
[ad_1]

Researchers have discovered a software supply chain attack used to install surveillance malware on the computers of online gamers.
The unknown attackers target certain users of NoxPlayer, a software that emulates the Android operating system on PC and Mac. People mainly use it for playing Android mobile games on these platforms. NoxPlayer maker BigNox claims the software has 150 million users in 150 countries.
Poison the well
Security firm Eset said Monday that the BigNox software distribution system had been hacked and used to deliver malicious updates to some users. The first updates were delivered last September by manipulating two files: BigNox’s main binary Nox.exe and NoxPack.exe, which downloads the update itself.
“We have enough evidence to say that the BigNox infrastructure (res06.bignox.com) was compromised to host malware, and also to suggest that their HTTP API infrastructure (api.bignox.com) could have been compromised, ”Ignacio, malware researcher at Eset Sanmillan wrote. “In some cases, additional payloads were downloaded by the BigNox updater from servers controlled by the attackers. This suggests that the URL field, provided in the BigNox API response, has been tampered with by attackers. “
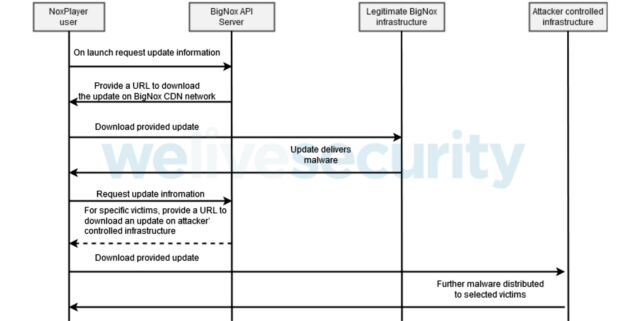
In a nutshell, the attack works this way: upon launch, Nox.exe sends a request to a programming interface to query for update information. The BigNox API server responds with update information that includes a URL where the legitimate update is believed to be available. Eset assumes that the legitimate update may have been replaced by malware or, alternatively, a new filename or URL has been introduced.
The malware is then installed on the target’s machine. Malicious files are not digitally signed like legitimate updates are. This suggests that the BigNox software building system is not compromised; only updating systems are. The malware performs limited recognition on the targeted computer. Attackers also tailor malicious updates to specific targets of interest.
The BigNox API server responds to a specific target with update information that indicates the location of the malicious update on a server controlled by an attacker. The observed intrusion flow is illustrated below.
Eset
Sanmillan, malware researcher at Eset, added:
- Legitimate BigNox infrastructure provided malware for specific updates. We observed that these malicious updates did not occur until September 2020.
- Additionally, we observed that for specific victims, malicious updates were downloaded from an infrastructure controlled by the attackers thereafter and throughout late 2020 and early 2021.
- We are confident that these additional updates have been made by
Nox.exeprovide parameters specific toNoxPack.exe, suggesting that the BigNox API mechanism may have also been compromised to deliver personalized malicious updates.- It could also suggest the possibility that the victims were subjected to a MitM attack, although we believe that this hypothesis is unlikely since the victims we have discovered are in different countries and the attackers already had a foot on it. BigNox infrastructure.
- In addition, we were able to reproduce the download of malware samples hosted on
res06.bignox.comfrom a test machine and using https. This eliminates the possibility that a MitM attack was used to tamper with the update binary.
Eset observed three variants of malware being installed. There is no sign that any of the malware is attempting to make financial gains on behalf of the attackers. This led the security company to believe that the malware was being used to monitor targets.
Sanmillan said that out of more than 100,000 Eset users who have NoxPlayer installed, only five of them received a malicious update. The numbers underline how targeted the attacks are. The targets are located in Taiwan, Hong Kong and Sri Lanka.
Sanmillan said Eset contacted BigNox with the results and the software maker denied being affected. BigNox representatives did not respond to emails requesting comment for this post.
Anyone who has used NoxPlayer in the past five months should take the time to carefully inspect their systems for any signs of compromise. Monday’s post provides a list of files and settings that will indicate when a computer has received a malicious update. Although Eset’s article only refers to the Windows version of the software, there is currently no way to rule out the possibility that macOS users have also been targeted.
[ad_2]
Source link