
[ad_1]

In a report released Friday, Google points out that it's important to tie a phone to an account when it comes to fighting the diversion of attempts to hijack automated bot attempts, phishing and targeted attacks.
An email address is at the center of our online lives, critical for creating accounts for web services and for receiving communications of a more or less sensitive nature.
In addition, providers of a large number of services, such as Google and Microsoft, have opted for single sign-on with the same username and password to access all services from the same provider . In addition, these accounts can be used to register or connect to third-party services.
It is no wonder that email accounts are coveted by hackers. Hundreds of thousands of account piracy attempts occur every day and companies like Google have developed defense systems against these threats.
Proactive anti-piracy protection
Adding a recovery phone number to the Google Account appears to be an effective way to gain against takeover attacks, especially if they are not targeted.
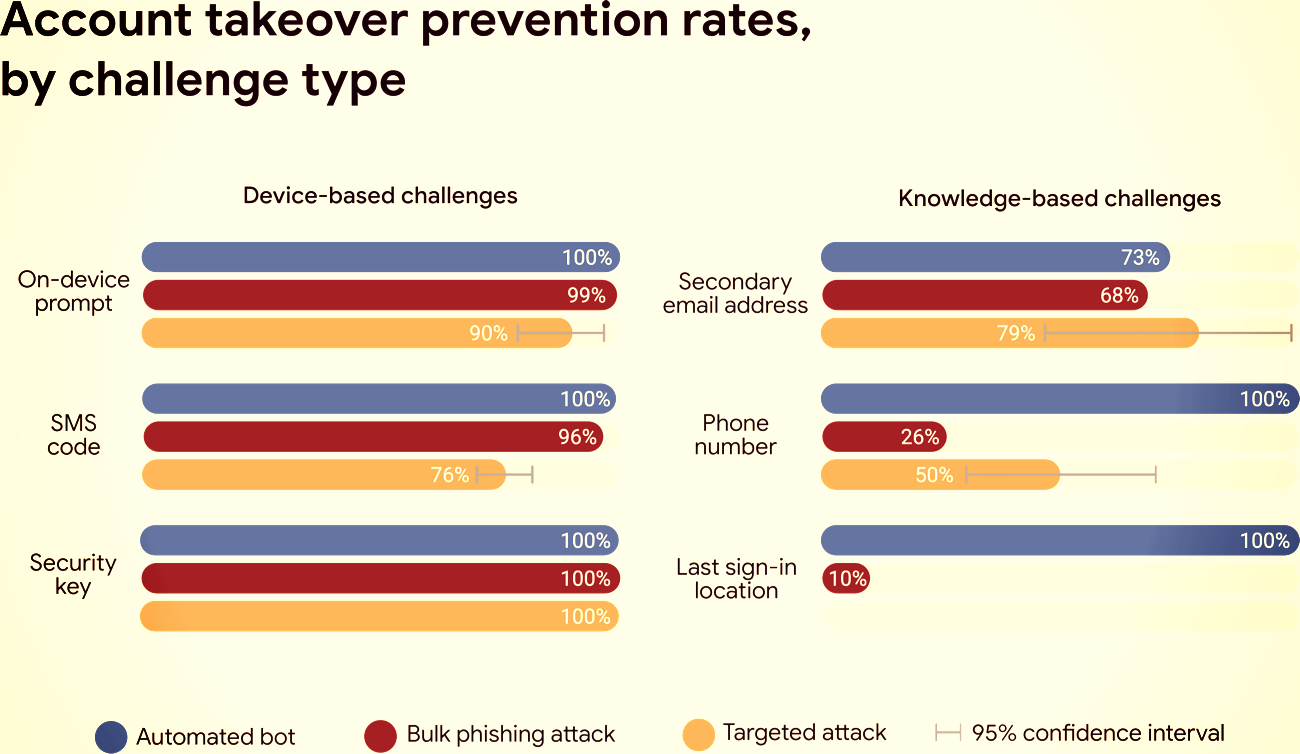
A study conducted by university researchers shows that when a Google account was associated with a phone, takeover prevention rates increased to 100% in the case of automated robots and reached 99% with banal phishing, and up to 90% with targeted attacks.
The research took into account more than 350,000 hacking attempts on a sample of 1.2 million users.
Google proactively secures user accounts and relies on its routine to determine the legitimacy of a passively connecting attempt. Among the signals used, there is the origin of the connection request, which includes both the device and the location.
In layman's terms, when users log on to their accounts from a different device or location, they are asked to prove that they are the rightful owner in solving a second challenge d & # 39; authentication.
