[ad_1]
When Windows 11 was introduced in late June 2021, many were excited about its revamped user interface – and countless PC enthusiasts rushed to download Windows Insider Developer Channel versions of the new operating system.
But, as they quickly discovered, the new operating system has several new requirements for PCs to support its new hardware and virtualization-based security features. These features are essential to protect consumer and business workloads from the more sophisticated malware and exploitative threats that currently evolve in nature.
Also: Microsoft just blew up the only reason you can’t use a Linux desktop
It turns out that all of these features are already built into Windows 10 if you are running version 20H2 (Windows 10 October 2020 update). As a consumer, small business, or business, you can take advantage of this if you deploy Group Policy or just click the Windows 10 Device Security menu to enable them. You don’t have to wait for Windows 11 to release or buy a new PC.
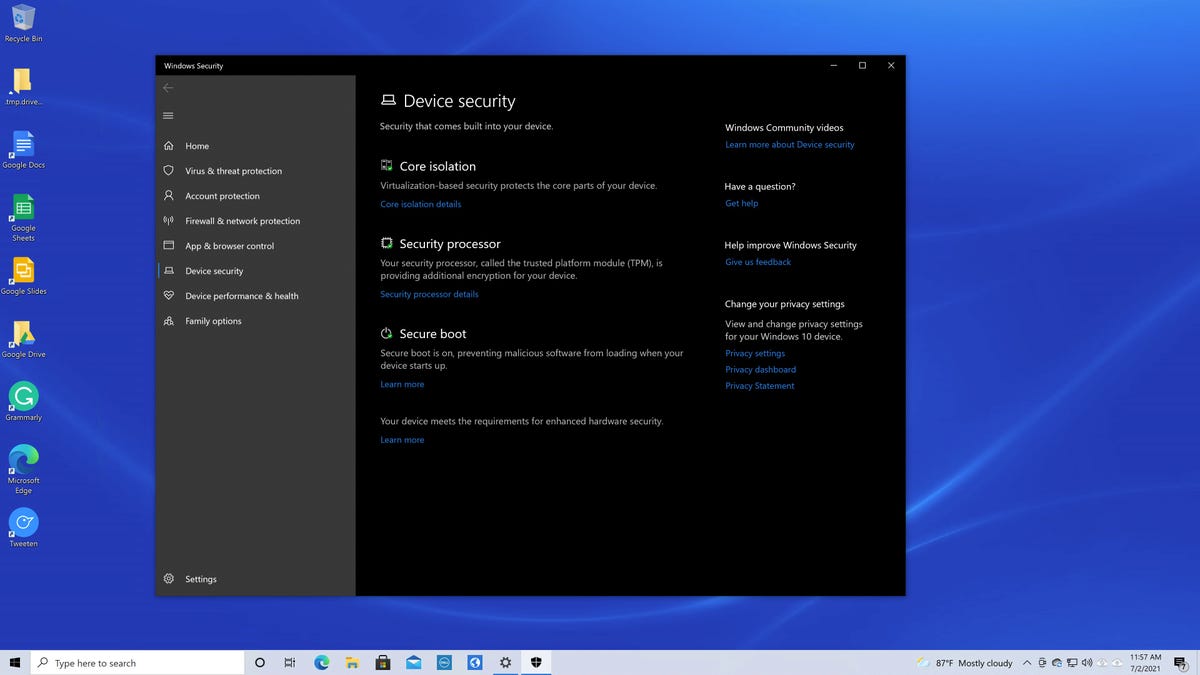
The Device Security menu in Windows 10 20H2
Jason Perlow / ZDNet
Feature 1: TPM 2.0 and Secure Boot
Trusted Platform Module (TPM) is a technology designed to provide security-related hardware cryptographic functions. If you have a PC made in the past five years, chances are you have a TPM chip on your motherboard that supports version 2.0. You can determine this by opening Device Manager and expanding “Security devices”. If it says “Trusted Platform Module 2.0”, you’re good to go.
