[ad_1]
With an iCloud account and an Apple device, two-factor authentication is very different from that used on any other device or account. As is the case at Apple, 2FA on your iPhone or Mac is integrated with the device you own, thus creating a theoretically as secure system as a security key. Except when it is not the case.
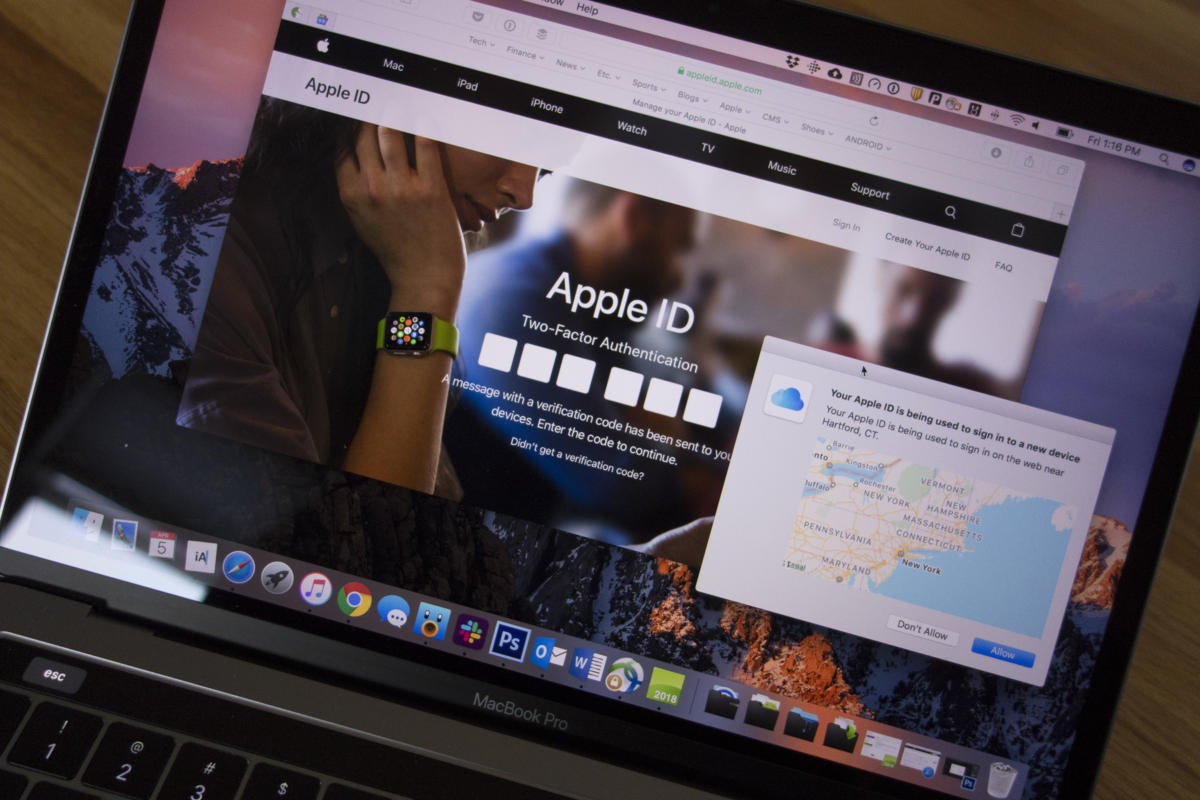
Here is how it works. When you try to sign in to your iCloud or Apple Music account on your iPhone, you will be prompted to enter your password first. Once this is recognized, you will be asked to enter a code that has been sent to one of your trusted devices, for example an iPad. On your iPad, a message will inform you that someone is trying to log into your account and asks you if you want to allow it. Then you will receive a six-digit code that you enter in the boxes of your iPhone.
If you do not receive the code (which happens from time to time), you can request a standard SMS code or use one of the randomly generated codes in your iPhone's Settings application or system preferences. Just tap on your iCloud name on the iPhone or account details on the Mac and then Password and security, and Get a verification code. A six-digit code appears. You can enter them in the appropriate boxes on your other device.
Although it seems that Apple covers all 2FA bases, its proprietary system of trusted devices is not devoid of defects. On the one hand, it works best when you have more than one iOS device. Not only does it add an extra layer of protection by integrating a second device into the mix, it's also 2FA, combining something you know (your password) with something you own (your device ).
Holes in the security system
But if you only have one Apple device, you're not lucky enough and that's where the problem starts. If an iPhone is your only Apple device, for example, you will be essentially blocked by SMS. Obviously, you will not be able to get code on another Apple device, but Apple limits trusted devices to iPhone, iPad, or iPod touch with iOS 9 and later, or to a Mac with OS X El Capitan and later. This means that you can not use a PC, Chromebook or Android phone, which is a major limitation. And since you will be signing into iCloud in the Settings app, you will not be able to get a verification code using the Embedded Authenticator tab.
