[ad_1]
It’s good when ransomware gangs have their bitcoin stolen, malware servers shut down, or forced to disband in some other way. We hang on to these occasional wins because history tells us that most lucrative ransomware collectives don’t go away until they reinvent themselves under a new name, with new rules, targets, and weapons. Indeed, some of the most destructive and costly ransomware groups are now in their third incarnation.
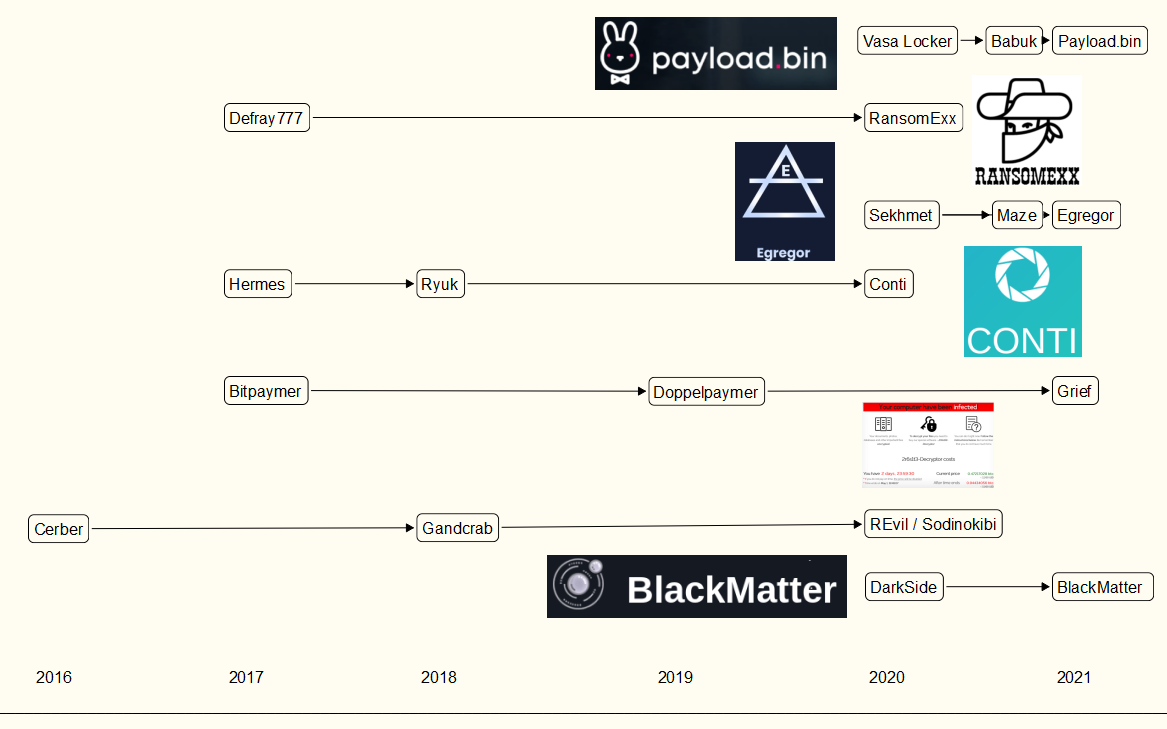
A rough timeline of major ransomware operations and their reputed links over time.
Reinvention is a basic survival skill in cybercrime. One of the oldest tricks in the book is to fake his demise or retirement and invent a new identity. One of the main purposes of such a subterfuge is to confuse investigators or temporarily direct their attention elsewhere.
Cybercriminal syndicates also perform similar disappearance acts whenever it suits them. These organizational reboots are an opportunity for ransomware managers to set new ground rules for their members, such as what types of victims are not allowed (e.g. hospitals, governments, critical infrastructure) or the amount of ransom payment an affiliate should expect the group to gain access to a new network of victims.
I’ve put the graphic above together to illustrate some of the more notable ransom gang reinventions of the past five years. What this doesn’t show is what we already know about the cybercriminals behind many of these seemingly disparate ransomware groups, some of which pioneered the ransomware space nearly a decade ago. We’ll explore this in more detail in the second half of this story.
One of the most intriguing and recent redesigns involves Dark side, the group that extorted a $ 5 million ransom from Colonial pipeline earlier this year, only to see much of it recovered in a US Department of Justice operation.
After acknowledging that someone had also grabbed their internet servers, DarkSide announced that it was falling back. But a little over a month later, a new ransomware affiliate program called BlackMatter emerged, and experts quickly determined that BlackMatter was using the same unique encryption methods DarkSide had used in their attacks.
DarkSide’s demise roughly coincided with that of the evil, a long-standing ransomware group that claims to have extorted more than $ 100 million from victims. The last great victim of REvil was Kaseya, a Miami-based company whose products help system administrators manage large networks remotely. This attack allowed REvil to deploy ransomware in up to 1,500 organizations that were using Kaseya.
REvil demanded $ 70 million to release a universal decryptor for all victims of the Kaseya attack. A few days later, President Biden would have said in russian President Vladimir Putin that it expects Russia to act when the United States shares information about specific Russians involved in ransomware activity.
