
[ad_1]

Microsoft today shared details on how the SolarWinds hackers may have gone undetected by hiding their malicious activity in the networks of the hacked companies.
This previously unknown information was disclosed by security experts from the Microsoft 365 Defender research team, the Microsoft Threat Intelligence Center (MSTIC), and the Microsoft Cyber Defense Operations Center (CDOC).
The report they released earlier today shares new details regarding the activation of the second stage of Solorigate – the steps and tools used to deploy custom Cobalt Strike chargers (Teardrop, Raindrop and others) after giving up. the backdoor of the Solorigate (Sunburst) DLL.
SolarWinds Pirate Escape Tactics
As Microsoft’s security experts found, the hackers who orchestrated the SolarWinds attack exhibited a range of tactics, operational security, and anti-forensic behavior that dramatically reduced the ability of violated organizations to detect. their malicious actions.
“[T]he attackers behind Solorigate are skillful and methodical operators who follow Operational Security Best Practices (OpSec) to minimize traces, stay under the radar and avoid detection, ”Microsoft reveals.
“During our in-depth analysis of the attacker’s tactics, techniques, and procedures (TTPs) seen through the lens of Microsoft 365 Defender’s rich telemetry, we observed a few techniques worth revealing to help other defenders. to better respond to this incident and to use research tools such as Microsoft 365 Defender Advanced Search or Azure Sentinel Queries to find potential traces of past activity. “
Some examples of SolarWinds hacker escape tactics discovered and highlighted by Microsoft:
- Methodical avoidance of shared metrics for each compromised host by deploying custom Cobalt Strike DLL implants on each machine
- Camouflage and merge in the environment by renaming tools and binaries to match files and programs on the compromised device
- Disable event logging using AUDITPOL before hands-on keyboard activity and re-enable afterwards
- Creation of firewall rules to minimize outgoing packets for certain protocols before performing noisy network enumeration activities (removed after these operations are completed)
- Carefully plan lateral movement activities by first disabling security services on targeted hosts
- It is also believed to have used temporal correction to alter artifact timestamps and to exploited erasure procedures and tools to prevent the discovery of malicious DLL implants in the affected environments.
Additionally, Microsoft provides a list of the most fascinating and unusual Tactics, Techniques, and Procedures (TTPs) used in these attacks.
The company also said it “is actively working with MITER to ensure that any new techniques emerging from this incident are documented in future updates to the ATT & CK framework.”
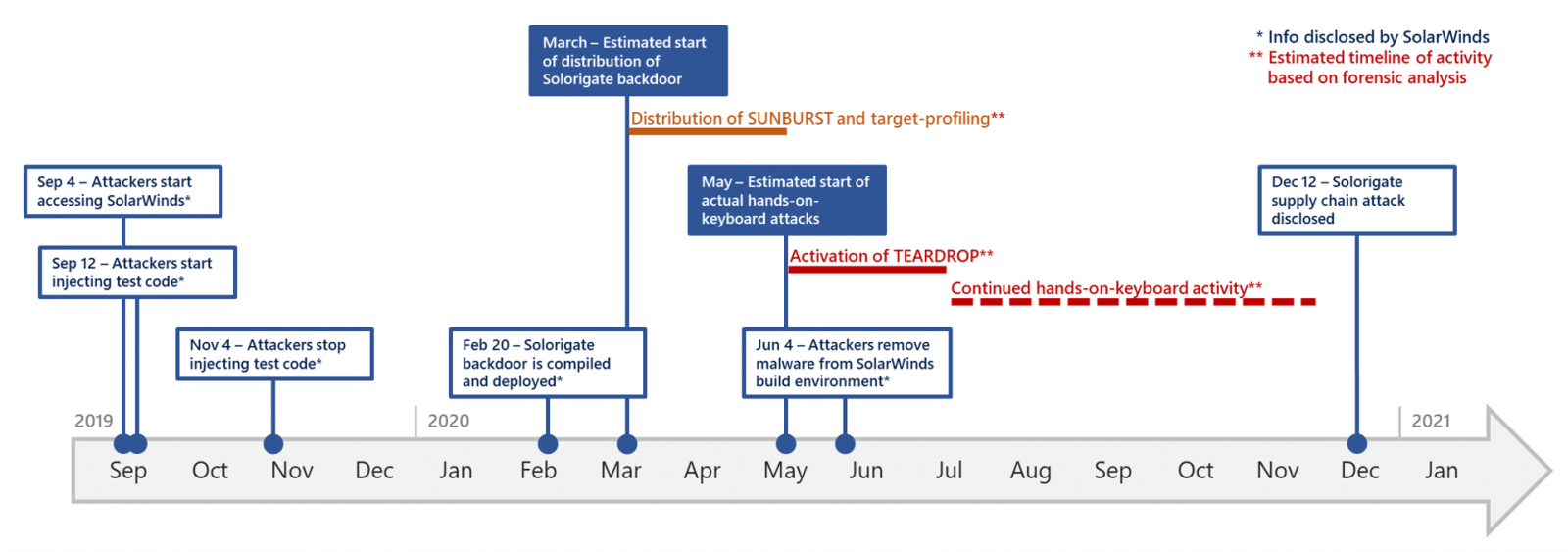
Timeline of supply chain attacks
A detailed timeline of these attacks shows that the Solorigate DLL backdoor was deployed in February and deployed to compromised networks in late March (SolarWinds also provided an overview of the attack timeline earlier this month).
After this step, the threat actor prepared the Cobalt Strike custom implants and selected targets of interest until early May, when the practical attacks likely began.
“The removal of the backdoor build function and compromised code from the SolarWinds binaries in June could indicate that, by that point, the attackers had reached a sufficient number of good targets and that their focus had shifted from deployment to enabling the backdoor (Stage 1) to be operational on selected victim networks, continuing the attack with hands-on keyboard activity using Cobalt Strike implants (stage 2), ”adds Microsoft.
Microsoft uncovered these new details during its ongoing investigation into the SolarWinds supply chain attack orchestrated by threat actor followed like StellarParticle (CrowdStrike), UNC2452 (FireEye), SolarStorm (Palo Alto Unit 42) and Dark Halo (Volexity).
Although the identity of the threatening actor remains unknown, a joint statement released by the FBI, CISA, ODNI and NSA earlier this month indicates that it is likely an Advanced Persistent (APT) group. Threat) supported by Russia.
Kaspersky also linked the SolarWinds hackers to the Russian hacking group Turla after finding that the Sunburst backdoor had overlaps in functionality with the Kazuar backdoor tentatively linked to Turla.
[ad_2]
Source link