
[ad_1]

Threat actors share tutorials and zero-day Windows MSHTML exploits (CVE-2021-40444) on hacking forums, allowing other hackers to start exploiting the new vulnerability in their own attacks.
Last Tuesday, Microsoft unveiled a new zero-day vulnerability in Windows MSHTML that allows malicious actors to create malicious documents, including Office and RTF documents, to execute commands remotely on a victim’s computer.
Although no security update is available for the CVE-2021-40444 vulnerability, as it was discovered used in active attacks by EXPMON and Mandiant, Microsoft has decided to disclose the vulnerability and provide action for it. mitigation to prevent its exploitation.
These mitigations work by blocking ActiveX controls and Word / RTF document previews in Windows Explorer.
However, the researchers were able modify the exploit not to use ActiveX, thereby bypassing Microsoft’s mitigation measures.
Guides and PoCs shared on hacking forums
When Microsoft first disclosed the Windows zero-day MSHTML, tracked as CVE-2021-40444, security researchers quickly found the malicious documents used in the attacks.
As they soon reproduced the exploits, modified them for other abilities, and discovered a new document preview vector, the researchers did not disclose details for fear that other threat actors might abuse them.
Unfortunately, the malicious actors were able to reproduce the exploit on their own from malicious information and material samples posted online and began to share detailed guides and information on the hacking forums.
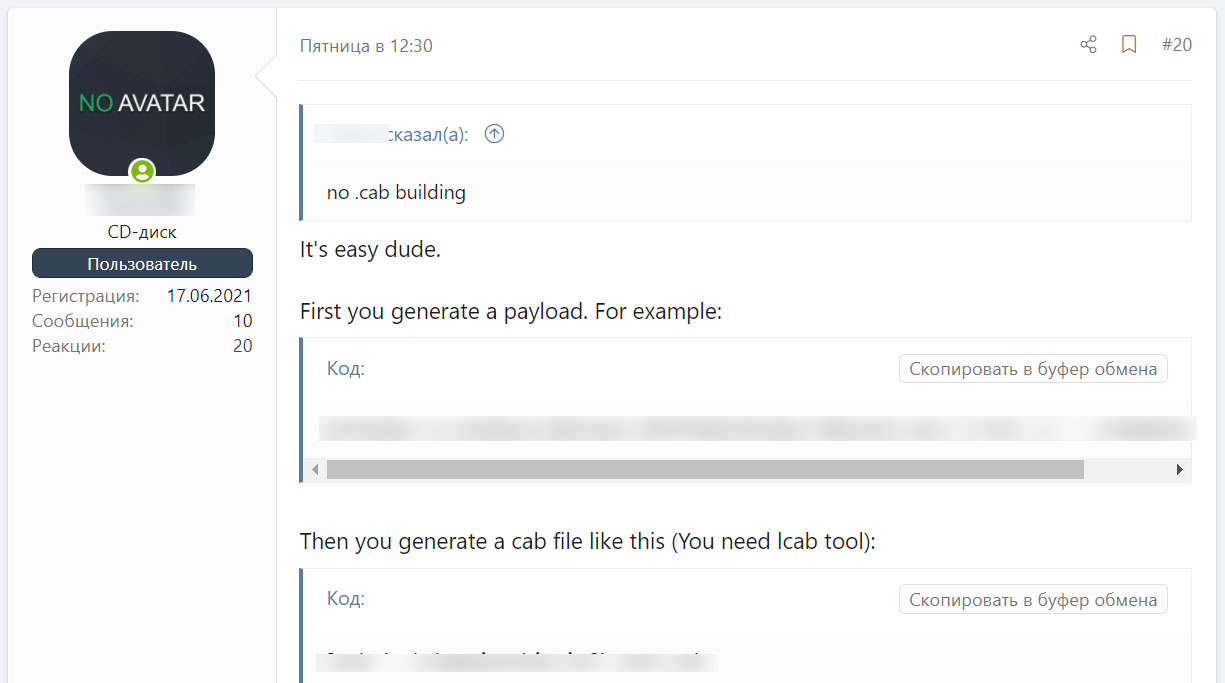
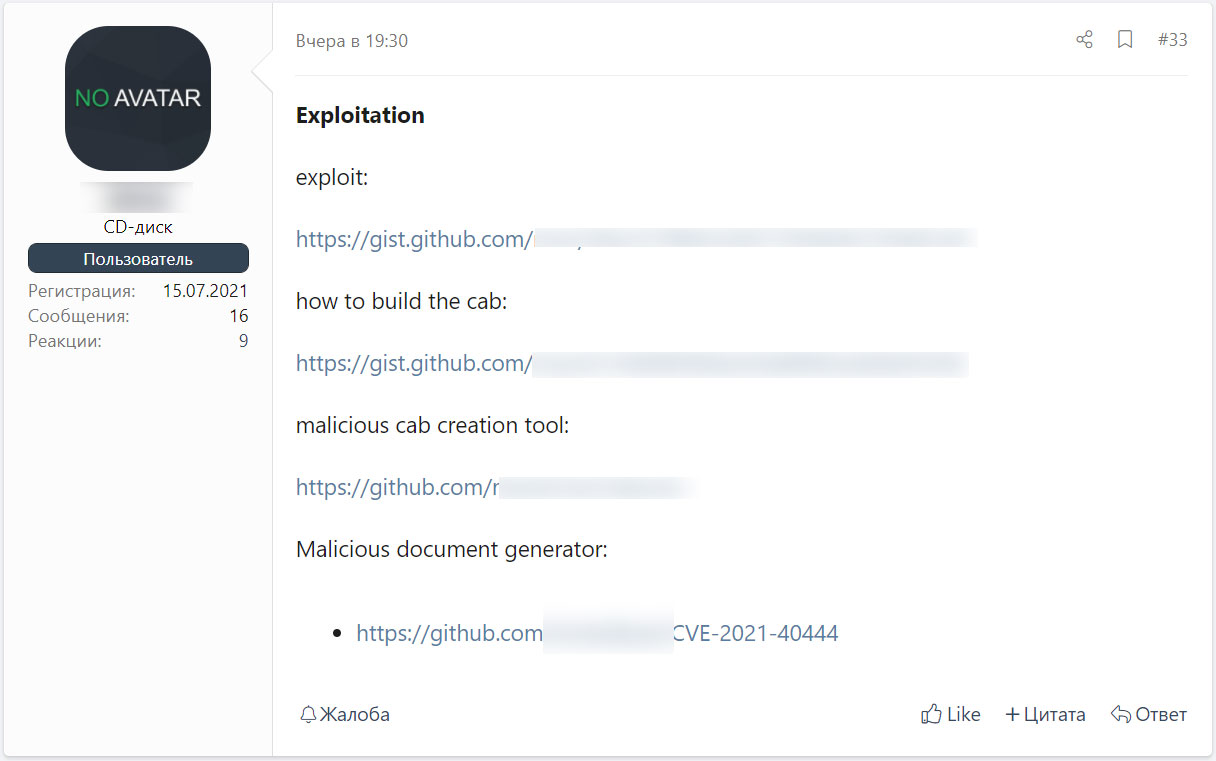
The information is easy to follow and allows anyone to create their own working version of the CVE-2021-40444 exploit, including a python server to distribute malicious documents and CAB files.
