[ad_1]
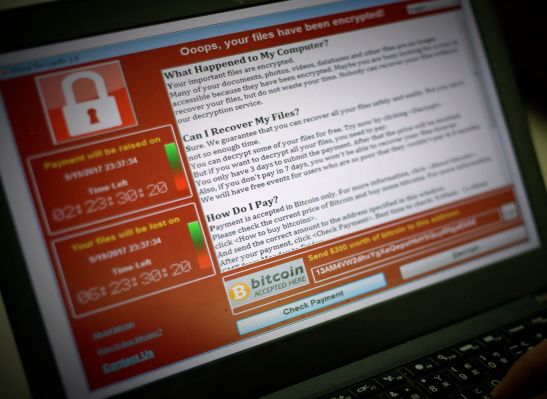
Two years ago today, a powerful ransomware software has begun to spread around the world.
WannaCry has spread like wildfire by encrypting hundreds of thousands of computers in more than 150 countries in a matter of hours. It was the first time that a ransomware, a malware that encrypts a user's files and asks for ransom cryptocurrency to unlock them, had spread around the world from the angle of a coordinated cyber attack.
UK hospitals reported a "major incident" after being decommissioned by malware. Government systems, rail networks and private companies have also been affected.
Security researchers quickly realized that the malware spread like a worm, on computers and over the network, using the Windows SMB protocol. Suspicions were quickly raised on a lot of highly classified hacking tools developed by the National Security Agency, which had been stolen and published online to be accessible to all.
"It's real," said Kevin Beaumont, UK-based security researcher. at the time. "Shit will hit the big fan style."
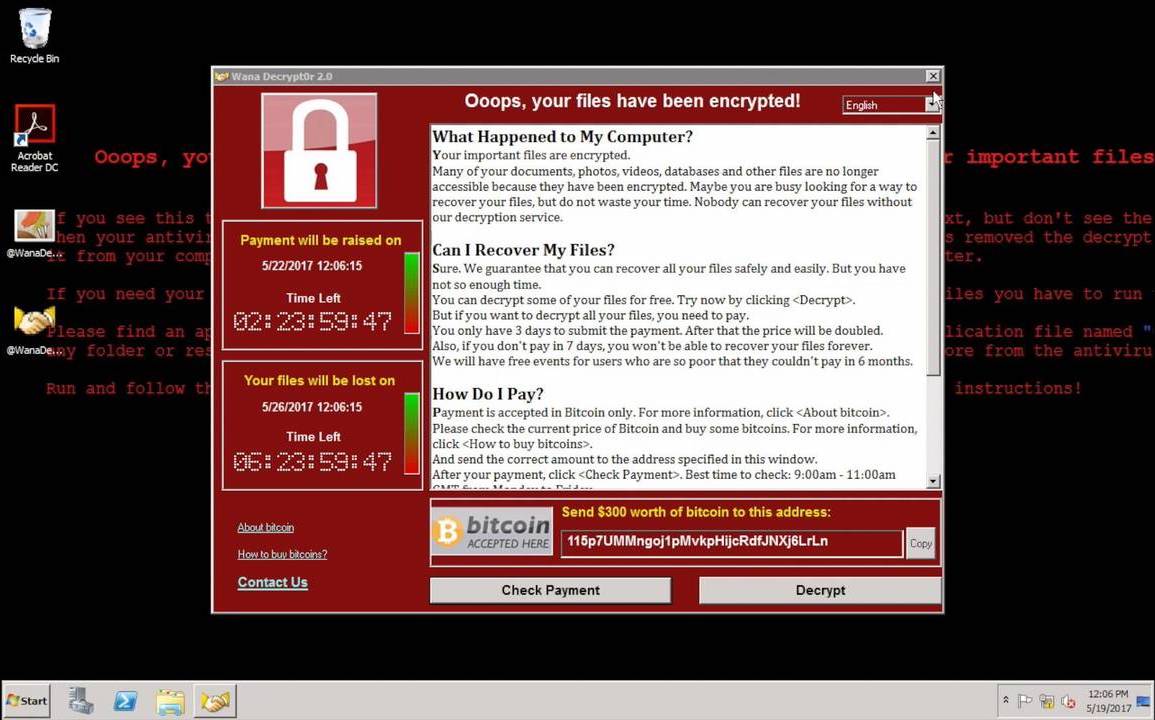
WannaCry relies on the stolen exploits developed by the NSA, DoublePulsar and EternalBlue, to hack Windows PCs and spread over the network. (Image: archive photo)
A group of unknown hackers – who are later thought to be working for North Korea – seized the cyber-weapons issued by the NSA and launched their attack – without probably realizing the magnitude of propagation. Hackers used the NSA's backdoor, DoublePulsar, to create a persistent backdoor used to deliver the WannaCry ransomware. Using the EternalBlue exploit, the ransomware is extended to all other computers not patched on the network.
