
[ad_1]

Google researchers detailed a sophisticated hacking operation that exploited vulnerabilities in Chrome and Windows to install malware on Android and Windows devices.
Some of the exploits were zero days, meaning they targeted vulnerabilities that at the time were unknown to Google, Microsoft, and most outside researchers (both companies have since patched security holes). Hackers delivered the exploits through waterhole attacks, which compromise sites frequented by targets of interest and bind the sites with code that installs malware on visitors’ devices. The trapped sites used two operating servers, one for Windows users and one for Android users.
Not your ordinary hackers
Using complex, zero-day infrastructure is not in itself a sign of sophistication, but it does show above-average skills from a professional team of hackers. Combined with the robustness of the attack code – which successfully chained several exploits – the campaign demonstrates that it was carried out by a “highly sophisticated actor”.
“These exploit chains are designed to be efficient and flexible due to their modularity,” wrote a researcher from the Google Project Zero Exploit research team. “This is a well-designed complex code with a variety of innovative logging methods, mature logging, sophisticated and calculated post-logging techniques, and high volumes of anti-scan and targeting checks. We believe that teams of experts have designed and developed these exploit chains. “
The modularity of payloads, interchangeable operating chains, as well as logging, targeting and operation maturity also set the campaign apart, the researcher said.
The four zero days operated were:
- CVE-2020-6418 – Chrome vulnerability in TurboFan (fixed in February 2020)
- CVE-2020-0938 – Font Vulnerability on Windows (Fixed April 2020)
- CVE-2020-1020 – Font Vulnerability on Windows (Fixed April 2020)
- CVE-2020-1027: Windows CSRSS vulnerability (fixed in April 2020)
Attackers obtained remote code execution by exploiting Chrome’s zero day and several recently patched Chrome vulnerabilities. Everyday Zero has been used against Windows users. None of the attack chains targeting Android devices operated on zero day, but researchers at Project Zero said it was likely that attackers had zero day Android.
The diagram below gives a visual overview of the campaign, which took place in the first quarter of last year:
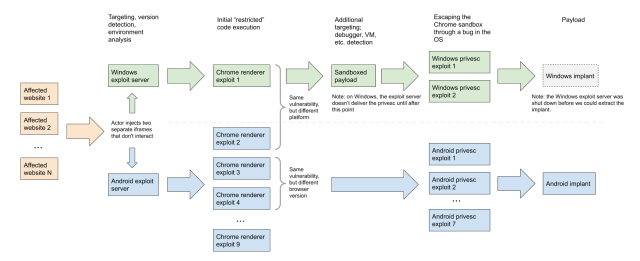
In all, Project Zero released six installments detailing the exploits and post-exploit payloads discovered by researchers. Other parts describe a Chrome infinity bug, Chrome exploits, Android exploits, post-Android operating payloads, and Windows exploits.
The intention of the series is to help the security community as a whole fight more effectively against complex malware operations. “We hope this series of blog posts provide others with an in-depth look at the exploitation of a mature, presumably well-resourced real-world actor,” the Project Zero researchers wrote.
[ad_2]
Source link