
[ad_1]
Any Mac with the Zoom teleconference app can be spied on right now. Yes, it's a bad day for Apple security because malicious websites can be coded to remotely start a video conference call on your Mac – and the attack can even be emailed.
The good news? Zoom promises that a fix is on the way.
This news, revealed by security researcher Jonathan Leitschuh, shows that even Macs on which Zoom is no longer installed – but which has already been – are vulnerable. The good news, though, is that there are solutions (one is seriously difficult) and that Zoom seems to be fixing the problem quickly.
What to do now:
The solution, thanks to Zoom's position change, seems to be as simple as accepting Zoom updates as they arrive. In an update to Zoom's big blog post on the flaw, the company said that a patch that will arrive tonight (July 9) at or before 3 pm EST / midnight (Pacific Daylight Time) will resolve the problem. Users will be prompted to update the application and after the update, "the local web server will be completely removed from this device".
The update will also improve the uninstall procedure. Zoom Publishing Reports "We are adding a new option to the Zoom menu bar that will allow users to manually and completely uninstall the Zoom client, including the local web server."
We are eager to see if Jonathan Leitschuh and other security researchers think that Zoom is doing a thorough and appropriate job.
Leitschuh shared this tip in his post revealing the flaw.
(Image credit: Jonathan Leitschuh)
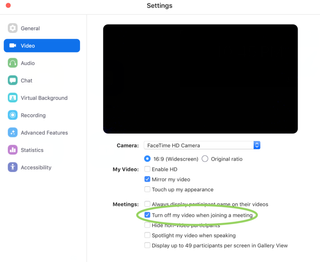
To protect your Mac until this update, open Settings for Zoom – click Zoom in the menu bar, then click Settings – and open the Video section. Then check the box "Disable my video when I attend a meeting".
In his message, Leitschuh also shared code to use in the terminal. These instructions become a little complicated and are better suited to technology-savvy users who would prefer it. These tips are intended to eradicate the web server created by Zoom on the Mac.
How it works
Yes, all this is possible because Zoom secretly installs a web server on Macs, a server that receives – and accepts – requests that your web browsers would not do. Leitschuh explained that he had tried working with Zoom, addressing the company last March, but that his "solutions were not enough to fully protect their users".
In addition, as I mentioned earlier, even users who have uninstalled Zoom from their Mac are vulnerable. Leitschuh explains that the Web server installed by Zoom remains in place even after the removal of the program. and that the server can be triggered remotely to automatically update and install the latest version of Zoom.
Oh, and a victim does not even need to be cheated to open a web page. First, "fun jon", a Vimeo user, posted a video proof that you can attack this flaw by email and that the target does not even need to open the message . They simply need to use an email client application that downloads the encoded message in a malicious way.
After Leitschuh quarreled with Zoom, claiming to have told the company that "allowing a host to choose whether a participant would automatically join the video" was a "stand-alone security breach", the company was not This opinion, placing its decision as a pro user: believes that it is important to give our customers the power to choose how they want to zoom. "
Zoom has also published a blog article arguing its side of the story. He admits no fault or fault.
Do you want to see it for yourself?
If you've ever had Zoom on your machine, you can see it for yourself. Look in Leitschuh's blog for the phrase "zoom_vulnerability_poc /" – because that's the link to his proof of concept, which launches a Zoom call. The first is an audio only version; the second link, which includes "iframe" in the URL, makes a call with the active video.
This vulnerability of Zoom concerns bananas. I've tried one of the technical validation links and I logged in to three other hikes who are also scared in real time. https://t.co/w7JKHk8nZy pic.twitter.com/arOE6DbQafJuly 9, 2019
[ad_2]
Source link