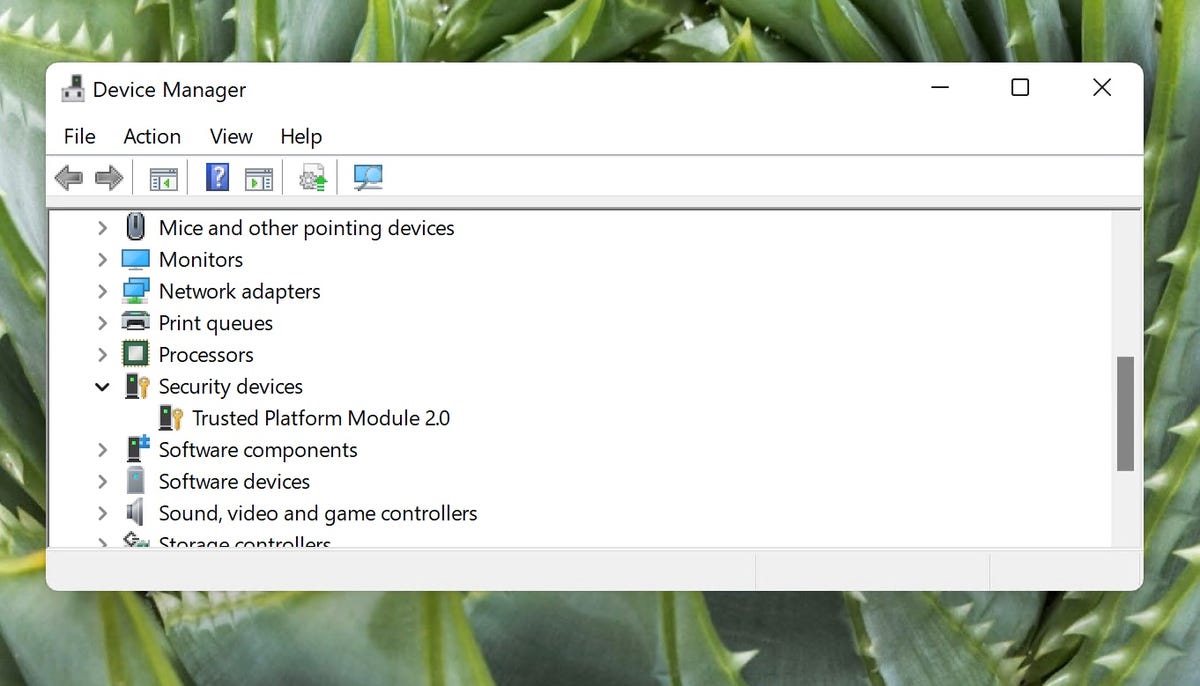
Microsoft Windows Device Manager with TPM 2.0 enumerated
Jason Perlow / ZDNet
This is displayed as “Security Processor” in the Device Security Settings menu in Windows 10 (and Windows 11).
So what does TPM actually do? It is used to generate and store cryptographic keys unique to your system, including an RSA encryption key unique to your system’s TPM itself. In addition to being traditionally used with smart cards and VPNs, TPMs are used to support the secure boot process. It measures the integrity of the operating system’s boot code, including firmware and individual operating system components, to ensure that they have not been compromised.
You don’t have to do anything for it to work; it does, provided it is not disabled in your UEFI. Your organization can choose to deploy Secure Boot on Windows 10 through Group Policy or an MDM-based enterprise solution such as Microsoft Endpoint Manager.
While most manufacturers ship their PCs with TPM enabled, some may turn it off. Therefore, if it doesn’t show up in Device Manager or if it’s disabled, boot into your UEFI firmware settings and watch.
If the TPM was never prepared for use on your system, simply invoke the utility by running tpm.msc from the command line.