When a suspicious connection is detected, users go through an additional verification step, which can be knowledge based (answering security questions, providing a phone number or recovery email address) or based on a device (prove access to a registered device).
The device beats knowledge-based challenges
According to a study by researchers at the University of New York and Google, real-world efforts to hijack a Google account were mostly ineffective in addressing the issues posed by the devices.
On the machine, a protection measure allowing the connection by confirming it over the phone had a 100% success rate against automated robots, 99% against mass phishing attacks and 90% against targeted account attacks. (ATA).
More successful was to authorize the connection with a security key. When this protection was enabled, all ATA attempts failed because the physical device was required for the connection process to continue.
Unfortunately, security keys add frictions to the authentication challenge that most users are unwilling to accept. This is why they are typically used by a category of users more likely to be victims of a targeted attack. For most users, even having the phone on hand is not always possible.
The weakest form of protection resulting from the study was SMS-based common authentication, which can be rolled back if the attacker in an intermediate position implements a live phishing attack, intercepts requests, and performs validity checks in real time.
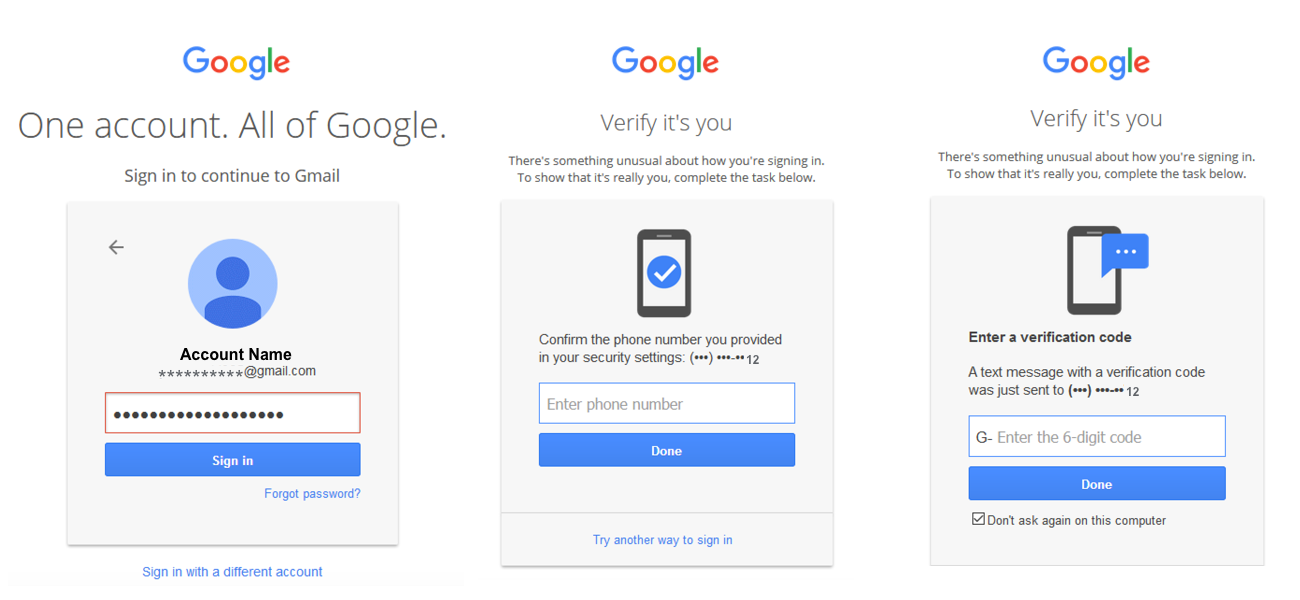
"If you've connected to your phone or set up a recovery phone number, we can provide a level of protection similar to 2-step verification via device-based challenges," say Google researchers.
The alternative to not having a phone connected to the Google account is that the recovery must be based on lower challenges, based on knowledge, that can be known to the attacker, or very easy to detect. Although it works against automated robots, phishing can be effective in 90% of cases.
If you do not have a recovery phone number, we may fall back on lower knowledge challenges, such as recalling your last logon location. This is an effective defense against robots, but the rate of protection against phishing can go down to 10%. The same vulnerability exists for targeted attacks. This is because phishing pages and targeted attackers may cause you to reveal any additional credentials that we may request.
It is important to note that Google provides users with other ways to protect their accounts from attempts to take control. S & # 39; s tap an authentication application that generates codes for connecting to the second factor and using one-time backup codes are also available options. However, both solutions are considered less convenient from the point of view of the average user because the process takes longer.
[ad_2]
Source link