[ad_1]
After the Specter vulnerability announced in January by Google, the Chrome browser received an upgrade called site isolation in its kernel to avoid this vulnerability.

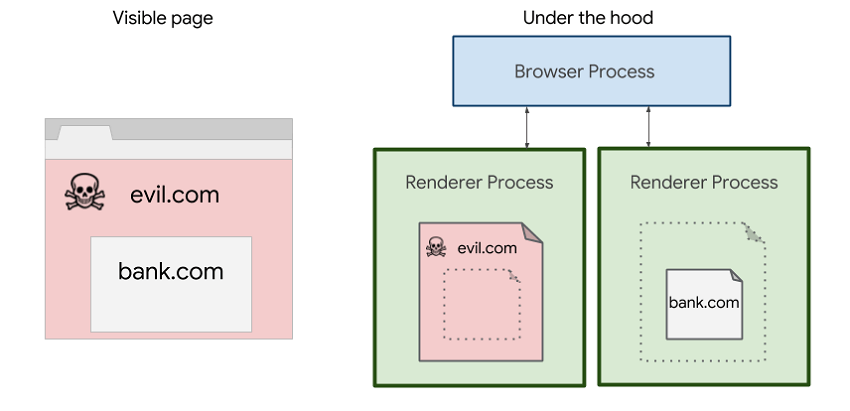
Since its release Google Chrome Browser, its way of working was a little different from other browsers, since when the program runs, it does not work. It's not just a process. For security reasons, the load is divided into several processes so that there is no risk of leakage information from one tab to the other. Google has now introduced a stricter version of the isolation of this site to make it safer than the Specter attack, discovered in January in collaboration with other researchers
The first version of the stricter (site isolation)) was released in May with Chrome version 67, but it was not turned on by itself. But the new feature is now activated in 99% of users between Windows, Mac, Linux and Chrome OS.
Technology companies that manufacture processors, operating systems and browsers worked together to prevent vulnerability, through which we can access pbadwords or encryption keys
Site application site is a big change for the browser. Modifies the rendering, which translates the code of a page into the final result we see. With site isolation, Chrome separates rendering engines into separate processes for added security. Unfortunately, it consumes more RAM, up to 13% more
"Our team is working intensively to optimize resource consumption while maintaining security and speed.We are also working on the Android version, which is not yet available, "says Reis, a member of the Chrome development team
Isolation of the site: A new way to protect Chrome from Vulnerability Specter was last modified: July 12, 2018, 14:07 pm by SecNews
[ad_2]
Source link