[ad_1]
You may have been advised to "search for the padlock" to warn legitimate e-commerce sites against phishing or malware traps. Unfortunately, this has never been such a useless tip. A new study indicates that half of phishing scams are now hosted on websites whose internet address includes the lock and starts with "https: //".
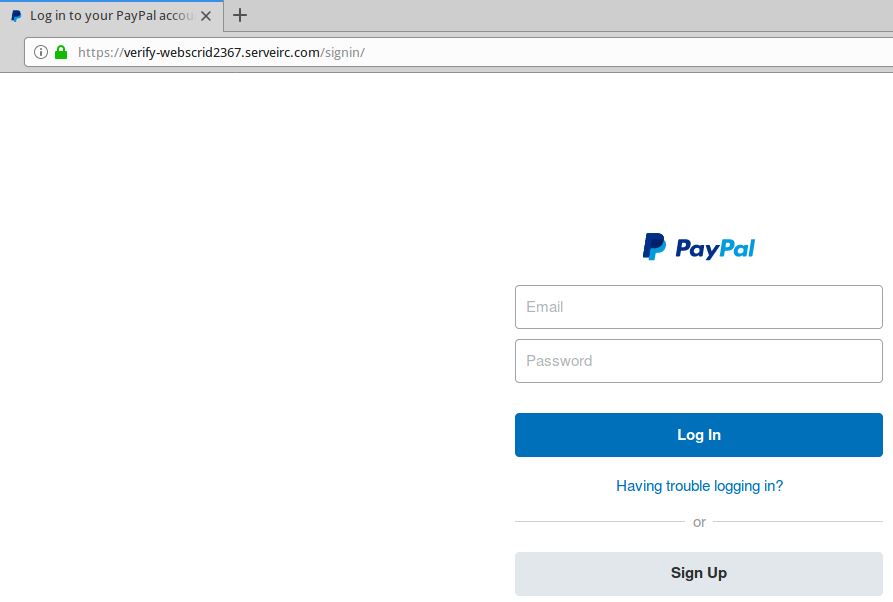
A live Paypal phishing site that uses https: // (has the green padlock).
Recent data from the PhishLabs anti-phishing company show that 49% of all phishing sites in the third quarter of 2018 wore the padlock security icon next to the domain name of the phishing site, such as the phishing site. it appears in the browser's address bar. This is up from 25% a year ago and 35% in the second quarter of 2018.
This alarming change is remarkable because a majority of Internet users took to heart the search tip of the lock "looking for a lock", while associating the lock icon with legitimate sites. A survey conducted by PhishLabs last year revealed that over 80% of respondents thought that the green lock indicated that a website was either legitimate or safe.
In fact, the https: // part of the address (also called "Secure sockets layer" or SSL) simply means that the data exchanged between your browser and the site is encrypted and can not be read by third parties. The presence of the padlock does not mean that the site is legitimate, any more than proof that the site has been protected against the intrusion of hackers.
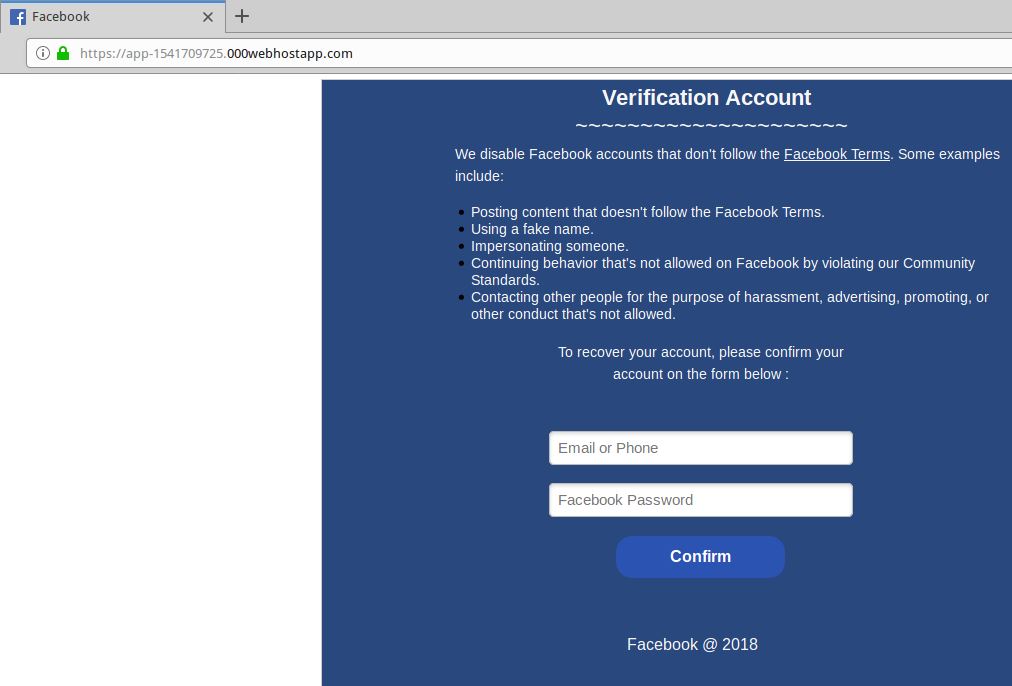
Facebook phishing live using SSL (has the green padlock).
