
[ad_1]

TrickBot, one of the world’s best-known and most adaptable malware botnets, expands its set of tools to investigate firmware vulnerabilities to potentially deploy bootkits and take complete control of an infected system .
The new feature, dubbed ‘TrickBoot’ by Advanced Intelligence (AdvIntel) and Eclypsium, uses readily available tools to scan for well-known vulnerabilities on devices that can allow attackers to inject malicious code into UEFI / BIOS firmware. a device, making attackers an effective mechanism for storing persistent malware.
“This marks a significant step in the evolution of TrickBot as UEFI-level implants are the deepest, most powerful and stealthy form of bootkits,” the researchers said.
By adding the ability to channel victim devices for specific UEFI / BIOS firmware vulnerabilities, TrickBot actors are able to target specific victims with firmware-level persistence that survives reimaging or even the ability to device brick. “
UEFI is a firmware interface and BIOS replacement that improves security, ensuring that no malware has tampered with the boot process. Since UEFI makes it easier to load the operating system itself, these infections are resistant to reinstalling the operating system or replacing the hard drive.
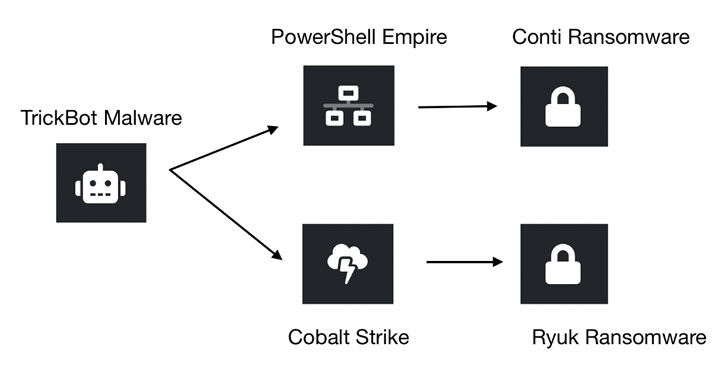
TrickBot emerged in 2016 as a banking Trojan, but has since evolved into a General Purpose Malware As a Service (MaaS) that infects systems with other malicious payloads designed to steal credentials, emails, financial data and spread file encryption ransomware like Conti and Ryuk.
Its modularity and versatility have made it an ideal tool for a diverse set of threat actors despite attempts by cyber vendors to dismantle the infrastructure. It has also been observed in conjunction with Emotet campaigns to deploy Ryuk ransomware.
“Their most common chain of attack begins largely via Emotet’s malspam campaigns, which then charge up TrickBot and / or other loaders, and move to attack tools like PowerShell Empire or Cobalt Strike for achieve goals relating to the victim organization under attack, ”the researchers said. “Often, at the end of the chain of destruction, the Conti or Ryuk ransomware is deployed.”
To date, the botnet has infected more than a million computers, according to Microsoft and its partners at Symantec, ESET, FS-ISAC and Lumen.
From a recognition module to an attack function
The newest addition to their arsenal suggests that TrickBot can not only be used to mass target systems with ransomware and UEFI attacks, but also provide criminal actors with even more leverage when negotiating ransom by leaving a bootkit behind. UEFI secret on the system for later use.
The development is also another sign that adversaries are extending their focus beyond the device’s operating system to lower layers to avoid detection and carry out destructive or espionage-focused campaigns.
TrickBot’s reconnaissance component, first observed in October 2020 just after US Cyber Command and Microsoft-orchestrated takedown attempts, targets Intel systems from Skylake to Comet Lake chipsets to probe for UEFI firmware vulnerabilities of infected people. Machines.
Specifically, the researchers found that TrickBoot targets the SPI flash chip that hosts the UEFI / BIOS firmware, using an obscured copy of the RwDrv.sys driver from the RWEverything tool to check if the BIOS check register is unlocked and that the contents of the BIOS region can be changed.
Although activity so far has been limited to discovery, it would not be difficult to extend this ability to write malicious code to the system firmware, thus ensuring that the attacker’s code executes before the attack. operating system and paving the way for the installation of backdoors or even the destruction of a targeted device.
Also, given the size and scope of the TrickBot, an attack of this type can have serious consequences.
“TrickBoot is just a line of code to be able to brick any device it deems vulnerable,” the researchers noted. “The national security implications resulting from a widespread malware campaign capable of plugging in devices are enormous.”
With UEFI persistence, “TrickBot operators can turn off any OS level security checks they want, which then allows them to resurface to a modified OS with endpoint protections. sterilized and achieve goals with unhurried time on their side.
To mitigate these threats, it is recommended to keep the firmware up to date, enable BIOS write protections, and verify the integrity of the firmware to protect against unauthorized changes.
[ad_2]
Source link