure because two devices must be compromised before an attacker can gain access to the internal LAN. Security controls can be set specifically for each network segment. For example, a network intrusion detection and prevention system located in a DMZ could be configured to block all traffic except secure requests from the hypertext transfer protocol to port 443 of the transmission control protocol. .
Examples of DMZ
Some of the different ways that DMZs are used are as follows:
- Cloud services. Some cloud services, such as Microsoft Azure, use a hybrid security approach in which a DMZ is implemented between an organization’s local network and the virtual network. This method is typically used in situations where the organization’s applications run partly on-premises and partly on the virtual network. It is also used when outbound traffic needs to be audited or when granular traffic control is required between the virtual network and the on-premises data center.
- Home networks. A DMZ can also be useful in a home network where computers and other devices are connected to the Internet using a broadband router and configured in a local area network. Some home routers include a DMZ host function. This can be contrasted with the DMZ subnet used in organizations with many more devices than in a home. The DMZ host function designates a device on the home network to operate outside the firewall, where it acts as the DMZ while the rest of the home network is inside the firewall. In some cases, a game console is chosen to be the DMZ host so that the firewall does not interfere with games. Additionally, the console is a good candidate for a DMZ host because it probably contains less sensitive information than a personal computer.
- Industrial control systems (ICS). DMZs offer a potential solution to the security risks of ICS. Industrial equipment, such as turbine engines or ICSs, are merged with information technology (IT), which makes production environments smarter and more efficient, but also creates a greater surface of threat. Most industrial or operational technology (OT) equipment connected to the Internet is not designed to handle attacks in the same way as computing devices. A DMZ can provide increased network segmentation which can make it more difficult for ransomware or other network threats to bridge the gap between computer systems and their more vulnerable OT counterparts.
Take-out
A DMZ is a fundamental part of network security. These subnets create a layered security structure that reduces the risk of attack and the severity if it occurs. They are used to isolate the outward facing applications of an enterprise from the corporate network. If a system or application faces the public Internet, it must be placed in a DMZ.
Learn how a jar of honey can be placed in the DMZ to attract malicious traffic, move it away from the internal network and let IT investigate its behavior.
Source link