Using this information, BleepingComputer could reproduce the exploit in about 15 minutes, as shown in the video below.
Defending against the MSHTML CVE-2021-40444 vulnerability
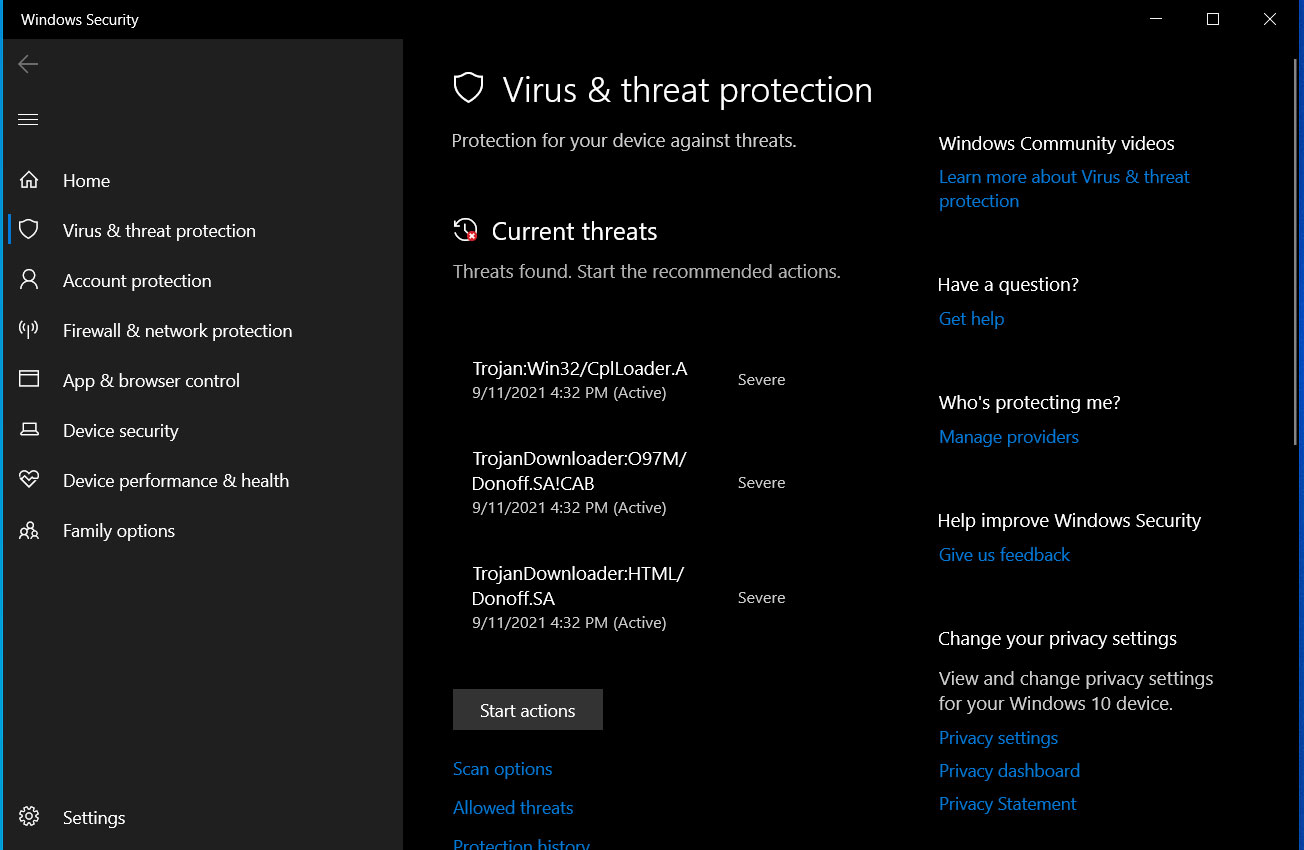
The good news is that since the vulnerability was disclosed, Microsoft Defender and other security programs can detect and block malicious documents and CAB files used in this attack.
For example, below you can see Microsoft Defender blocking the exploit as “Trojan: Win32 / CplLoader.a” and “TrojanDownloader: HTML / Donoff.SA” detections.
Microsoft has also provided the following mitigations to block ActiveX controls in Internet Explorer, the default handler for the MSHTML protocol, and to block document preview in Windows Explorer.
Disable ActiveX Controls in Internet Explorer
To disable ActiveX controls, please follow these steps:
- Open Notepad and paste the following text into a text file. Then save the file as disable-activex.reg. Make sure that the display of file extensions is enabled to correctly create the registry file.
Alternatively, you can download the registry file from here.
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsCurrentVersionInternet SettingsZones�] "1001"=dword:00000003 "1004"=dword:00000003 [HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsCurrentVersionInternet SettingsZones1] "1001"=dword:00000003 "1004"=dword:00000003 [HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsCurrentVersionInternet SettingsZones2] "1001"=dword:00000003 "1004"=dword:00000003 [HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsCurrentVersionInternet SettingsZones3] "1001"=dword:00000003 "1004"=dword:00000003 - Find the newly created disable-activex.reg and double click on it. When a UAC prompt appears, click the Yes button to import registry entries.
