
[ad_1]

Newly detected Android malware, some of which spread through the Google Play Store, uses a new way to override harvesting login information from more than 100 banking and cryptocurrency apps.
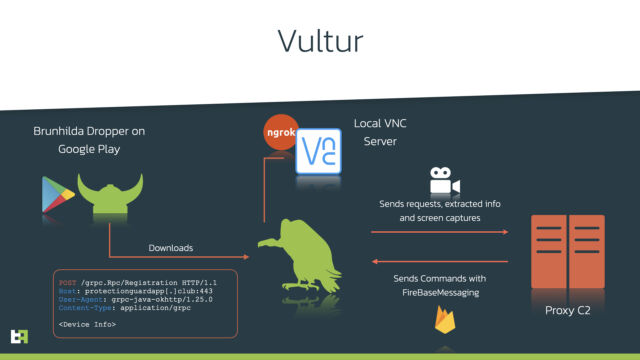
The malware, which researchers at Amsterdam-based security firm ThreatFabric call Vultur, is one of the first Android threats to record a device screen whenever one of the targeted apps is opened. Vultur uses an actual implementation of the VNC screen sharing app to mirror the screen of the infected device to a server controlled by an attacker, ThreatFabric researchers said.
Threat Fabric

Threat Fabric
The next level
The typical operating mode for Android-based bank fraud malware involves overlaying a window on the login screen presented by a targeted application. The “overlay,” as these windows are commonly referred to, appear identical to the banking app user interface, making victims feel like they are entering their credentials into trusted software. The attackers then collect the credentials, enter them into the app running on another device, and withdraw money.
“Banking threats on the mobile platform are no longer based solely on well-known overlay attacks, but are evolving into RAT-like malware, inheriting useful tricks such as detecting top apps to boot. screen recording, ”ThreatFabric researchers wrote of the new Vultur approach in a post.
They continued:
This takes the threat to another level, as such features open the door to on-device fraud, bypassing MO-based detection of phishing that requires fraud to be performed from a new device: with Vultur , fraud can occur on the infected device of the victim. These attacks are scalable and automated since the actions to perform a fraud can be scripted on the malware backend and sent as sequenced commands.
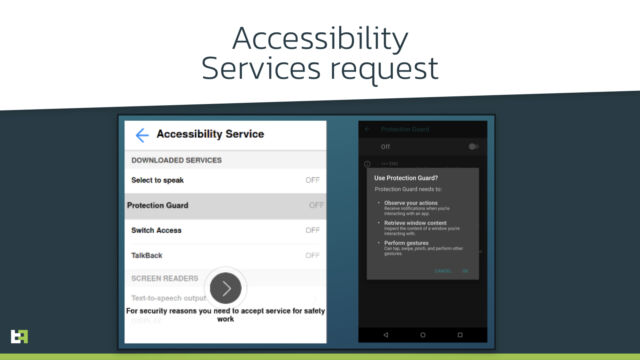
Vultur, like many Android banking Trojans, relies heavily on the accessibility services built into the mobile operating system. During the first installation, Vultur abuses these services to obtain the necessary permissions to operate. To do this, the malware uses an overlay from other malware families. Therefore, Vultur monitors all requests that trigger accessibility services.
Threat Fabric
Stealth and more
The malware uses the services to detect requests from a targeted application. The malware also uses the services to prevent removal of the application through traditional measures. Specifically, whenever the user tries to access the app details screen in Android settings, Vultur automatically clicks the back button. This prevents the user from accessing the uninstall button. Vultur also hides his icon.
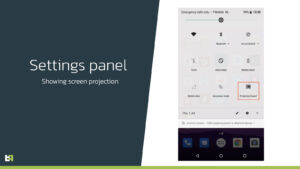
Another way the malware remains stealthy: the trojanized apps that install it are full-featured programs that actually provide real services, such as fitness tracking or two-factor authentication. Despite attempts at cover-up, however, the malware at least provides a telltale sign that it is running – whatever trojan app Vultur installed will appear in the Android notification panel as projecting the screen. .
Threat Fabric
Once installed, Vultur starts screen recording, using the VNC implementation of Alpha VNC. To provide remote access to the VNC server running on the infected device, the malware uses ngrok, an application that uses an encrypted tunnel to expose local systems hidden behind firewalls to the public internet.
The malware is installed by a Trojan horse application called a dropper. So far, ThreatFabric researchers have found two Trojan horse apps in Google Play that install Vultur. They had a combined facility of around 5,000, which led researchers to estimate the number of Vultur infections to be in the thousands. Unlike most Android malware, which relies on third-party dropper droppers, Vultur uses a custom dropper now called Brunhilda.
“This dropper and Vultur are both developed by the same group of threat actors,” the ThreatFabric researchers wrote. “The choice to develop its own private Trojan, instead of renting third-party malware, demonstrates a strong motivation of this group, associated with the overall level of structure and organization present in the bot as well as in the server code. . “
Researchers have found that Brunhilda has been used in the past to install various Android banking malware called Alien. In total, researchers estimate that Brunhilda has infected more than 30,000 devices. The researchers based the estimate on malicious apps previously available on the Play Store, some with more than 10,000 installations each, as well as figures from third-party markets.
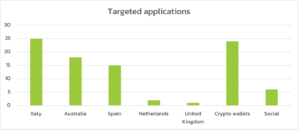
Vultur is programmed to record screens when any of the 103 Android banking or cryptocurrency apps are running in the foreground. Italy, Australia and Spain are the countries most targeted by banking institutions.
Threat Fabric
Besides banking and cryptocurrency apps, the malware also collects credentials for Facebook, WhatsApp Messenger owned by Facebook, TikTok, and Viber Messenger. The collection of credentials for these applications is done through traditional keystroke logging, although the ThreatFabric message does not explain why.
While Google has removed all Play Market apps known to contain Brunhilda, the company’s track record suggests new trojanized apps are likely to emerge. Android users should only install apps that provide useful services and, even then, only apps from known publishers, if possible. People should also pay close attention to user ratings and app behavior to spot signs of maliciousness.
[ad_2]
Source link