
[ad_1]

Just after a zero-day vulnerability on yesterday's Windows 10 privilege escalation, the same researcher released the exploit code for two other vulnerabilities today.
A security researcher named SandboxEscaper is known for his vulnerabilities and exploits of day zero for Microsoft. Just yesterday, the researcher published a local privilege escalation vulnerability that uses the Windows 10 Task Scheduler. When used, this vulnerability allows users to obtain permissions on files that are not available. 39 they would not normally have.
Today, SandboxEscaper has released a code that exploits two other vulnerabilities; a local privilege elevation vulnerability in the Windows error report (followed by CVE-2019-0863) and a sandbox escape vulnerability for Internet Explorer 11.
The only reason given for posting these vulnerabilities is the following post from SandboxEscaper's blog.
"There are two other bugs on github.
*** this industry ***. Anyway, I do not plan to make a career.
I hate everyone involved in this industry.
Everyone thinks that they know better. Everyone just likes to point fingers.
Bouquet of monkeys.
Goodbye"
At this point, users with the latest security updates from Microsoft are protected against CVE-2019-0863, but the status of IE bug 11 is unknown.
Internet Explorer 11 Sandbox Escape zero-day
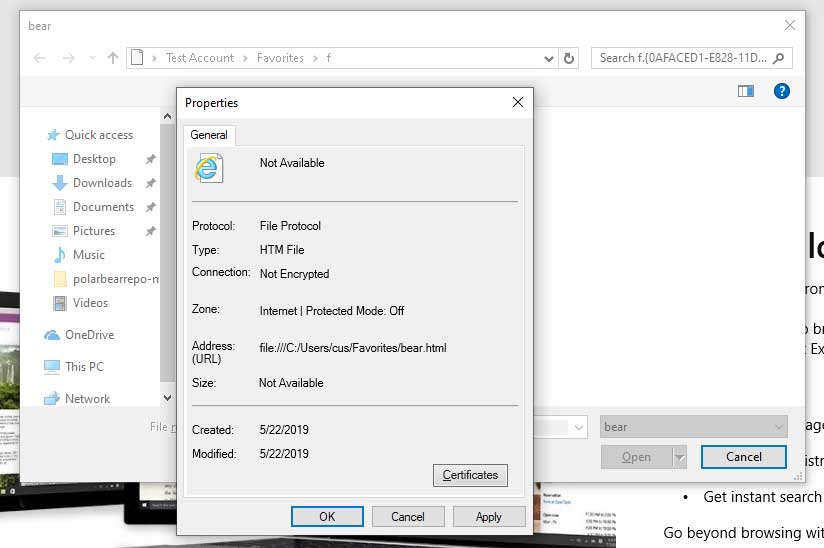
The first vulnerability published today could allow an attacker to inject a DLL into a specified Internet Explorer 11 process. When the injection works, it opens a file selector and an HTML page containing JavaScript.
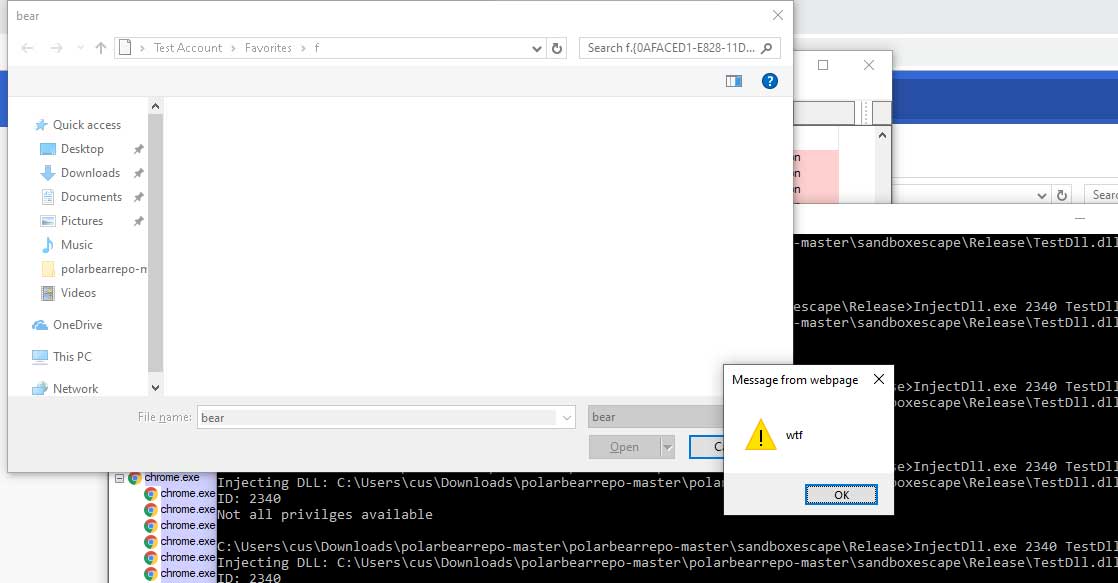
When you right-click the file picker, you can see that the exploit is disabled in Internet protected mode. This means that the JavaScript code would have been executed in this lower security context.