Only one vulnerable system exposed to the Internet was enough to wreak havoc.
Microsoft, already aware of the theft of hacking tools targeting his operating systems, had released patches. But consumers and businesses have slowly changed their systems.
In just a few hours, the ransomware had caused billions of dollars in damages. Bitcoin portfolios associated with ransomware were fill by victims to recover their records – most often to no avail.
Marcus Hutchins, a counter-intelligence engineer and malware specialist, was on vacation at the time of the attack. "I took a fucking week to take my job," he said. tweeted. Shortening his holidays, he went to his computer. Using data from its malware tracking system, he found what became WannaCry's firewall – a domain name built-in code that, when registered, immediately saw the number of infections stop. Hutchins, who pleaded guilty to unrelated computer crimes last month, has been hailed as a hero for stemming the spread of the attack. Many have called for clemency, if not a complete presidential pardon for his efforts.
Trust in intelligence services has collapsed overnight. Lawmakers demanded to know how the NSA was planning to clean up the hurricane from the damage done. It has also launched a heated debate over how the government accumulates vulnerabilities as offensive weapons for surveillance or spying purposes, or when it should disclose bugs to sellers in order to correct.
A month later, the world was preparing for a second round of cyberattacks in which what looked like it would soon become the norm.
NotPetya, another ransomware for which the researchers also found a switch, used the same exploits DoublePulsar and EternalBlue to delight the transport giants, supermarkets and advertising agencies, left shocked by the attacks.
Two years later, the threat posed by the leak of NSA tools remains a concern.
