
[ad_1]

Microsoft has posted an advisory for another Windows zero-day print spooler vulnerability tracked as CVE-2021-36958 which allows local attackers to gain SYSTEM privileges on a computer.
This vulnerability is part of a class of bugs known as “PrintNightmare”, which abuses Windows print spooler configuration settings, print drivers, and Windows Point and Print functionality.
Microsoft released security updates in July and August to address various vulnerabilities in PrintNightmare.
However, a vulnerability revealed by a security researcher Benjamin Delpy still allows malicious actors to quickly gain SYSTEM privileges by simply connecting to a remote print server, as shown below.
This vulnerability uses the CopyFile registry directive to copy a DLL file that opens a command prompt to the client with a print driver when you connect to a printer.
Although recent security updates from Microsoft have changed the new printer driver installation procedure to require administrator privileges, you will not be required to enter administrator privileges for yourself. connect to a printer when this driver is already installed.
Additionally, if the driver exists on a client and therefore does not need to be installed, connecting to a remote printer will still execute the CopyFile directive for non-administrator users. This weakness allows the Delpy DLL to be copied to the client and executed to open a SYSTEM level command prompt.
Microsoft publishes advisory on CVE-2021-36958
Today Microsoft issued an advisory on a new Windows print spooler vulnerability identified as CVE-2021-36958.
“A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations,” read advisory CVE-2021-36958.
“An attacker who successfully exploited this vulnerability could execute arbitrary code with SYSTEM privileges. An attacker could then install programs, view, modify or delete data, or create new accounts with full user rights.”
“The workaround for this vulnerability is to stop and disable the Print Spooler service.”
Will Dormann, a vulnerability analyst for CERT / CC, told BleepingComputer that Microsoft has confirmed that CVE-2021-36958 is the PoC exploit shared by Delpy on Twitter and described above.
In the advisory, Microsoft attributes the bug to Victor mata from FusionX, Accenture Security, which also discovered the bug in December 2020.
Hey guys, I reported the vulnerability on December 20 but did not disclose any details at the request of MSRC. It seems they recognized it today due to recent events with the print spooler.
– Victor Mata (@offenseindepth) August 11, 2021
Oddly, Microsoft has classified this as a remote code execution vulnerability, even though the attack must be performed locally on a computer.
When BleepingComputer asked Dormann to clarify if this was incorrect labeling, we were told “this is clearly local (LPE)” based on the CVSS score: 3.0 7.3 / 6, 8.
“They just recycled” Remote code execution vulnerability exists when Windows Print Spooler service improperly performs privileged file operations “: https://google.com/search?q=%22A+.” Dormann told BleepingComputer.
Microsoft will likely update its advisory over the next few days to change its “impact” rating to “Elevation of Privilege”.
CVE-2021-36958 Vulnerability Mitigation
Microsoft has not yet released a security update for this vulnerability, but states that you can suppress the attack vector by disabling the print spooler.
Since disabling the print spooler will prevent your device from printing, a better method is only to allow your device to install printers from authorized servers.
This restriction can be done using the ‘Package Point and print – Approved servers’ Group Policy, preventing non-administrative users from installing print drivers using Point and Print unless the server printing is not on the approved list.
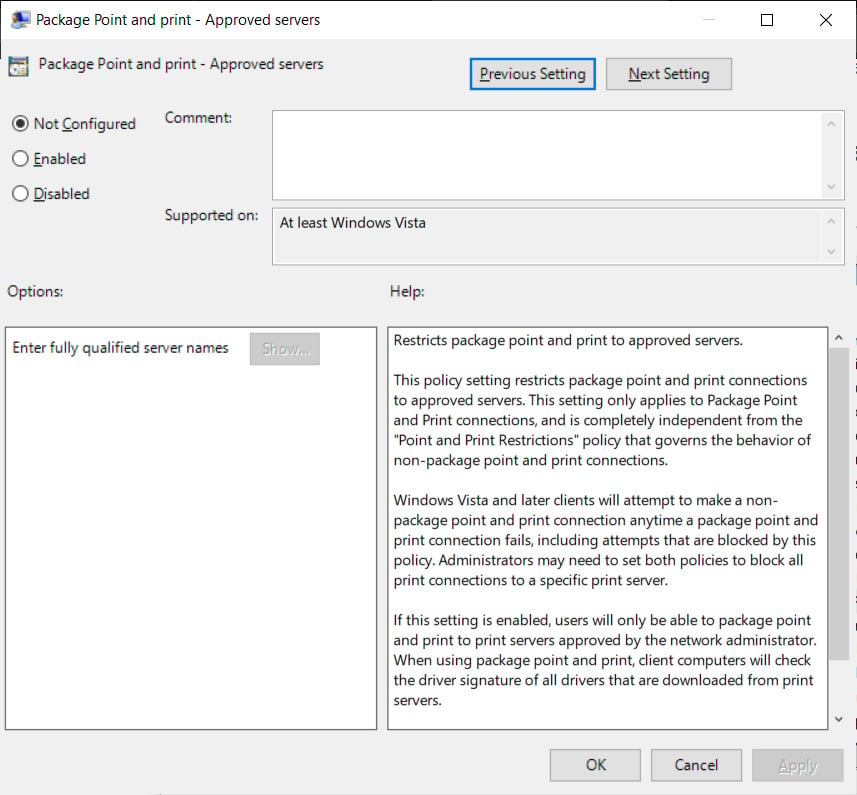
To enable this policy, launch the Group Policy Editor (gpedit.msc) and navigate to User configuration > Administrative Templates > Control Panel > Printers > Pointing and Printing Packages – Trusted Servers.
When you toggle the policy, enter the list of servers you want to allow to use as a print server, and then tap Okay to activate the policy. If you don’t have a print server on your network, you can enter a fake server name to enable the feature.
Using this Group Policy will provide the best protection against CVE-2021-36958 exploits but will not prevent malicious actors from taking control of an authorized print server with malicious drivers.
[ad_2]
Source link