
[ad_1]
A security researcher has uncovered a new vulnerability that compromises a macOS main security feature designed to prevent applications – or malware – from accessing a user's private data, webcam, or microphone without explicit authorization .
The privacy protections, recently developed in macOS Mojave, were intended to make it more difficult for users to access sensitive user information such as their contacts, calendar, location, and messages. unless the user clicks "allow" in a pop-up dialog box. . The protections also aim to prevent applications from activating the webcam and microphone of a Mac without permission. Apple's Craig Federighi presented security features as "one of the reasons why people chose Apple" at the WWDC developer conference last year.
But the protections were not very good. These "allow" boxes can be reversed with a malicious click.
It was previously possible to create artificial or "synthetic" clicks using AppleScript, the built-in automation feature, or using mouse keys, which allow users – and malware – to control the mouse cursor. using the keypad on the keypad. After fixing these bugs in previous versions of MacOS, Apple's current defense is to block all synthetic clicks, forcing the user to physically click a button.
But Patrick Wardle, a former NSA hacker currently in charge of research at Digita Security, said he found another way to circumvent these protections with relative ease.
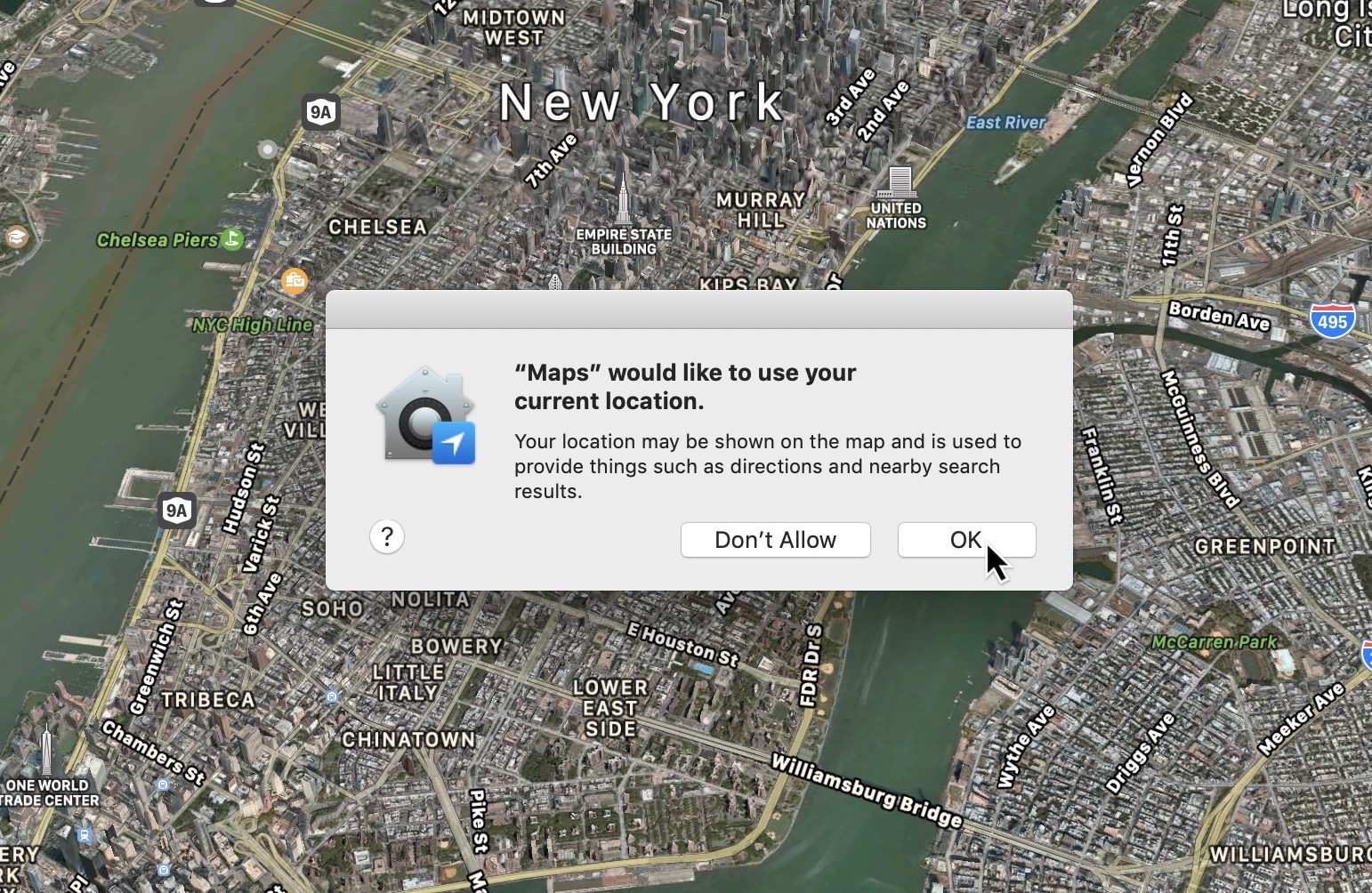
One of the Apple Consent dialog boxes is displayed for a user when an application requests access to a user's personal information, such as its location. (Image: TechCrunch)
Wardle, who revealed the zero-day flaw at his conference Objective By The Sea in Monaco on Sunday, said the bug stems from an undocumented white list of approved macOS applications, allowed to create clicks synthetic to prevent them from breaking.
Generally, applications are signed with a digital certificate to prove that the application is genuine and has not been tampered with. If the application has been modified to include malicious programs, the certificate usually reports an error, and the operating system does not run the application. But a bug in Apple's code meant that macOS was only checking if a certificate existed and did not correctly check the authenticity of the whitelisted application.