 IDG
IDGWhen you need to login to your iCloud account with the help of a browser, your 2FA code is transmitted to the same device.
Although you technically protect your account and services through 2FA, it's the least secure way. Problems with the theft of identity and direct theft of text codes upon arrival are well documented. Surely, most Android users also use one of these two options on their phone, but they at least have the option to download an authenticator with biometric authentication. Since Apple does not yet support hardware security keys for iCloud, you really have no choice but to use a second Apple device.
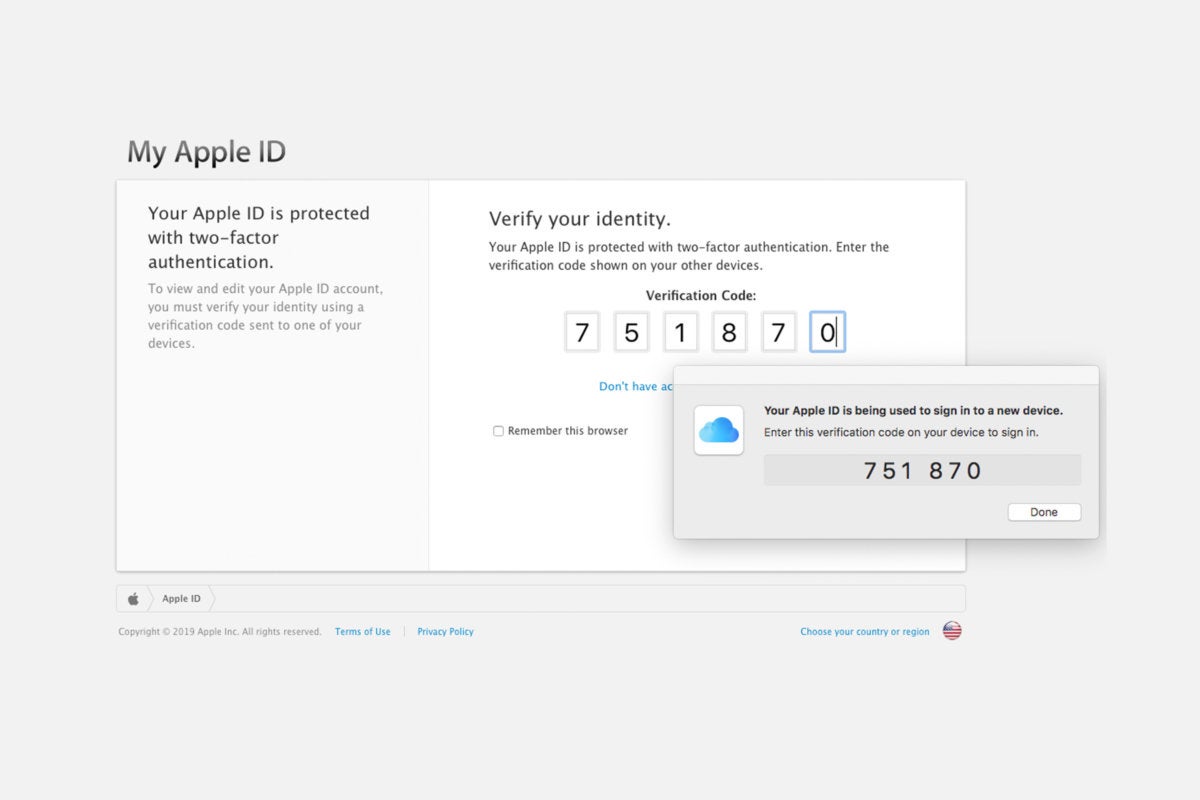
If the implementation of iCloud 2FA with a single Apple device is bad, it is totally flawed when you have to manage your account on the web. When you enter your password to sign in to your Apple ID account page, Apple automatically prompts you to enter the 2FA code, as it should.
However, this code applies to all your secure devices, including the one you use. If you use Safari on your Mac, the 2FA code is displayed on the same screen, which defeats the purpose and makes your most sensitive data vulnerable if your Mac is stolen. This means that all you need is the password of your Mac and that they will have access to your entire account, as long as iCloud Keychain is enabled.
This is the case wherever you connect – iPhone, Mac, PC – Apple will send your 2FA code to anyone trying to sign in to your account from one of your trusted devices. I do not know if it's a bug or some sort of browser-related snafu, but it makes Apple's 2FA system more a 1FA system.
[ad_2]
Source link