
[ad_1]

The Ziggy ransomware operation has arrested and released victims’ decryption keys after concerns about recent law enforcement activity and guilt for the encryption victims.
Over the weekend, security researcher Mr. Shahpasandi told BleepingComputer that the administrator of Ziggy Ransomware announced on Telegram that he was shutting down operations and that he would release all decryption keys.
In an interview with BleepingComputer, the ransomware administrator said he created the ransomware to generate money while living in a “third world country”.
After feeling guilty for their actions and concerns regarding recent Emotet and Netwalker ransomware law enforcement operations, the administrator decided to shut down and release all keys.
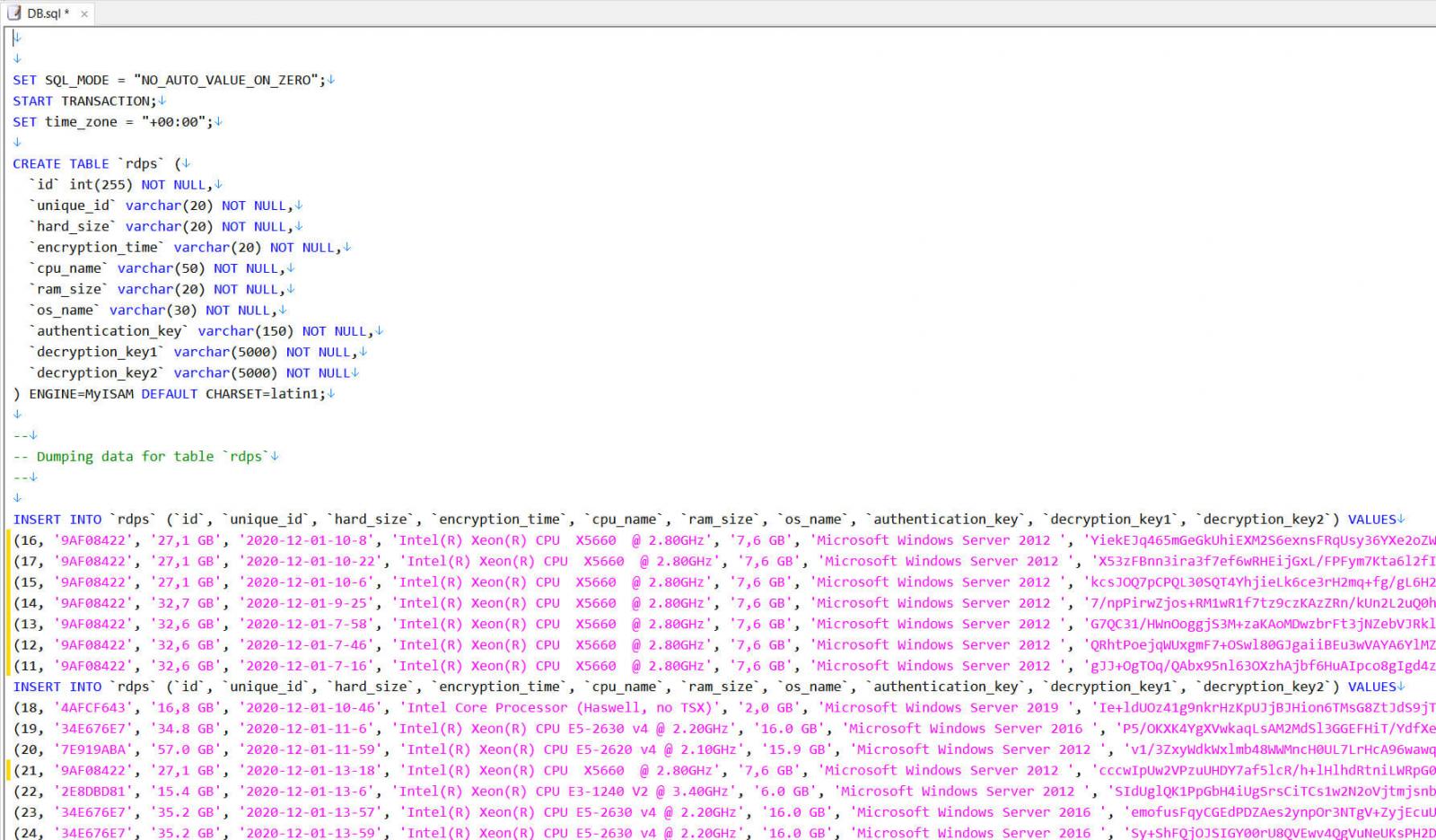
Today, Ziggy ransomware administrator released an SQL file containing 922 decryption keys for the encrypted victims. For each victim, the SQL file lists three keys needed to decrypt their encrypted files.
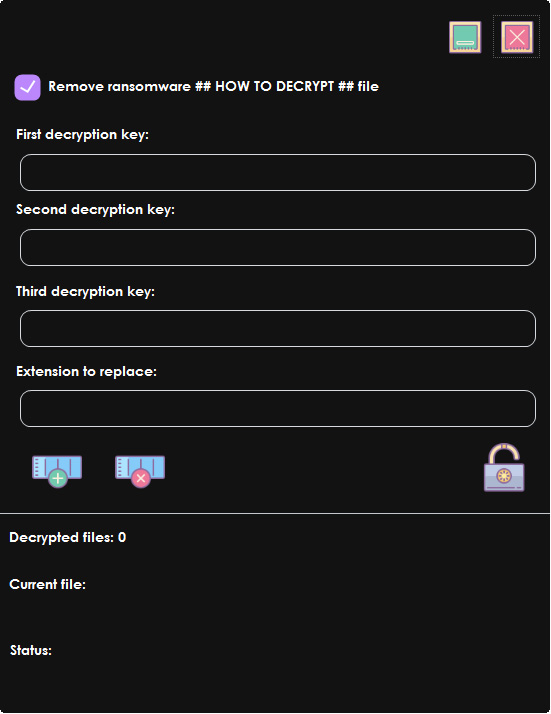
The ransomware administrator also released a decryptor [VirusTotal] that victims can use with the keys listed in the SQL file.
In addition to the decryptor and SQL file, the ransomware administrator shared the source code of another decryptor with BleepingComputer which contains offline decryption keys.
Ransomware infections use offline decryption keys to decrypt infected victims without being connected to the internet or the command and control server was inaccessible.
The ransomware administrator also shared these files with ransomware expert Michael Gillespie who told BleepingComputer that Emsisoft will release a decryptor soon.
“Releasing the keys, whether intentionally or unintentionally, is the best possible outcome. This means that former victims can recover their data without having to pay the ransom or use the developer’s decryptor, which could contain a backdoor and / or bugs. And, of course, that also means there’s one less ransomware bunch to worry about. “
“The recent arrests of individuals associated with Operation Emotet and Netwalker may make some players feel cold-hearted. If so, we may well see more groups cease operations and hand over their keys. Fingers crossed. “Emsisoft’s Brett Callow told BleepingComputer.
Although the ransomware administrator seems honest in their intention to stop and release the keys, BleepingComputer still suggests waiting for a security company’s decryptor rather than using the one provided by the threat actor.
Last week, the Fonix ransomware operation also stopped and released the keys and decryptor. Ziggy’s administrator told BleepingComputer that they are friends with the Fonix ransomware group and are from the same country.
[ad_2]
Source link