
[ad_1]
Cyber attackers take full advantage of slow remediation or mitigation processes on Microsoft Exchange Server, with attack rates doubling every few hours.
According to Check Point Research (CPR), threat actors are actively exploiting four zero-day vulnerabilities addressed with emergency fixes released by Microsoft on March 2 – and attack attempts continue to increase.
Over the past 24 hours, the team has observed “attempts to exploit organizations doubling every two to three hours.”
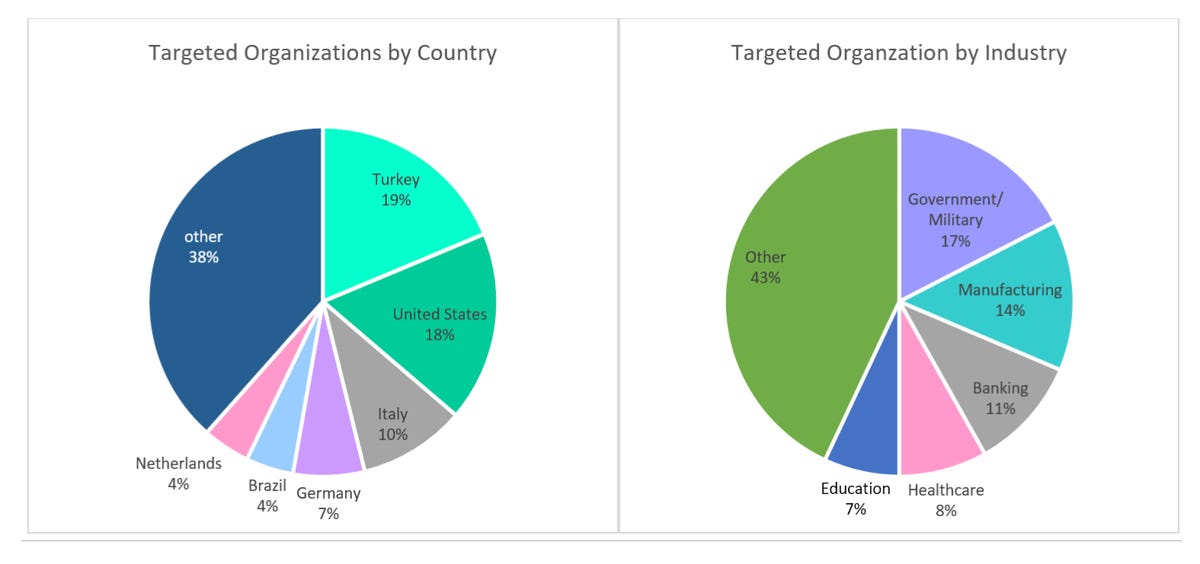
The countries most affected by attempted attacks are Turkey, the United States and Italy, which respectively account for 19%, 18% and 10% of all attempted exploits tracked.
Government, military, manufacturing and then financial services are currently the most targeted sectors.
Palo Alto estimates that at least 125,000 servers remain unpaid around the world.
Critical vulnerabilities (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065) affect Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019.
Microsoft has released emergency out-of-band fixes to address security vulnerabilities – which can be exploited for data theft and server compromise – and previously attributed the active exploit to the Chinese group of advanced persistent threats ( APT) Hafnium.
Read on: Everything you need to know about the Microsoft Exchange Server hack
This week, ESET revealed that at least 10 APT groups have been linked to current attempts to exploit Microsoft Exchange Server.
On March 12, Microsoft said that a form of ransomware, known as DearCry, was now using server vulnerabilities in attacks. The tech giant claims that after the “initial compromise of unpatched on-premises Exchange servers”, ransomware is deployed to vulnerable systems, a situation reminiscent of the WannaCry outbreak in 2017.
“Compromised servers could allow an unauthorized attacker to extract your corporate emails and execute malicious code within your organization with elevated privileges,” commented Lotem Finkelsteen, Head of Threat Intelligence at Check Point. “Organizations at risk should not only take preventative action on their Exchange, but also scan their networks for real threats and assess all assets.”
Previous and related coverage
Do you have any advice? Get in touch securely via WhatsApp | Signal to +447713025499, or more to Keybase: charlie0
[ad_2]
Source link