- Restart your computer to apply the new configuration.
After your computer restarts, ActiveX controls will be disabled in Internet Explorer.
You can re-enable ActiveX controls by removing the above registry keys or by using this registry file.
Disable document preview in Windows Explorer
Security researchers have also discovered that this vulnerability can be exploited by viewing a malicious document using the Windows Explorer preview function.
CVE-2021-40444 is so bad pic.twitter.com/3Gu9ahwmHd
– jq0904 (@ jq0904) September 10, 2021
Since this was discovered, Microsoft has added the following mitigation to disable previewing of RTF and Word documents:
- In the registry editor (regedit.exe), navigate to the appropriate registry key:
For Word documents, go to these keys:
- HKEY_CLASSES_ROOT.docx ShellEx {8895b1c6-b41f-4c1c-a562-0d564250836f}
- HKEY_CLASSES_ROOT.doc ShellEx {8895b1c6-b41f-4c1c-a562-0d564250836f}
- HKEY_CLASSES_ROOT.docm ShellEx {8895b1c6-b41f-4c1c-a562-0d564250836f}
For rich text (RTF) files, navigate to this key:
- HKEY_CLASSES_ROOT.rtf ShellEx {8895b1c6-b41f-4c1c-a562-0d564250836f}
- Export a copy of the registry key as a backup.
- Now double click name and in the Edit channel dialog box, delete the value data.
- Click on Okay,
Previews for Word documents and RTF files are now disabled in Windows Explorer.
To enable Windows Explorer preview for these documents, double-click the .reg backup file you created in step 2 above.
While these mitigation measures are useful because the exploit has been modified to not use ActiveX controls, users are still at risk until an official security update is released.
Until Microsoft releases a security update, everyone should treat all Word and RTF attachments suspiciously and manually verified their source before opening them.
[ad_2]
Source link