[ad_1]
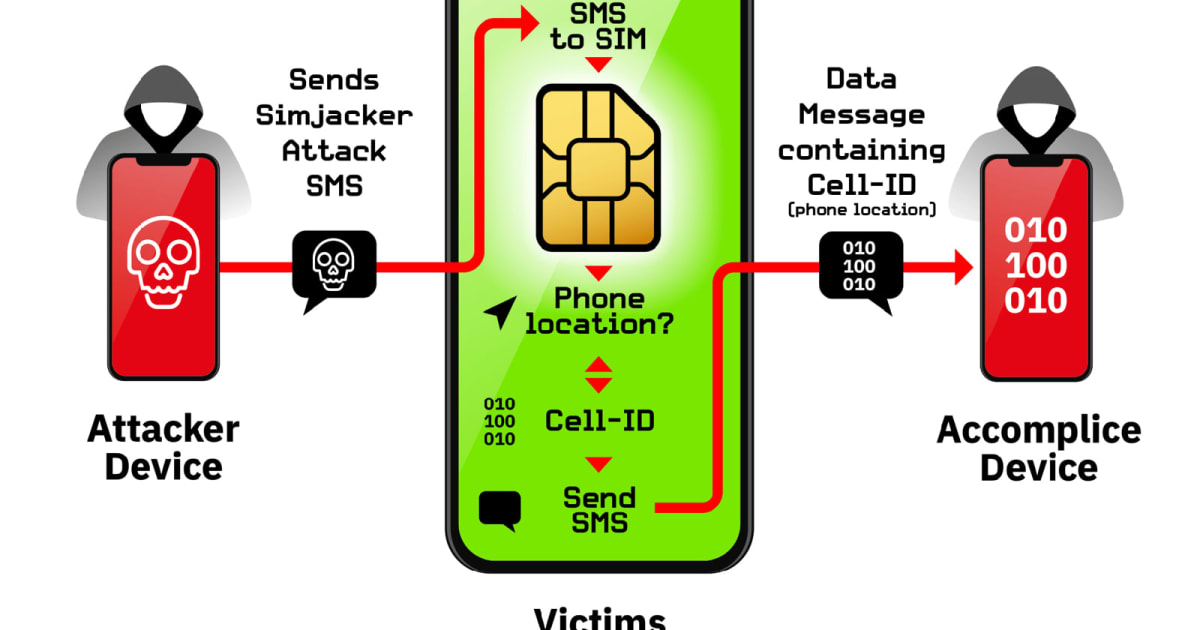
Above all, the approach is silent. Although SMS uses, you will not receive notifications. An intruder can get frequent updates without giving up his activity. The exploit is also device independent and has been used against the iPhone, many brands of Android phones and some Internet-enabled devices equipped with SIM card.
And it's not just a theoretical exercise. The surveillance company reportedly used Simjacker in more than 30 countries (mainly in the Middle East, North Africa, Asia and Eastern Europe) for at least two years. While most targets were only controlled a few times a day for long periods, a handful of people were targeted hundreds of times in a week – 250 in the case of the largest target. It is not thought to be a mass surveillance campaign, but AdaptiveMobile also did not say whether it was used to hunt down criminals or for more harmful purposes, such as espionage of political dissidents. . The company is setting up a "very sophisticated" operation, AdaptiveMobile said.
Networks should be able to thwart these attacks. Simjacker sends code rather than ordinary text, so it should be possible to block the code. However, it may be difficult to coordinate this response when the affected countries have one billion inhabitants. And although you are not likely to be targeted by this particular organization, nothing prevents an attacker also able to launch a wider campaign. It may take a long time before you can assume that your SIM card is not a potential weakness.
[ad_2]
Source link