
[ad_1]
Microsoft’s PrintNightmare fiasco brought the vulnerabilities exposed by installing third-party drivers to the attention of the hacker community and today hacker Jonhat has discovered that you can open a wide open door in Windows 10 by simply plugging in a Razer wireless dongle.
Need a local administrator and physical access?
– Connect a Razer mouse (or dongle)
– Windows Update will download and run RazerInstaller as SYSTEM
– Abuse elevated explorer to open Powershell with Shift + right clickI tried to contact @Razer, but no answers. So here is a gift pic.twitter.com/xDkl87RCmz
– jonhat (@ j0nh4t) August 21, 2021
The problem is that Windows Update downloads and runs RazerInstaller as a system, and the installer gives users the option of opening an explorer window to choose where to install the drivers.
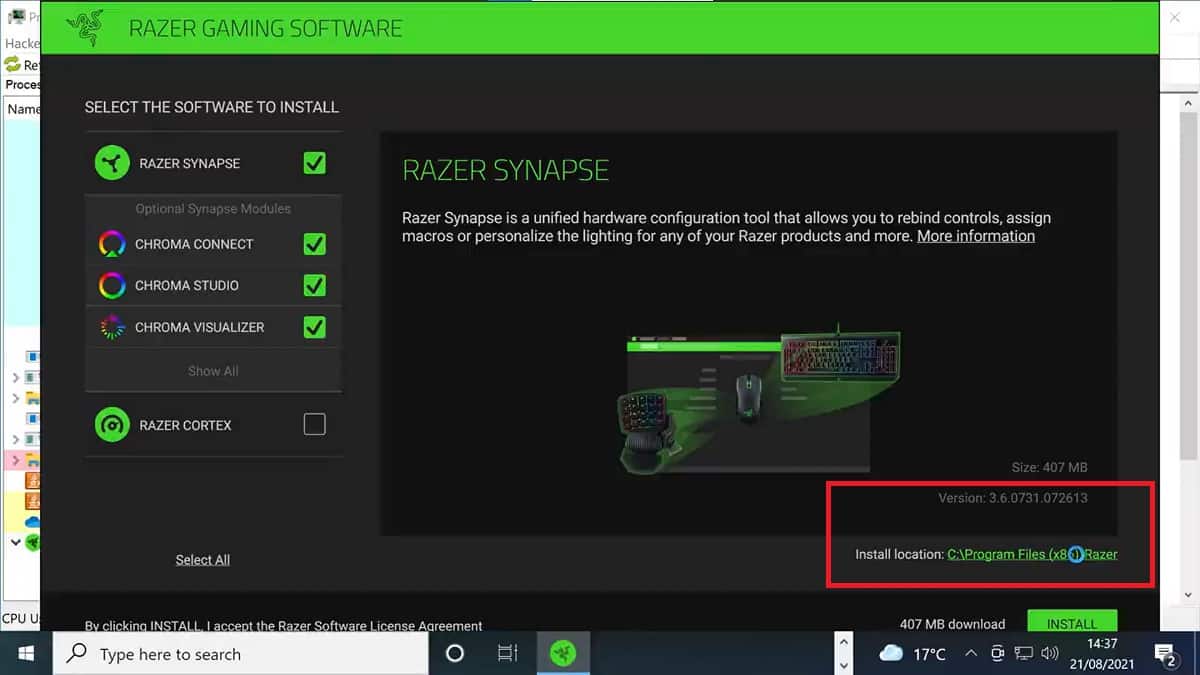
From there, it only takes a right click to open a Powershell terminal with system privileges, and the hacker can basically do whatever he wants.
Additionally, if the user goes through the installation process and sets the backup directory to a user-controllable path like Desktop, the installer saves a service binary there which can be hacked for persistence and which is executed before the user logs in at startup.
Attackers don’t even need a real Razer mouse, as the USB ID can be easily spoofed.
Jonhat says he tried to contact Razer but was unsuccessful, and therefore published the vulnerability. We’re assuming Microsoft will go a bit faster and remove the driver from Windows Update soon, although there is no guarantee as this would leave Razer hardware users without an easy way to access the driver.
See the video in full quality below. The attack is of course simpler than it looks, as much of the video shows observers that the user is indeed a standard user and that Windows is fully patched:
[ad_2]
Source link