
[ad_1]
In short: Researchers at Radboud University discovered flaws in some popular Solid State Drive (SSD) disks that allowed them to decrypt hardware encryption without the password. Carlo Meijer and Bernard van Gastel discovered that they could modify the firmware or use debugging tools to modify the password authentication schemes used by readers.
They have successfully tested their exploits on the Crucial MX100, MX200, and MX300 SSDs, as well as Samsung's 840 EVO, 850 EVO, T3 Portable, and T5 Handhelds. The researchers said they were able to reverse engineer these devices and reprogram them to validate the password no matter what was entered.
"We have analyzed the hardware-based encryption of multiple SSDs by reverse engineering their firmware. In theory, the security guarantees offered by hardware encryption are similar or better than those implemented by software. In fact, we found that many hardware implementations had critical security weaknesses. Many models allowed a complete recovery of data without knowing any secrets. "
In addition, since Windows BitLocker software encryption is defaulted to hardware encryption, it can also be ignored using the same methods.
Meijer and van Gastel have discovered three techniques for exploiting these flaws.
With the Crucial MX100, MX200, Samsung 850 EVO and T3 Portable systems, they were able to physically connect to the player's JTAG debug interface and change the password verification controls. Any password entered would decipher the reader.
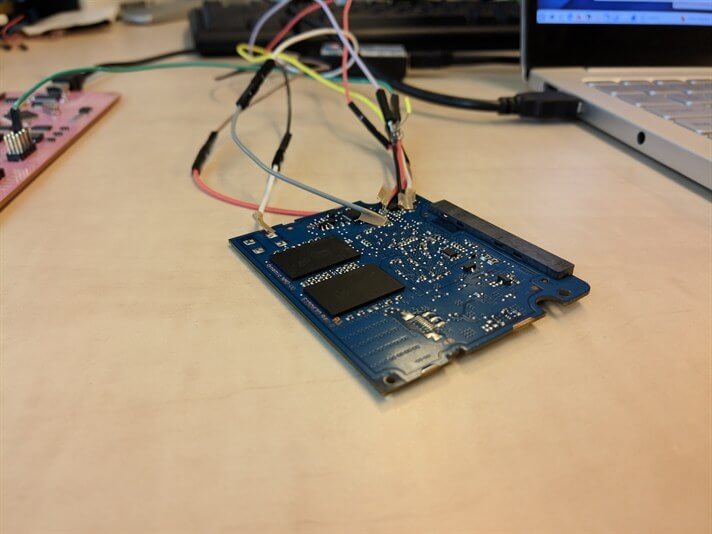
The Crucial MX300 also has a JTAG port, but they discovered that it is disabled by default. Instead, the researchers flashed the reader with counterfeit firmware. This allowed them to authenticate with an empty password field.
With the remaining drives, they were able to recover data encryption keys (DEK) using a feat of "leveling wear".
"Suppose the DEK is stored unprotected, after which a password is set by the end user, thus replacing the unprotected DEK with an encrypted variant," they explain. "Due to wear, the new variant can be stored elsewhere in the storage chip and the old location is marked as unused. If it is not overwritten later by other operations, the unprotected variant of the DEK key can still be retrieved. "
Crucial and Samsung have been informed of the flaw well before announcing it publicly. Crucial has already released corrected firmware for all affected readers. Samsung has also deployed updates for its T3 and T5 portable SSDs. However, for its EVO readers, the company recommends the use of software encryption.
Meijer and van Gastel are preparing to publish an article on loopholes entitled "Automatically Encrypted Disappointment: Solid State Drive (SSD) Encryption Deficiencies". It is currently in the process For details, they made a preliminary copy available for download on the website of Radboud University.
Source link