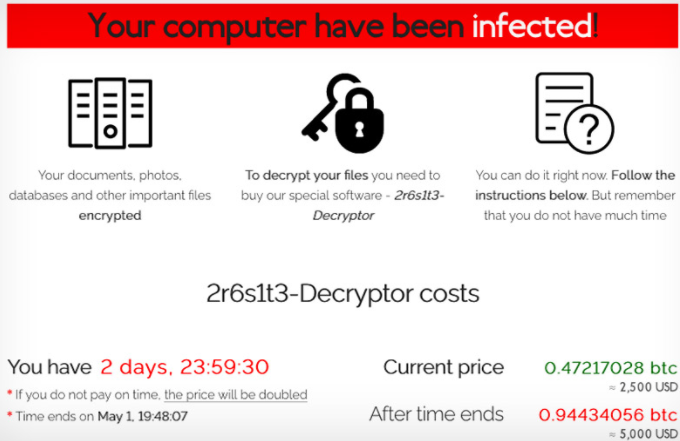
A ransom note REvil.
It is not known if this conversation sparked any action. But the shameful blog of REvil victims would disappear from the dark web four days later.
Mark Arena, CEO of cyber threat intelligence firm Intel 471, said it remains unclear whether BlackMatter is the REvil team operating under a new banner, or if this is just the reincarnation of DarkSide.
But one thing is clear, Arena said: “We will probably see them again unless they have been arrested.”
Likely, indeed. REvil is widely seen as a reboot of GandCrab, a prolific ransomware gang that boasted of extorting over $ 2 billion over 12 months before brutally shutting down in June 2019. “Gandcrab boasted.
And wouldn’t you know it: Researchers found that GandCrab shared key behaviors with Cerberus, a first ransomware-as-a-service operation that stopped claiming new victims around the same time GandCrab entered the scene.
GOOD MOURNING
The past few months have been a busy time for ransomware groups looking to rebrand. BipComputer recently reported that the new “Pain” starting the ransomware was just the last paint job of Double payer, a ransomware strain that shared most of its code with an earlier 2016 iteration called BitPaymer.
These three ransom operations come from a prolific cybercrime group known as TA505, “Indrik Spider”And (perhaps the most memorable) Evil Society. According to the security company CrowdStrike, Indrik Spider was formed in 2014 by former affiliates of the GameOver Zeus criminal network who called themselves internally “The Business Club”.
The Business Club was a notorious organized cybercrime gang from Eastern Europe accused of stealing more than $ 100 million from banks and businesses around the world. In 2015, the FBI offered a permanent bounty of $ 3 million for information leading to the capture of the head of the Business Club – Evgeniy Mikhailovich Bogachev. By the time the FBI put a price tag on his head, Bogachev’s Zeus Trojan and its later variants had been infecting computers for nearly a decade.

The alleged perpetrator of the ZeuS Trojan, Evgeniy Mikhaylovich Bogachev. Source: FBI
Bogachev was way ahead of his colleagues in the pursuit of ransomware. His Gameover Zeus Botnet was a peer-to-peer criminal machine that infected between 500,000 and one million Microsoft Windows computers. Throughout 2013 and 2014, PCs infected with Gameover were seeded with Cryptolocker, a widely copied early strain of ransomware believed to have been created by Bogachev himself.
CrowdStrike notes that soon after the group was formed, Indrik Spider developed his own custom malware called Dridex, which has become a major malware deployment vehicle that lays the foundation for ransomware attacks.
“Early versions of Dridex were primitive, but over the years malware has gotten more professional and sophisticated,” CrowdStrike researchers wrote. “In fact, Dridex’s operations were significant throughout 2015 and 2016, making it one of the most prevalent eCrime malware families. “
This CrowdStrike report was dated July 2019. In April 2021, security experts from Checkpoint software found that Dridex was still the most prevalent malware (for the second month in a row). Mainly distributed via well-crafted phishing emails – like a recent campaign that spoofed QuickBooks – Dridex often serves as the attacker’s initial fulcrum in enterprise-wide ransomware attacks, CheckPoint said.
REMARKS TO AVOID SANCTIONS
Another ransomware family linked to Evil Corp. and the Dridex gang is WastedLocker, which is the latest name in a ransomware strain that has changed its name several times since 2019. It was at this point that the Department of Justice awarded a $ 5 million bounty to the head of ‘Evil Corp. Foreign Assets Control Office (OFAC) said it was prepared to impose heavy fines on anyone who paid ransom to the cybercrime group.

The alleged leader of Evil Corp Maksim “Aqua” Yakubets. Image: FBI
In early June 2021, researchers discovered that the Dridex gang was once again attempting to transform in an attempt to evade US sanctions. The drama began when ransomware group Babuk announced in May that it was launching a new data extortion platform, which was intended to attract ransomware groups that did not yet have a blog where they can go. public shame on victims to pay by gradually releasing stolen data.
On June 1, Babuk changed the name of its leak site to Payload[dot]bin, and began to disclose the victim’s data. Since then, several security experts have spotted what they believe to be another version of WastedLocker disguised as payload.bin-branded ransomware.
“Looks like EvilCorp is trying to impersonate Babuk this time around”, wrote Fabien Ousar, technical director of a security company Emsisoft. “As Babuk releases its PayloadBin leak portal, EvilCorp is renaming WastedLocker once again as PayloadBin in an effort to get victims to violate OFAC regulations.”
Experts are quick to point out that many cybercriminals involved in ransomware activity are affiliated with more than one separate ransomware-as-a-service operation. Additionally, it is common for a large number of affiliates to migrate to competing ransomware groups when their existing sponsor is suddenly shut down.
All of the above seems to suggest that the success of any strategy to tackle the ransomware outbreak depends heavily on the ability to disrupt or apprehend a relatively small number of cybercriminals who appear to wear many disguises.
Perhaps this is why the Biden administration said last month it was offering a $ 10 million reward for information leading to the arrest of the gangs behind the extortion schemes, and for new approaches that make it easier to track and block cryptocurrency payments.
[ad_2]
Source link