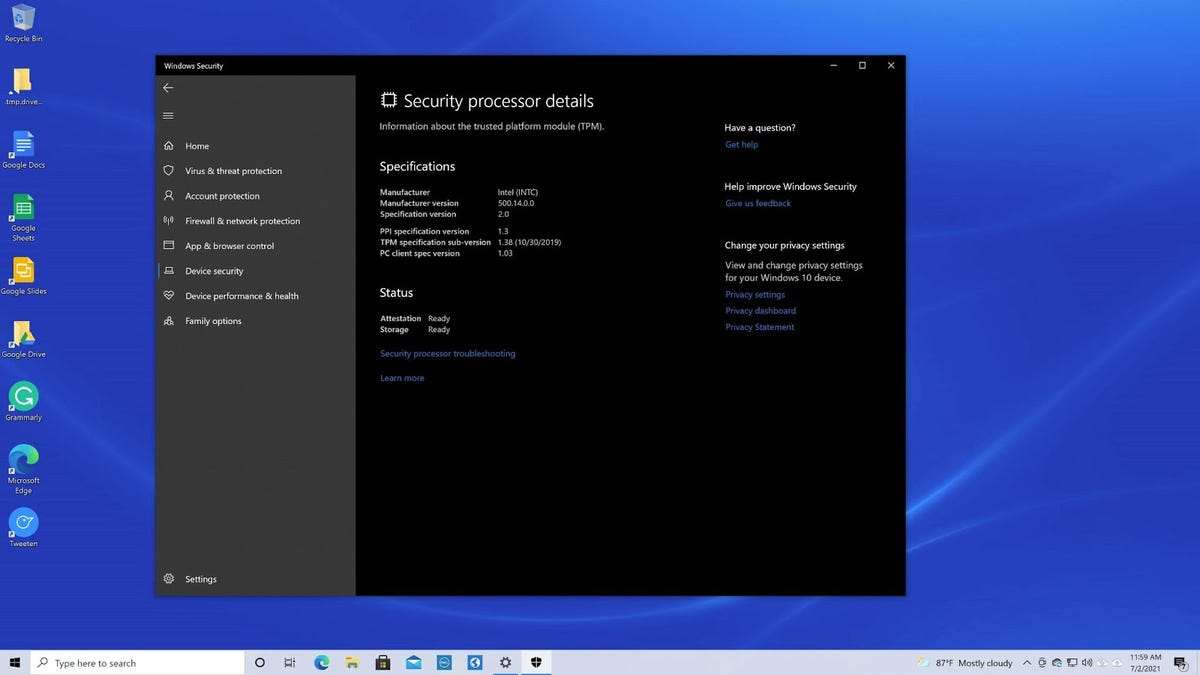
Details of the Security Chip (TPM 2.0) in Windows Device Security.
Feature 2: Virtualization Based Security (VBS) and HVCI
While TPM 2.0 has been common on many PCs for as long as six years, the feature that really allows the security rubber to hit the road in Windows 10 and Windows 11 is HVCI or Hypervisor-Protected Code Integrity, also known as Integrity Integrity. memory or Core. Isolation, as it appears in the Windows Device Security menu.
Although it is required by Windows 11, you have to activate it manually in Windows 10. Just click on “Core Isolation Details” and then turn on Memory Integrity with the toggle switch. It may take about a minute for your system to turn it on, as it needs to check every memory page in Windows before turning it on.
This feature is only usable on 64-bit processors with hardware virtualization extensions, such as Intel’s VT-X and AMD-V. Although initially implemented in server class chips as early as 2005, they have been present in almost every desktop system since at least 2015 or Intel Generation 6 (Skylake). However, it also requires Second Level Address Translation (SLAT), which is present in Intel’s VT-X2 with Extended Page Tables (EPT) and Rapid Virtualization Indexing (RVI) from AMD. .
There is an additional HVCI requirement that any I / O device capable of Direct Memory Access (DMA) is behind an IOMMU (Input / Output Memory Management Unit). These are implemented in processors that support Intel VT-D or AMD-Vi instructions.
It sounds like a long list of requirements, but the bottom line is that you are good to go if Device Security indicates that these features are present in your system.

Windows 10 Device Security Kernel Isolation Feature (Memory Integrity)
Jason Perlow / ZDNet
Isn’t virtualization primarily used to improve workload density in data center servers or by software developers to isolate their test configuration on their desktops or run operating systems? foreigners such as Linux? Yes, but virtualization and containerization / sandboxing are now increasingly used to provide additional layers of security in modern operating systems, including Windows.
In Windows 10 and Windows 11, VBS, or Virtualization-based Security, uses Microsoft’s Hyper-V to create and isolate a secure memory region from the operating system. This protected region is used to run several security solutions that can protect vulnerabilities inherited from the operating system (for example, unexploded application code) and stop exploits that attempt to bypass those protections.
HVCI uses VBS to enforce the code integrity policy by checking all kernel-mode drivers and binaries before booting and preventing unsigned drivers and system files from loading into system memory. These restrictions protect vital operating system resources and security assets such as user credentials. So even if malware gains access to the kernel, the extent of an exploit can be limited and contained, because the hypervisor can prevent the malware from executing code or accessing secrets.
VBS also performs similar functions for application code: it checks applications before they are loaded and only starts them if they are from trusted code signers, assigning permissions on every page in system memory. All of this is done in a secure memory region, which offers more robust protections against kernel viruses and malware.
