
[ad_1]

Updated 7:23 pm ET: When this message was posted, Zoom's developers reversed their previous position and released an update modifying the disputed behavior.
"At first, we did not consider the web server or video posture a significant risk to our customers, and in fact we felt it was critical to our seamless join process," Jonathan Farley wrote. Zoom. "But hearing the outcry from our users over the past 24 hours, we have decided to update our service."
The update makes the following changes:
- complete removal of the local Web server and
- an add-on to the menu that allows users to delete the app
The Zoom developers have also added new details on a previously mentioned update, which is now scheduled for Friday. It will be
- Automatically save user selection for the first time of the "Always turn off my video" preference and
- allow previously registered users to update their video preferences and disable the default video at any time via the Zoom client settings
The following is the story as it unfolded earlier:
One of the easiest ways to find out if a computer security practitioner is working is to look at his laptop. If the webcam is covered with tape or sticker, this is the case. A recently published report on the Zoom for Mac conferencing application highlights why this practice makes sense.
Researcher Jonathan Leitschuh reported Monday that in some cases, websites can automatically cause visitors to join calls with their cameras on. It's not hard to imagine that this is a problem for people in bathrobe or in the middle of a tricky business conference, since a malicious link will not cancel in advance that it will open Zoom and broadcast everything that happens in front of the camera.
The developers of Zoom almost certainly wanted this behavior to facilitate the use of the web conferencing application. However, unless users have adjusted their settings properly in advance, Lietschuh's results show how villains can turn this ease of use into unintended users. A proof of concept feat is available here, but the reader is warned: Depending on your Zoom settings, your webcam may soon transmit what it sees to complete strangers.
"This vulnerability allows any Web site to forcibly attach a user to a Zoom call, with its video camera enabled, without the permission of the user," wrote Leitschuh.
Leitschuh is mostly correct here. Click the link to automatically open Zoom and join a call. But as mentioned before, video is collected only when Zoom is set to start conferences with a camera turned on. Some media reports and social media commentators have stated that this behavior allows websites to "hijack" a Mac webcam. I would say it's a little exaggerated because (1) it's pretty obvious that Zoom opens and broadcasts what the camera sees and (2) it's easy to immediately leave the conference or just turn off the camera.
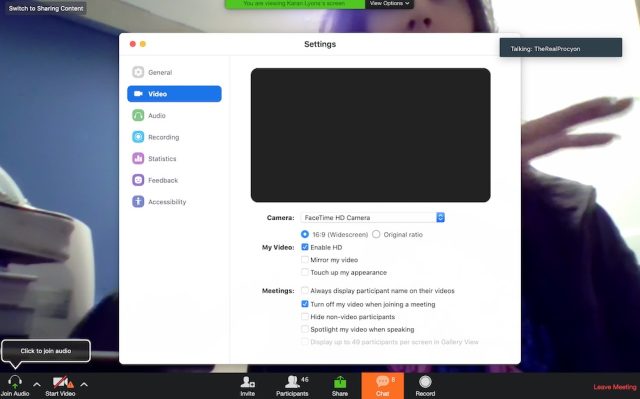
In addition, preventing video capture involves a single click on a box in the Zoom preferences that keeps the video disabled when you attach a video. However, even when this setting is enabled, sites can still force Macs to open Zoom and join a conference.
Dan Goodin
This does not mean that the threat disclosed by Leitschuh is a gesture of the hand. This is not it. But this underscores the almost impossible balance that developers must realize. Make a feature too difficult to use and people will switch to a competing product. Do it too easily and attackers could abuse it to do bad things that the developer never imagined.
In this case, the developers of Zoom should have warned that the ability to automatically join a conference with the video enabled was a powerful feature that could be used to compromise the privacy of users. Instead, developers have left users to decide without any prior advice. (On the other hand, audio is automatically disabled when participating in a Zoom conference.) In other words, Zoom developers have made automatic access to this automatic webcam too easy. In retrospect, thanks to Leitschuh's message, it's easy to see.
In response to Leitschuh's disclosure, Richard Farley of Zoom said the company will publish an update this month that "will apply and record the video preferences of the user from their first Zoom meeting to all future Zoom meetings ". Farley has not specified if Zoom would provide the information that many users will need to make an informed choice.
A permanent web server
Leitschuh's research has revealed another behavior of Zoom for Mac that is also disturbing for security-conscious people. The application installs a web server that accepts requests from other devices connected to the same local network. This server continues to work even when a Mac user uninstalls Zoom. Leitschuh showed how this web server can be misused by people on the same network to force Macs to reinstall the application.
This is clearly not good. Although the Web server is only accessible to devices on the same network, it still exposes people using unreliable networks. And if hackers ever encountered a code execution vulnerability on the Web server, the chances of abuse would be even greater. Farley explained that Zoom introduced the Web server as a way to bypass a change introduced in Safari 12 that requires users to confirm by clicking each time they want to start the Zoom application before joining a meeting.
"We believe it's a legitimate solution to a bad user experience problem, allowing our users to participate in faster meetings with one click," Farley said. "We are not alone among video conferencing providers to implement this solution."
Kevin Beaumont, independent safety researcher says on Twitter the BlueJeans video conferencing application for Mac also opens a web server. Nothing indicates that the behavior reported by Leitschuh is reflected in Zoom for Windows.
Convenience is the enemy of security
As in the case of the self-activated webcam when attending meetings, setting up a Web server by Zoom is a benefit that entails security costs. None of these behaviors represent a critical vulnerability, but they suggest that Zoom developers could do more to lock the Mac version of their application, especially for users who are less aware of security issues.
And it is there that intervene precautions such as recording on a webcam. Users can never be sure that developers have properly protected their apps from hacking or abuse, so the responsibility lies with the end users. Another way to protect yourself against the abuse of Zoom or any other web conferencing software is to use an application such as Little Snitch and configure it to give the conferencing software access to the Internet for a limited time. Another stand-alone protection is to configure macOS so that Zoom only has access to the webcam at specific times, if necessary.
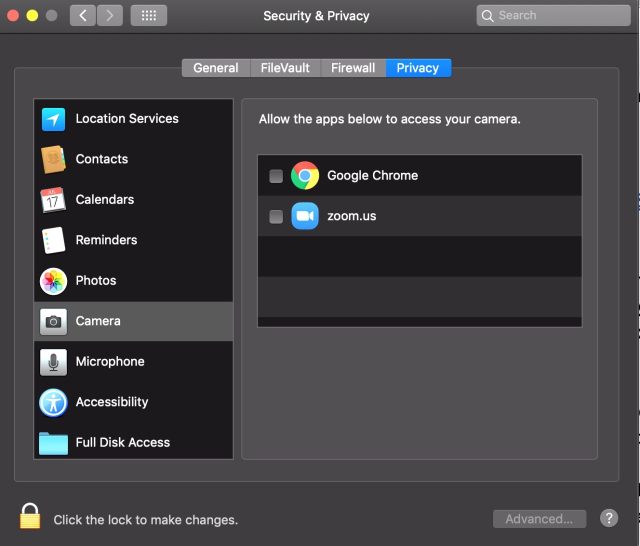
Yes, these extra protections can be a problem. But they also emphasize the fundamental tension between convenience and security.
[ad_2]
Source link