[ad_1]

The REvil ransomware gang has returned and is once again attacking new victims and posting stolen files on a data breach site.
Since 2019, the ransomware operation REvil, aka Sodinokibi, has been carrying out attacks against organizations around the world demanding ransoms of a million dollars to receive a decryption key and prevent the leak of stolen files.
During its operation, the gang has been involved in numerous attacks against well-known companies including JBS, Coop, Travelex, GSMLaw, Kenneth Cole, Grupo Fleury, and others.
REvil’s disappearance certificate
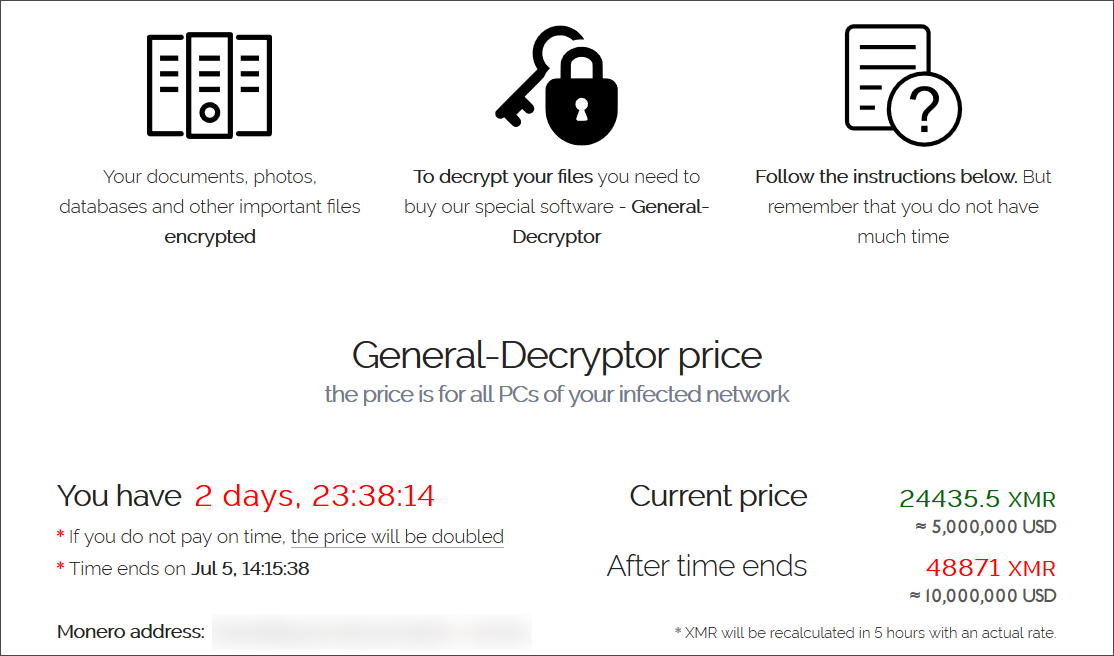
REvil shut down its infrastructure and disappeared completely after its biggest run to date – a massive attack on July 2 that encrypted 60 managed service providers and more than 1,500 businesses using a zero-day vulnerability in the Kaseya VSA remote management platform.
REvil then demanded $ 50 million for a universal decryptor for all Kaseya victims, $ 5 million for decryption of an MSP, and a ransom of $ 44,999 for individual file encryption extensions at the companies involved.
This attack had such sweeping consequences around the world that it drew the full attention of international law enforcement agencies to the group.
Likely feeling pressure and fearing apprehension, the REvil gang suddenly shut down on July 13, 2021, leaving many victims in a lurch with no way to decrypt their files.
The last time we heard about REvil was that Kaseya had received a universal decryptor that victims could use to decrypt files for free. It is not known how Kaseya received the decryptor, but said it was from a “trusted third party”.
REvil returns with new attacks
After their shutdown, researchers and law enforcement believed REvil would be rebranded as a new ransomware operation at some point.
However, to our surprise, the REvil ransomware gang came back to life this week under the same name.
On September 7, nearly two months after they disappeared, the Tor payment / trading and data breach sites suddenly reignited and became accessible. A day later, it was again possible to log into the Tor payment site and negotiate with the ransomware gang.
All of the previous victims had their timers reset, and it turned out that their ransom demands remained as they were when the ransomware gang shut down in July.
However, there was no evidence of any new attacks until September 9, when someone uploaded a new sample of REvil ransomware compiled on September 4 to VirusTotal.
Today we saw further evidence of their renewed attacks as the ransomware gang posted screenshots of stolen data for a new victim on their data breach site.
If you have first-hand information about the return from REvil, you can contact us confidentially on Signal at +16469613731, Wire at @ lawrenceabrams-bc, or Jabber at [email protected].