Think of VBS as the new maintainer of Windows code enforcement, your kernel, and your Robocop application that resides in a protected memory box enabled by your virtualization-enabled processor.
Feature 3: Microsoft Defender Application Guard (MDAG)
One special feature that many Windows users are unaware of is Microsoft Defender Application Guard, or (MDAG).
This is another virtualization-based technology (also known as Hyper-V “Krypton” containers) which when combined with the latest version of Microsoft Edge (and current versions of Chrome and Firefox using an extension), creates an isolated memory instance of your browser, preventing your system and corporate data from being compromised by untrusted websites.

Windows Defender Application Guard used on Microsoft Edge
Jason Perlow / ZDNet
If the browser becomes infected with scripts or malware attacks, the Hyper-V container, which runs separately from the host operating system, is isolated from your critical system processes and corporate data.
MDAG is associated with the network isolation settings configured for your environment to define the limits of your private network as defined by your company’s group policy.
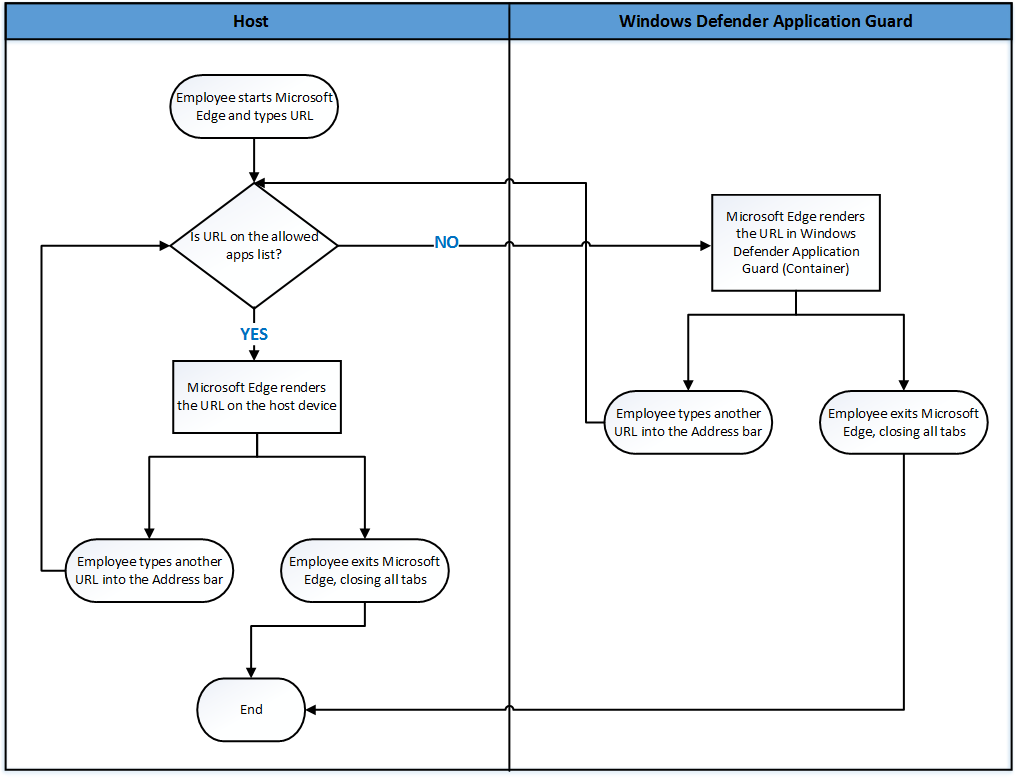
How MDAG works on the host PC and the isolated Hyper-V browser container. (Source: Microsoft)
Microsoft
In addition to protecting your browser sessions, MDAG can also be used with Microsoft 365 and Office to prevent Word, PowerPoint, and Excel files from accessing trusted resources such as credentials and corporate data. This feature was released as a public preview in August 2020 for Microsoft 365 E5 customers.
MDAG, which is part of the Windows 10 Professional, Enterprise, and Education SKUs, is activated with the Windows Features menu or a simple PowerShell command; it does not require the activation of Hyper-V.
Microsoft Defender Access Guard from the Turn Windows Features On or Off menu.
Jason Perlow / ZDNet
While MDAG primarily targets businesses, end users and small businesses can activate it with a simple script that defines GPOs. This excellent video and accompanying article posted at URTech.Ca covers the process in more detail.
[ad_2]
Source link