
[ad_1]
What is touted as the "first large-scale empirical study of media permissions and leaks from Android apps" revealed that an alarming number can make use of your screen.
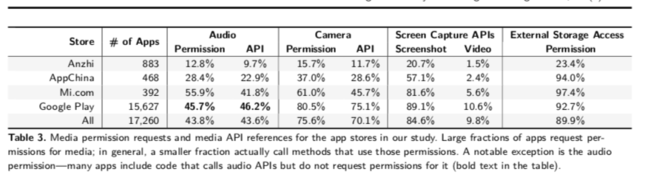
More than 89% of apps in Google Play Store use an API that requires screen capture or recording – and the user is oblivious as it escapes the permission frame Android.
"Our study reveals several alarming privacy risks in the ecosystem of Android applications: media permissions and applications that share images and video data with other parties unexpectedly, without knowledge or consent of the user, "note the authors.
" We also identify a previously undeclared privacy risk download screenshots and videos from the screen without informing the user and without requiring any authorization. "
Authors Elleen Pan (Northeastern University), Jingjing Ren (Northeastern University), Martina L Indorfer (UC Santa Barbara), Christo Wilson (University of Northeast) and David Choffnes (Northeastern University) studied 17,260 apps on Google Play Store and other download sites and used dynamic badysis on a subset of about 9,000 applicati ons. Their article entitled Panoptispy: Characterization of Audio and Video Exfiltration of Android Applications (Abstract and PDF).
They discovered that users and application developers, who claimed to set and control permissions, were ignoring slurping. Or, in their own words, the model of authorization is defective because it is a) "coarse grain" and b) "incomplete".
There is a gaping gap in the security of Android. "There is no authorization required for the third-party code in an application to continuously record the screen displayed to the user," they note.
Google captured more than 80% of the market by offering Android for free, allowing it to dominate search, maps, video and more. But the main business of Google is the mainstream data processing, selling the legal targeting of users to advertisers. The more a phone knows, the more its ads can be targeted and effective.
 Source: Panoptispy: Characterization of audio and video exfiltration from Android applications ; Pan et al (click to enlarge)
Source: Panoptispy: Characterization of audio and video exfiltration from Android applications ; Pan et al (click to enlarge)
On the rise, the authors "have discovered some cases of secret recordings (ie applications that take pictures or videos without the users do so intentionally).
some as the native code is not badyzed. "Our approach to static badysis focuses on the methods of the Android SDK and not the native code, so we can miss cases of media leaks, as well as dynamically loaded code leaks."
The researchers plan to study third-party libraries on iOS next to see what slurping can take place there. ®
Sponsored:
Minds Mastering Machines – Call for Papers Now Open
Source link