Most of the fight against cybercrime involves defenders who react to the attackers' offensive actions. However, the rapid increase in the adoption of SSL by phishers is a good example in which fraudsters are inspired by legitimate sites.
"PhishLabs thinks this can be attributed to the continued use of SSL certificates by phishers who register their own domain names and create certificates, as well as a general increase in SSL due to the Google Chrome browser." now displaying "Not secure". for websites that do not use SSL, "said John LaCour, technical director of the company. "In the end, the presence or absence of SSL does not tell you anything about the legitimacy of a site."
Leading web browser manufacturers are working with a number of security organizations to index and block new phishing sites, often generating red warning pages that signal the page. a phishing scam and try to dissuade internet users from consulting these sites. But not all phishing scams are reported as quickly.
I spent a few minutes browsing phishtank.com looking for phishing sites using SSL, and I found this cleverly crafted page that tries to phish the credentials of Bibox users, a cryptocurrency exchange. Click on the image below to see if you can see what's going on with this web address:
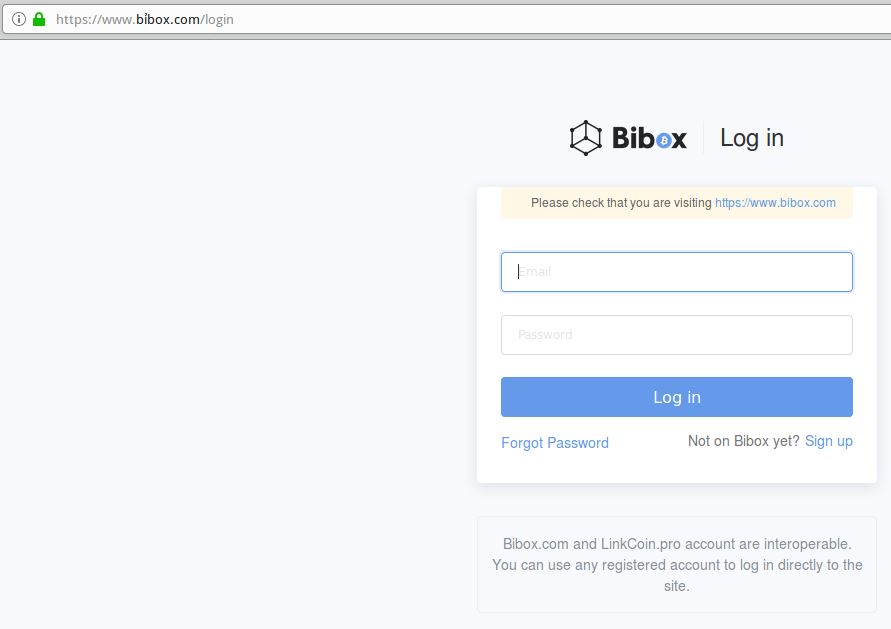
This live phish target users of the Bibox cryptocurrency exchange. Examine the URL carefully in the address bar and you will notice a wavy mark on the "i" in Bibox. This is an internationalized domain name whose actual address is https: //www.xn--bbox-vw5a.[.]com / login
Load the live phishing page at https: //www.xn--bbox-vw5a.[.]com / login (this link has been blocked expressly) in Google Chrome and you will receive a red warning "Deceptive Site in Advance". Load the address above – known as "punycode" – in Mozilla Firefox and the page makes good, at least from this writing.
This phishing site takes advantage of internationalized domain names (IDN) to introduce visual confusion. In this case, the "i" in Bibox.com is translated by the Vietnamese character "", which is extremely difficult to distinguish in a URL bar.
As KrebsOnSecurity noted in March, while Chrome, Safari and recent versions of Microsoft Internet Explorer and Edge browsers make all IDNs in their awkward punycode state, Firefox will gladly convert the code into the likeness domain displayed in the address bar.
If you are a Firefox (or Tor) user and you want Firefox to always display IDNs with their puny equivalent when they are displayed in the browser's address bar, type "about: config" without quotation marks in a Firefox address bar.
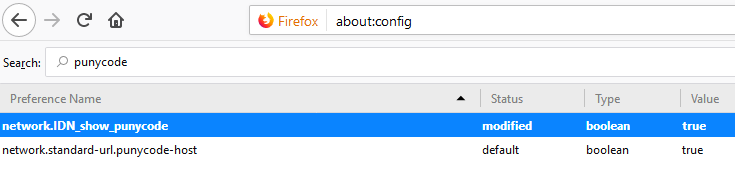
Then, in the "Find:" box, type "punycode" and you should see one or two options. The one you want is called "network.IDN_show_punycode". By default, it is set to "false"; double-clicking on this entry should change this parameter to "true".
Tags: Bibox, IDN, internationalized domain names, John LaCour, phishing, PhishLabs, punycode, SSL
This entry was posted on Monday, November 26th, 2018 at 9h57 and is filed under A Little Sunshine, Latest Warnings.
You can follow the comments of this entry via the RSS 2.0 feed.
You can go to the end and leave a comment. Ping is currently not allowed.
Source link