
[ad_1]

Crooks have been caught using a clever trick to impersonate the website for the Brave browser and use it in Google ads to spread malware that takes over browsers and steals websites. sensitive data.
The attack worked by registering the domain xn – brav-yva[.]com, an encoded string that uses something called punycode to represent bravė[.]com, a name that when displayed in the address bars of browsers confusingly looks like brave.com, where people download the Brave browser. Brave[.]com (note the emphasis on the letter E) was almost a perfect replica of brave.com with one exception: the “Download Brave” button recovered a file that installed malware called ArechClient and SectopRat.
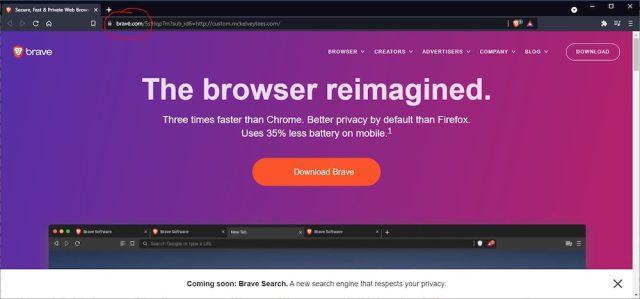
From Google to malware in 10 seconds flat
To drive traffic to the bogus site, the crooks bought ads on Google that were shown when people searched for material involving browsers. The ads looked pretty benign. As the images below show, the domain displayed for an ad was mckelveytees.com, a site that sells clothing for professionals.
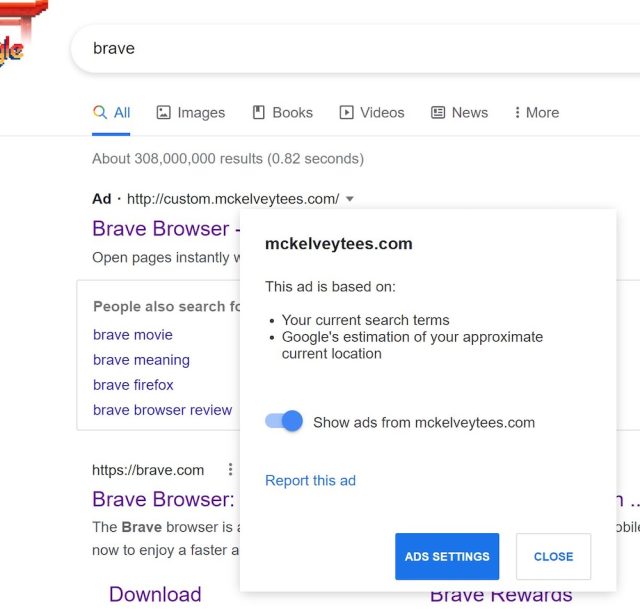
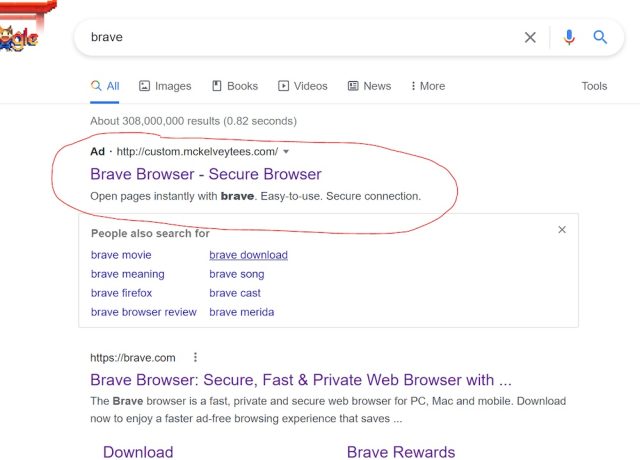
But when people clicked on one of the ads it took them to several areas in between until they ended up landing on bravė[.]com. Jonathan Sampson, a web developer who works at Brave, said the file available for download was an ISO image that was 303MB in size. Inside was a single executable.
VirusTotal immediately showed a handful of antimalware engines detecting ISO and EXE. At the time of this article’s publication, the ISO image has eight detections and the EXE has 16.
The malware detected has several names, including ArechClient and SectopRat. A 2019 analysis by security firm G Data found it to be a remote access Trojan capable of spreading a user’s current desktop or creating an invisible second desktop that attackers could use to browse the internet.
In a follow-up analysis released in February, G Data said the malware has been updated to add new features and capabilities, including encrypted communications with command and control servers controlled by attackers. A separate scan found that it had “capabilities like logging into C2 server, system profiling, stealing browser history from browsers like Chrome and Firefox.”
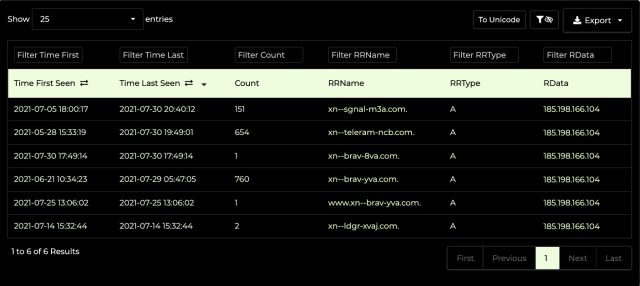
As this passive DNS lookup from DNSDB Scout shows, the IP address that hosted the fake Brave site hosted other suspicious punycode domains, including xn--ldgr-xvaj.com, xn--sgnal-m3a.com, xn- – teleram-ncb.com and xn--brav-8va.com. These translate respectively to lędgėr.com, sīgnal.com teleģram.com and bravę.com. All domains have been registered through NameCheap.
An old attack that’s still at its peak
Martijn Grooten, head of threat intelligence research at security firm Silent Push, wondered if the attacker behind this scam hosted other similar sites on other IP addresses. Using a Silent Push product, he searched for other Punycode domains registered through NameCheap and using the same host. It hit seven other equally suspicious sites.
The results, including the punycode and the translated domain, are:
- xn – screncast-ehb.com — screēncast.com
- xn--flghtsimulator-mdc.com-flghtsimulator.com.
- xn – brav-eva.com — bravē.com
- xn – xodus-hza.com — ēxodus.com
- xn – tradingvew-8sb.com — tradingvīew.com
- xn--torbrwser-zxb.com—torbrwser.com
- xn – tlegram-w7a.com — tēlegram.com
Google removed the malicious ads after Brave brought them to the attention of the company. NameCheap deleted the malicious domains after receiving a notification.
One of the things that is so evil about these attacks is how hard they are to detect. Since the attacker has full control over the punycode domain, the impostor’s site will have a valid TLS certificate. When this domain hosts an exact replica of the spoofed website, even security-conscious people can be fooled.
Unfortunately, there is no clear way to avoid these threats except by taking a few extra seconds to inspect the URL as it appears in the address bar. Attacks using punycode-based domains are not new. Brave.com’s identity theft this week suggests they won’t go out of fashion anytime soon.
[ad_2]
Source link