A new REvil representative appears
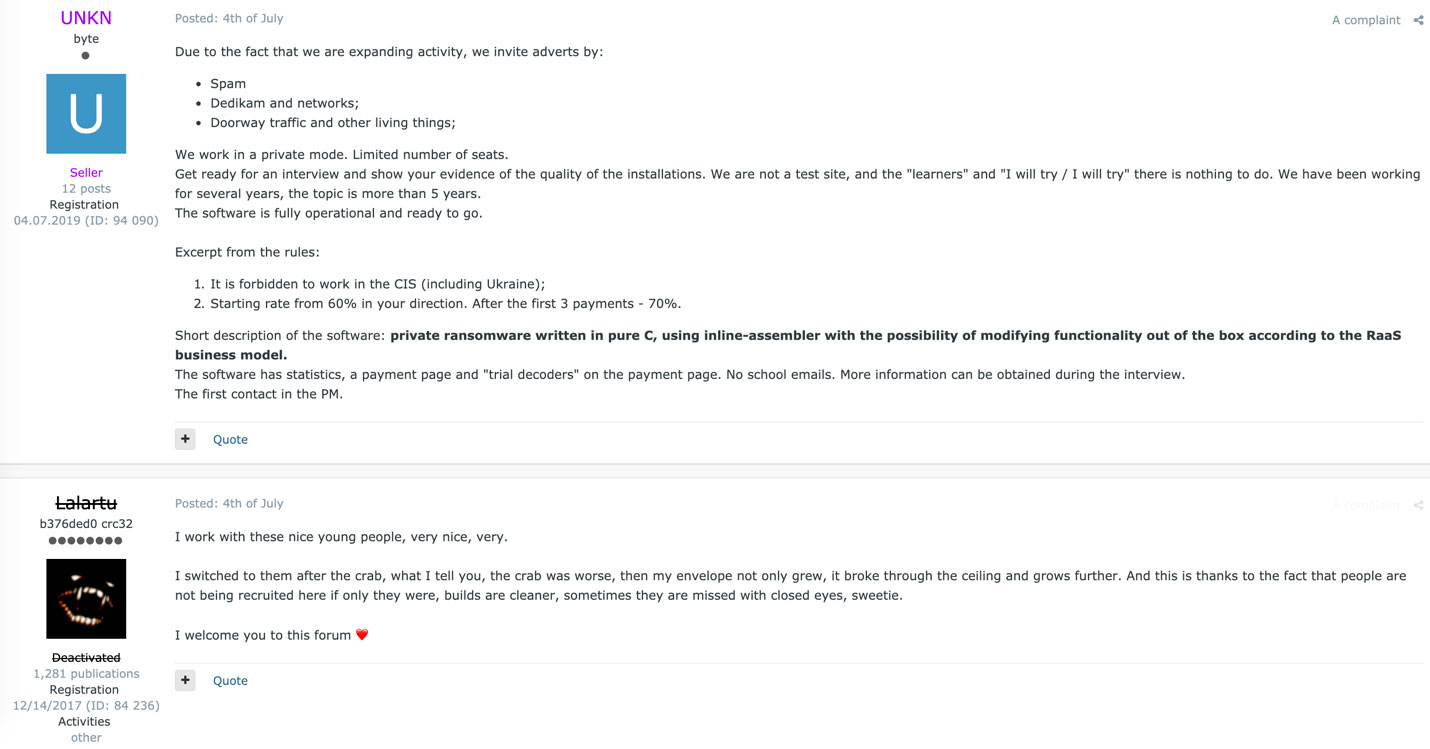
In the past, REvil’s public representative was a threat actor known as “Unknown” or “UNKN”, who frequently posted on hacking forums to recruit new affiliates or post information about the ransomware operation.
