[ad_1]
T The Long Term Evolution (LTE) standard for mobile communication, also known as 4G, was designed to overcome the security vulnerabilities of its predecessors and is used by millions of people in whole world.
discovered weaknesses in LTE that allow attackers to hijack the browser session that redirects users to malicious sites and spy on their online activity to find out which sites they visit via their LTE device.
They described three methods of attacking the data link layer of the LTE network on their website. The first two are pbadive attacks that map the identity and fingerprint of the website. However, the most intrusive is the third attack called & # 39; aLTEr & # 39; by the team
What is aLTEr?
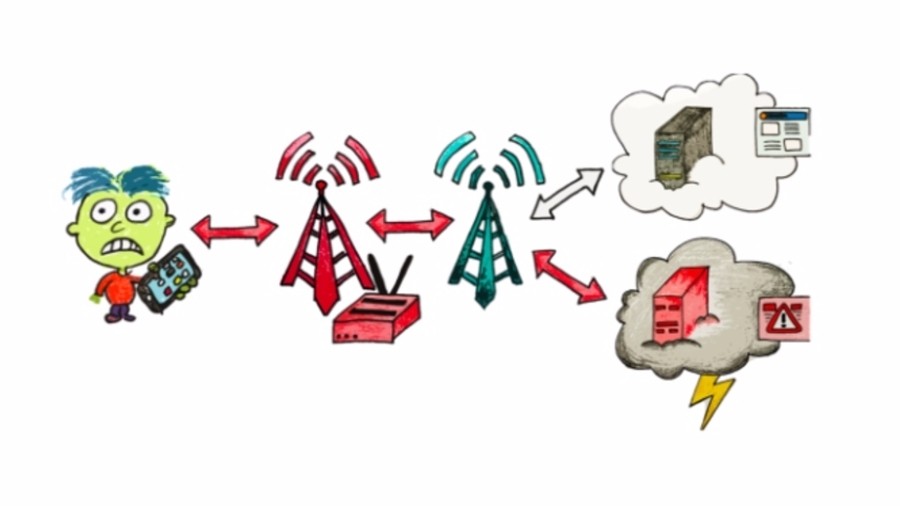
& # 39; Alter & # 39; is an active attack that abuses the data link layer of LTE. It allows attackers to intercept users browsing session and also redirect network queries via DNS spoofing
How does aLTEr work?
According to the researchers, this attack of the data layer of the LTE network is not protected. So & # 39; aLTEr & # 39; claims to be the real user that he wants to attack by creating a cell tower.
This fake cell tower can receive requests from the user and switch to a real cell tower, but before transmitting them, it modifies the bits of the encrypted packet. Later, the attacker can decrypt this package and re-encrypt it with a new DNS server to redirect it to malicious websites.
To what extent did aLTEr?
This method has limitations such as the configuration of an equipment worth $ 4000 and the LTE device must be within a 1-mile radius of the attacker to operate .
So the good news is that leading an aLTEr attack in real world scenarios is quite difficult. However, this does not eliminate the fact that aLter is very real and feasible for someone with the right resources.
What makes it worse is the fact that this security hole can not be corrected like this
How to avoid aLTEr?
The easiest way to avoid being a victim of error is to use HTTPS. Do not forget to check the "secure" text mentioned next to the address bar and avoid trusting an "unsecured" website by your browser.
Read also: Gentoo Linux Distro Hacked: All code on GitHub is compromised
[ad_2]
Source link