[ad_1]

Another zero day vulnerability in Windows Print Spooler can give an attacker administrative privileges on a Windows machine through a remote server under the attacker’s control and the “Queue-specific files” feature.
Last month, a security researcher accidentally revealed a Windows zero-day print spooler vulnerability known as PrintNightmare that Microsoft tracks as CVE-2021-34527.
Exploitation of this vulnerability allows a malicious actor to increase his privileges on a machine or to execute code remotely.
Microsoft released a security update to address the vulnerability, but researchers have determined that the patch can be circumvented under certain conditions.
Since the patch was incomplete, security researchers have taken a close look at the Windows print APIs and have discovered other vulnerabilities affecting the Windows print spooler.
Remote print server used in the attack
Security researcher and creator of Mimikatz Benjamin Delpy publicly disclosed a new zero-day vulnerability that allows an attacker to easily gain SYSTEM privileges on a Windows machine through a remote print server under their control.
#nightmare print – Episode 4
Do you know what’s better than a legitimate Kiwi printer?
Another legitimate Kiwi printer …No prerequisites at all, you don’t even need to sign the drivers / package pic.twitter.com/oInb5jm3tE
– Benjamin Delpy (@gentilkiwi) July 16, 2021
In a conversation with BleepingComputer, Delpy said his exploit uses the “Queue Specific Files” feature of Windows Point and Print feature to automatically download and run a malicious DLL when a client connects to a server. printing under the control of an attacker.
“When installing the printer, a vendor-supplied installer application can specify a set of files, of any type, to associate with a particular print queue,” explains the documentation for Microsoft on the “Queue Specific Files” feature.
“The files are downloaded to every client that connects to the print server.”
To exploit the vulnerability, the researcher created an Internet-accessible print server with two shared printers that use the queue-specific files feature.
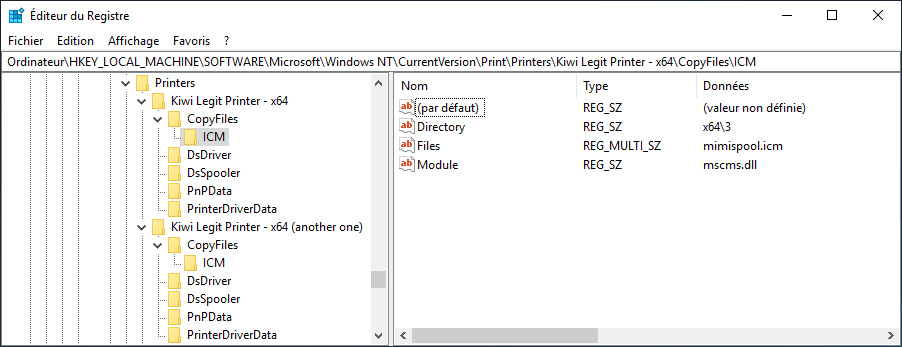
Source: Delpy
When running the malicious DLL, it will run with SYSTEM privileges and can be used to execute any command on the computer.
Will Dormann, a vulnerability analyst for CERT / CC, has published an advisory for this vulnerability which provides additional information.
“While Windows requires that the driver packages themselves be signed by a trusted source, Windows printer drivers can specify queue-specific files associated with device usage. For example, a shared printer might specify a CopyFiles guideline for arbitrary ICM files, ”explains the new CERT advisory.
“These files, which are copied with the digitally signed printer driver files, are do not covered by any signature requirement. That is, any file can be copied to a client system through the installation of the Point and Print printer driver, where it can be used by another printer with SYSTEM privileges. “
“This allows the LPE on a vulnerable system.”
What makes this vulnerability so dangerous is that it affects all current versions of Windows and allows a malicious actor to gain limited access to a network and instantly gain SYSTEM privileges on the vulnerable device.
With this access, malicious actors can spread laterally across the network until they gain access to a domain controller.
A video demonstrating this attack has been shared with BleepingComputer and posted below.
Delpy has created a publicly accessible remote print server that can be used to test the vulnerability demonstrated above.
Mitigating the new printer vulnerability
The good news is that Delpy and Dormann have shared two methods that can be used to mitigate this new “queue specific files” vulnerability.
These two methods are described in the CERT notice.
Option 1: Block outgoing SMB traffic at the edge of your network
Because Delpy’s public exploit uses a remote print server, you can block outgoing SMB traffic to prevent access to the remote computer.
However, Dormann states that MS-WPRN can also be used to install drivers without using SMB, and malicious actors could still use this technique with a local print server.
Therefore, this mitigation is not a foolproof method to block the exploit.
Option 2: Configure PackagePointAndPrintServerList
A better way to prevent this exploit is to restrict Point and Print to a list of trusted servers using the “Point and Print Packets – Trusted Servers” Group Policy.
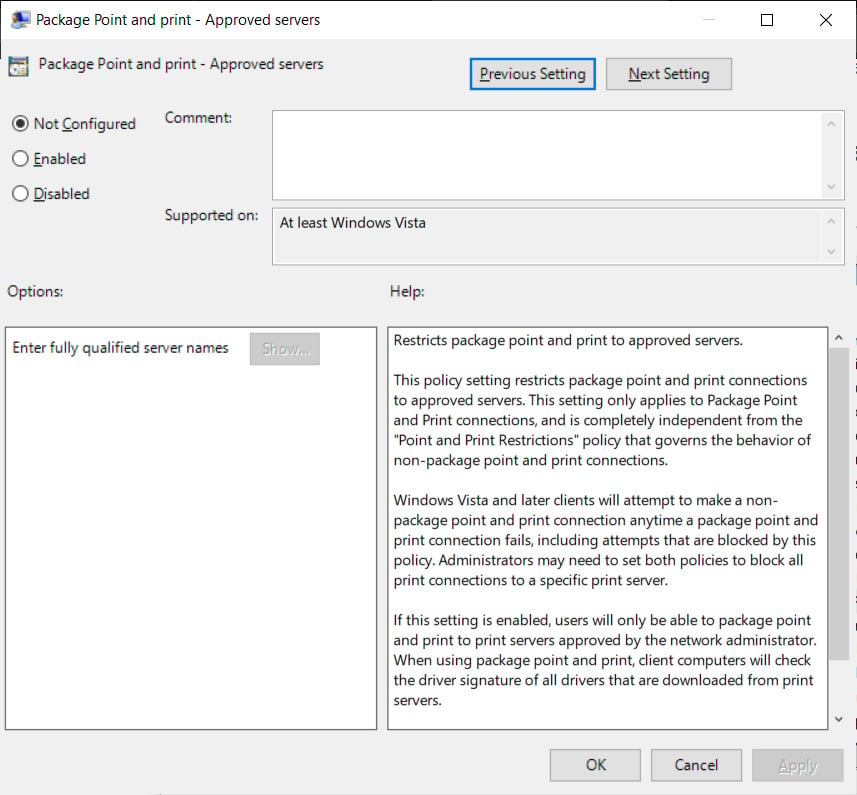
This policy prevents non-administrative users from installing print drivers using Point and Print unless the print server is on the approved list.
Using this Group Policy will provide the best protection against the known exploit.
BleepingComputer has contacted Microsoft regarding the issue but has not received a response.
[ad_2]
Source link