"Apple is only validating that the application is signed by those they think they are," he said. Because MacOS did not check if the application had been modified or manipulated, a manipulated version of an application listed in the whitelist could be exploited to trigger a synthetic click.
One of these approved applications is VLC, a popular and highly customizable open source video player that allows plug-ins and other extensions. Wardle said it was possible to use VLC as a delivery vector for a malicious plug-in to create a synthetic click on a consent prompt without the user's permission.
"For VLC, I have just uploaded a new plug-in, VLC is loading it, and as VLC is loading it, my malicious plug-in can generate a synthetic click – which is fully allowed because the system sees its VLC but does not validate that the package make sure that it has not been tampered with, "he explained
"And so, my synthetic events are able to click and access the user's location, webcam, microphone," he said.
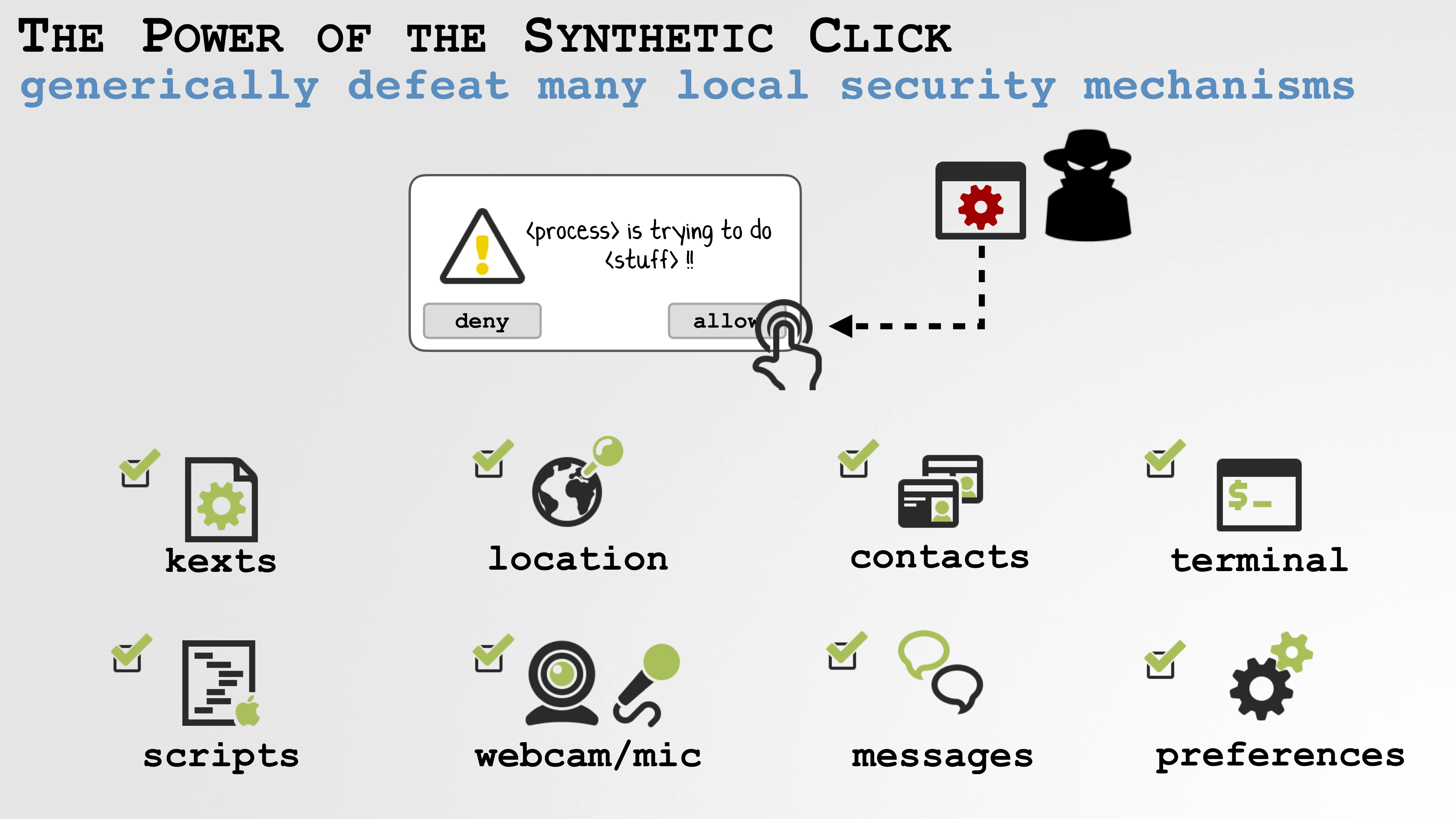
A slide from the Wardle conference in Monaco on June 2, in which he describes a vulnerability that could be exploited to access a user's webcam, microphone, and personal data. (Image: Patrick Wardle / provided)
Wardle describes this vulnerability as a "second step" attack because the bug already requires an attacker – or malware – to have access to the computer. . But that's exactly the kind of situation that malware on a computer is trying to click on a consent box that Apple is trying to prevent, Wardle said.
He said he informed Apple of the problem last week, but that the tech giant has not yet released a fix. "This is not a remote attack, so I do not think it immediately endangers a lot of Mac users," he said.
A spokesman for Apple did not return a request for comment.
This is not the first time Wardle has warned Apple of a bug related to synthetic clicks. He reported related bugs in 2015, 2017 and 2018. He said that it was "clear" that Apple does not take these bugs seriously.
"In this case, nobody has looked at this coat from a security point of view," he said.
"We have this undocumented whitelist feature that is critical for all these new privacy and security features, because if you can generate synthetic events, you can generically prevent them trivially," he said. .
"It's important to do things right," he said.
[ad_2]
Source link