
[ad_1]
Google has enabled a defensive technology in Chrome that will make it much more difficult for Spectra attacks to steal information such as login credentials.
Called "Site Isolation", the new security technology has a decade-long history. But more recently, it has been cited as a shield to guard against the threats posed by Specter, the vulnerability of the processor sniffed by Google 's own engineers more than a year ago. Google unveiled Insulation Site at the end of 2017 in Chrome 63, making it an option for IT staff members, who can customize the defense to protect employees from threats hosted on external sites. Enterprise administrators could use Windows GPOs – GPOs – as well as command-line tags before a broader deployment through Group Policies.
Later, in Google Chrome 66, launched in April. could activate the site isolation via the option chrome: // flags . Google said that Site Isolation would become the browser by default, but the company wanted to first validate the fixes to solve the problems encountered during the first tests. Users may have declined to participate in the test by changing any of the settings on the options page.
Google has enabled site isolation for the vast majority of Chrome users, 99% of which by the search giant's account. "Many known issues have been solved since (Chrome 63), making it convenient by default for all desktop Chrome users," Charlie Reis, a Google software engineer, wrote in an article on a company blog .
Reis explained: "A big change in the architecture of Chrome limits each rendering process to documents from a single site." With site isolation enabled, attackers will not be able to share their content in a Chrome process badigned to the content of a Web site.
"When site isolation is enabled, each rendering process contains documents from a maximum of one site, which means that all cross-site document navigation causes a process change in the tabs, which means that all inter-site iframes are placed in a different process from their parent frame, using out-of-process iframes added, was a major change in Chrome's operation, and one that engineers had been pursuing since several years long before Spectrum was discovered.
Reis's doctoral thesis almost ten years ago was on the subject, and the Chrome team was
 Google
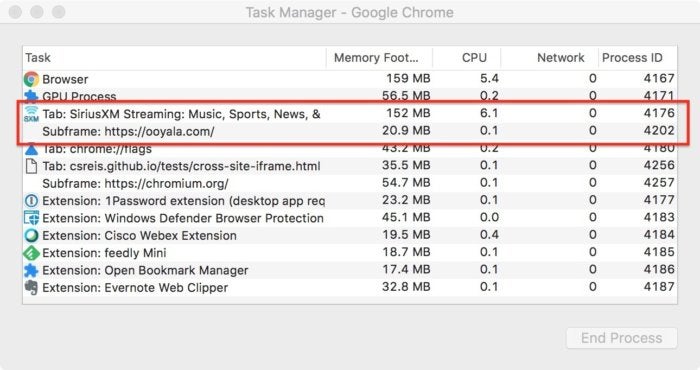
Google With site isolation enabled by default in 99% of Chrome instances, the browser task manager checks that the defense is operational. s for the tab dedicated to streaming music SiriusXM and the sub-picture below.
"This is an extremely impressive achievement" tweeted Eric Lawrence a former software engineer at Google but now a senior program director at rival Microsoft. "Google has invested many years of engineering in a feature that at first seemed hopeless compared to the cost / profit POV [point-of-view] .And then, suddenly, it wasn? T just a DiD nice-to-have [defense-in-depth] but instead essential defense against a clbad of attack. "
others have dropped as well. "The current version only defends against data-leakage attacks (eg Spectrum), but work is underway to protect against compromised engine attacks." tweeted Justin Schuh Senior Engineer and Director on Chrome Security. "We have not yet delivered to Android because we are still working on resource consumption issues."
Resource consumption can not be a "problem" imposed by Google with site isolation, but there are compromises technology, the company acknowledged. "There is about 10-13% overhead in real workloads because of the larger number of processes," said Reis, adding that engineers were still working on reducing this memory load.
The estimate is smaller than before. At the time when Chrome 63 debuted with site isolation, Google admitted that its use would increase up to 20% of memory usage.
Users will be able to verify that site isolation is enabled. % dropped in the cold as part of Google's efforts to "monitor and improve performance" – in Chrome 68 when it will be launched later this month by typing chrome: // process-internals in the address bar. (This does not work in Chrome 67 or earlier.) Currently, the verification requires more work on the part of the user: it is spelled out in this document under the sub-heading "Check". Computerworld used the latter to make sure that its instances of Chrome had enabled the isolation of the site
[Note:TheisolationofthesiteisactivatedforalloftheinstancesoftheChromememsithe"elementitsisolation"in The chrome settings page: // flags indicates "Disabled". To disable site isolation, users must override the "Disable site isolation test" option with "Disable (not recommended)".]
The isolation of the site site must be included in Chrome 68 for Android, said Reis. More features will also be added to the browser desktop edition. "We are also working on additional security checks in the browser process, which will allow the site's isolation to mitigate not only spectrum attacks, but also attacks from completely compromised rendering processes." he writes. "Stay tuned for an update on these steps of execution."
[ad_2]
Source link