Windows LPE error report bug
The second security issue addressed by SandboxEscaper is called AngryPolarBearBug2 and is a local privilege elevation vulnerability exploiting a bug in the Windows Error Report. The vulnerability has been fixed this month and a credit for discovery and reporting has been assigned to Gal De Leon of Palo Alto Networks and Polar Bear, which SandboxEscaper sometimes uses as an alias and which is also the name of its repository GitHub with exploitation code.
To do this, it exploits a situation of critical competition between two function calls in order to create a hard link with a high authorization on a file at the choice of the attackers. This could allow the attacker to modify or delete a file that he / she does not normally have access to.
In SandboxEscapers PoC, they declare that when the exploit succeeds, the drive C: Windows System32 drivers pci.sys is writable by a non-administrator, which is not normally the case as shown below.
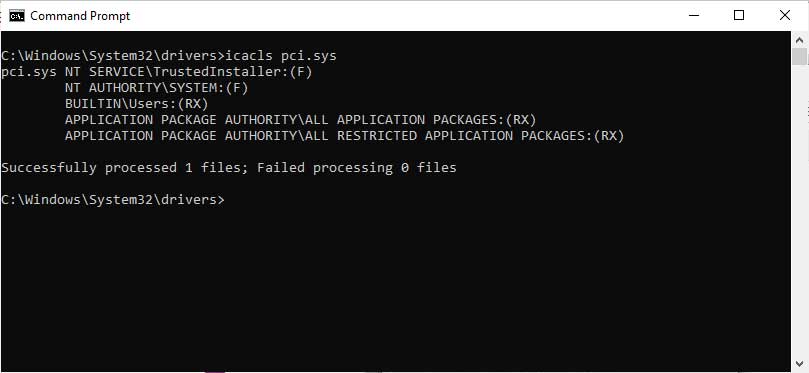
If successful, the exploit will allow a normal user to delete the PCI.sys file.
The good news is that this vulnerability is not easy to exploit. According to SandboxEscaper, the outbreak of the exploit can take up to 15 minutes, if at all.
It may take more than 15 minutes for the bug to fire. If it takes too much time, close the program, clean the reportarchive folder in programdata (this can mess up the timing if there are too many reports resulting from the execution of our poc too long), delete the folder c: blah. etc. .. could help.
"I suppose that a more determined attacker might perhaps improve reliability – it's just an incredibly small window into which we can win our race, I was not even sure I could manage it." To exploit at all. "
SandboxEscaper also indicates that the exploit has a better chance of success with more powerful computers and that even in this case, it can take a long time.
"The race condition is incredibly hard to win, I have not tested on any other configuration .. but you definitely need more processor cores and you may have to wait a few minutes for it to work (it can take very long …) Anyway … in a LPE scenario, time is not really a problem. "
BleepingComputer has not been able to trigger this vulnerability using SandboxEscaper's PoC.
Update [05.23.2019]: The AngryPolarBearBug2 bug is not a zero day. Security researcher Gal De Leon of Palo Alto Networks confirms that the exploit code is actually a proof of concept for CVE-2019-0863. De Leon is credited by Microsoft for reporting the bug, as well as Polar Bear, the name that Sandbox Escaper uses for its GitHub repository with operating code.
SandboxEscaper has released the exploit for CVE-2019-0863 (https://t.co/KZgdpeWBFr), also discovered by me 🙂
The race is quite difficult to win but possible, and provides a primitive to overwrite the DACL of an arbitrary file.– Gal De Leon (@galdeleon) May 23, 2019
[ad_2]
Source link