Nearly 1.7 million Internet-connected terminals are always vulnerable exploits, according to the latest data. The data generated by Shodan, a search engine for exposed databases and devices, puts the figure at one million – with most vulnerable devices in the United States. But this only represents devices directly connected to the Internet and not the millions of devices potentially connected to these infected servers. The number of vulnerable devices is probably much higher.
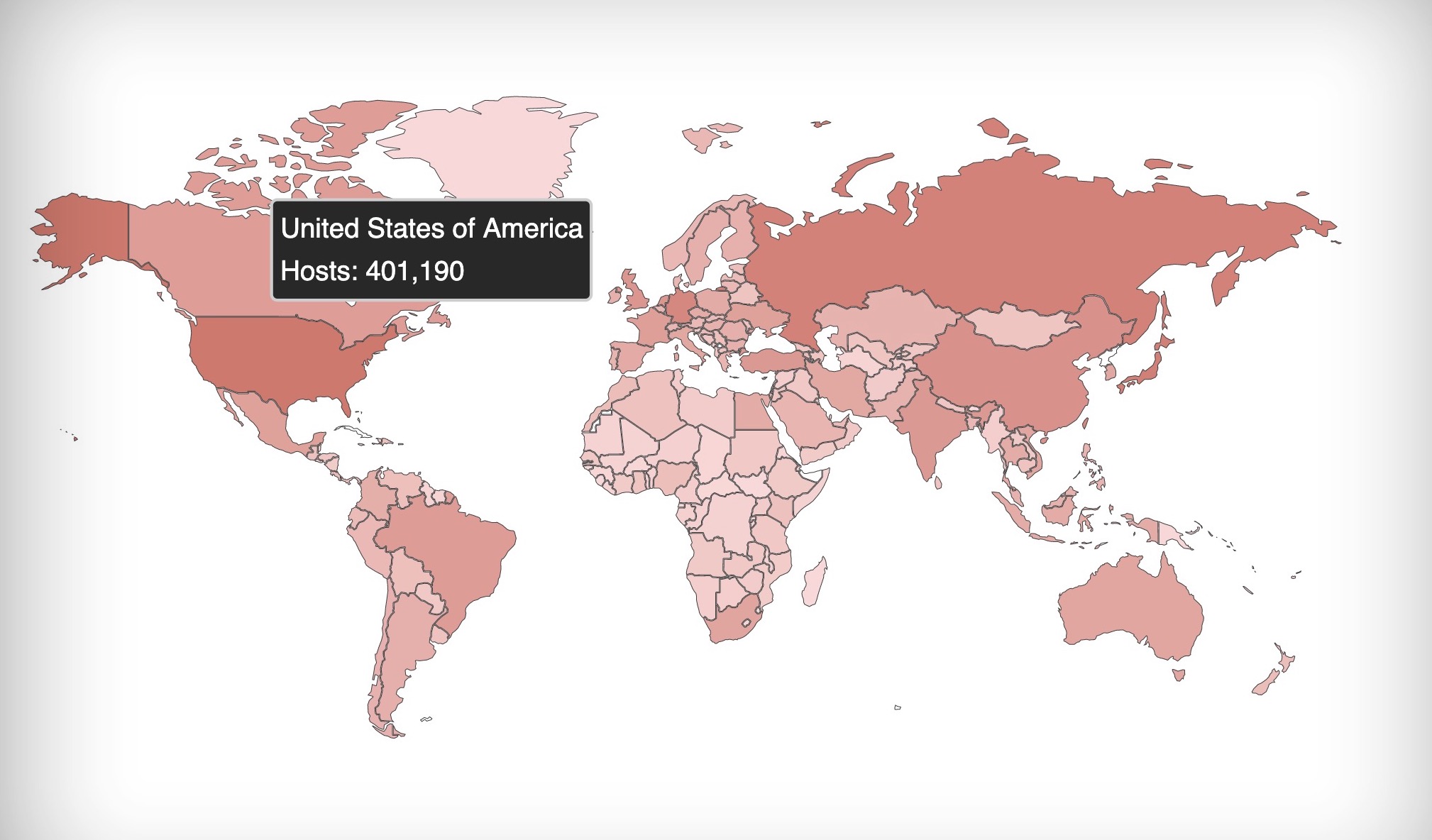
More than 400,000 systems exposed in the United States can be exploited using the NSA's stolen hacking tools. (Image: Shodan)
WannaCry continues to spread and sometimes still infects its targets. Beaumont said in a tweet On Sunday, the ransomware remains largely sterilized, unable to decompress and start encrypting data, for reasons that remain mysterious.
However, the NSA's exposed tools, which remain in place and can infect vulnerable computers, continue to be used to transmit all sorts of malicious programs – and new victims continue to appear.
A few weeks before the city of Atlanta was hit by a ransomware, cybersecurity expert Jake Williams discovered that his networks had been infected with NSA tools. More recently, NSA tools have been reconverted to infect networks with cryptocurrency mining code to generate money from vast reserves of processing power. Others have used these exploits to secretly trap thousands of computers in order to exploit their bandwidth to launch distributed denial of service attacks by hitting other systems with massive volumes of Internet traffic.
WannaCry caused panic. The systems were down, the data was lost and money had to be spent. It was a wake up call that the company needed to do better in basic cybersecurity.
But with more than one million devices not corrected in danger, there are still many risks of abuse. What we may not have forgotten two years later, it is clear that we can do more to learn from the failures of the past.
Read more:

[ad_2]
Source link