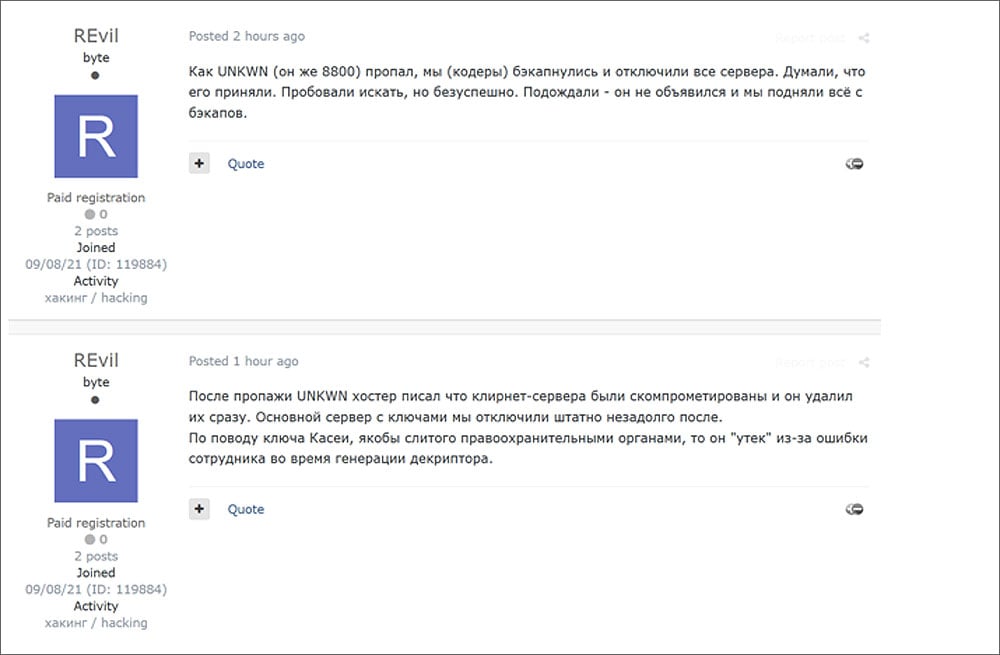
On September 9, after the ransomware operation returned, a new rep simply named “REvil” began posting on hacking forums claiming that the gang briefly shut down after believing that Unknown had been arrested and that the servers had been compromised.
Source: Advanced Intel
This translation of these messages can be read below:
“As Unknown (aka 8800) went missing, we (the encoders) backed up and shut down all the servers. We thought it had been shut down. We tried to search, but to no avail. We waited – it didn’t. did not show up and we restored everything from the backups.
After UNKWN disappeared, the host informed us that the Clearnet servers were compromised and they removed them immediately. We shut down the main server with the keys right after.
The Kaseya decryptor, which was allegedly leaked by law enforcement, was actually leaked by one of our operators during the generation of the decryptor. “- REvil
Based on these claims, Kaseya’s Universal Decryptor was obtained by law enforcement after gaining access to some of REvil’s servers.
However, BleepingComputer has been told by numerous sources that REvil’s disappearance has surprised law enforcement as much as everyone else.
A conversation between what is believed to be a security researcher and REvil, paints a different story, with an operator from REvil claiming that they simply took a break.
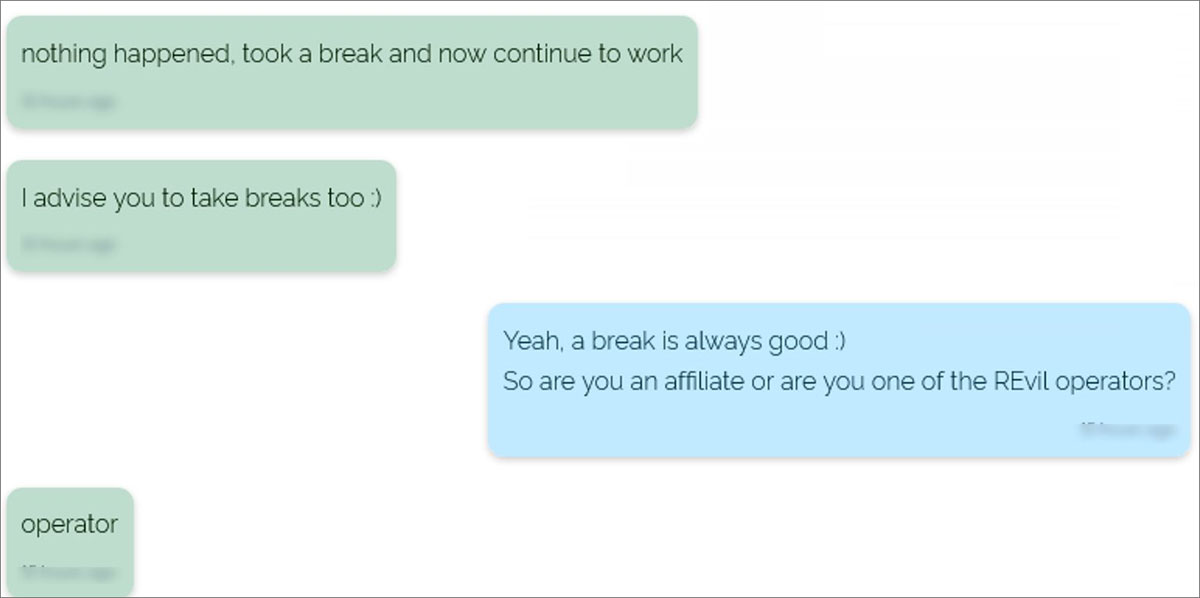
While we may never know the real reason for the disappearance or how Kaseya obtained the decryption key, most importantly, we know that REvil is back to target businesses around the world.
With their skilled affiliates and their ability to perform sophisticated attacks, all network administrators and security professionals should become familiar with their tactics and techniques.
[ad_2]
Source link